ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Nivedita Bisht1, Sapna Singh2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Data security is very important in wireless network and for this cryptography plays a crucial role which means “secret writing”. In Cryptography encryption decryption of data is done by using secret key to provide data confidentiality, data integrity and data authentication. This paper provide a comparative study between various encryption algorithm like AES, DES, RSA and DIFFIE-HELLMAN .Here we compare the different factors of both symmetric key and asymmetric key encryption algorithm
Keywords |
| Cryptography, encryption, symmetric key encryption, asymmetric key encryption. |
INTRODUCTION |
| Cryptography, a word with Greek origins, means “secret writing” is the science of devising methods that allow for information to be sent in a secure form in such a way that the only person able to retrieve this information is the intended recipient. The message to be sent through an unreliable medium is known as plaintext, which is encrypted before sending over the medium. The encrypted message is known as cipher text, which is received at the other end of the medium and decrypted to get back the original plaintext message. Hence a cryptosystem is a collection of algorithms and associated procedures for hiding and revealing information. |
 |
| Cryptography algorithms can be divided into two broad categorizes - Symmetric key cryptography and asymmetric key cryptography. |
II. SYMMETRIC KEY CRYPTOGRAPHY |
| In symmetric key cryptography, same key is shared, i.e. the one key is used in both encryption and decryption, hence also known as single key or secret key encryption. Symmetric key cryptography algorithms are simple requiring lesser execution time. As a consequence, these are commonly used for long messages. There are two types of symmetric key encryption modes one as block ciphers and other as stream ciphers. Block ciphers operate on groups of bits called blocks and each block is processed multiple number of times. The key applied in each round is in a unique manner. A stream cipher operates on one bit at a time i.e. The data is divided as small as single bits and then the encryption is done. In symmetric key encryption the AES algorithm and the DES algorithm different factors are analyzed. |
 |
III. ADVANCED ENCRYPTION STANDARD (AES) ALGORITHM |
| AES is a symmetric key algorithm which operates on two dimensional arrays of bytes known as state and the state consists of four rows of each bytes. AES has key size of 128,192 OR 256 Bits which protect against certain current and future attacks. Hardware and software both implementation are faster and can be implemented on various platforms. |
IV. DATA ENCRYPTION STANDARD (DES) ALGORITHM |
| In asymmetric key cryptography different keys are used for encryption and decryption, hence also known as public key encryption. The two keys are a private key and a public key. The public key is announced to the public; whereas the private key is kept by the receiver. The sender uses the public key of the receiver for encryption and the receiver uses his private key for decryption. Here the number of keys required is small but it is not efficient for long messages. In asymmetric key encryption the RSA algorithm and Diffie-Hellman algorithm different factors are analyzed. |
 |
VI. RIVEST-SHAMIR-ADLEMAN (RSA) ALGORITHM |
| RSA is most widely used public –key algorithm. It provides secrecy and digital signature both. To generate the public and private key it uses a prime number and multiplies larger numbers together. In this it uses two different keys for encryption and decryption. For security purpose its key size should be greater than 1024 bits. |
VII. DIFFIE-HELLMAN (DH) ALGORITHM |
| It is the public key algorithm which uses discrete logarithms in a finite field. It is also known as key exchange algorithm. In this the protocol allows two users to exchange a secret key over an insecure medium without any prior secrets. Hence this algorithm is vulnerable to a Man- in –the- middle attack. When an appropriate mathematical group is used then, only this protocol is considered to be secure. |
VIII. THEORETICAL ANALYSIS OF ENCRYPTION ALGORITHM |
 |
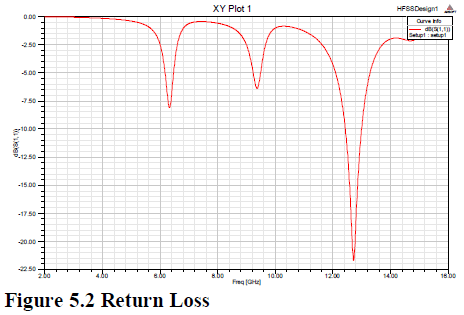
IX. RESULTS |
| Here the study of symmetric and asymmetric key algorithms is done according to different factors. The key used is defined in terms of encryption and decryption either it is same or different. The algorithm used is defined according to its type symmetric or asymmetric. The key length is used according to bit value. The speed is defined in terms of fast or slow. The power consumption takes as low or high. The security is defined as excellent, not secure and least secure. The cost is defined as cheaper or costly. The implementation according to its algorithm used is simple or complex. |
X. CONCLUSION |
| A comparative study of encryption techniques in terms of symmetric key and asymmetric key algorithms analyzed that symmetric key algorithms is viewed to be good in terms of speed and power consumption while asymmetric key algorithms in terms of tunability. In the symmetric key encryption AES algorithm is found to be better in terms of cost, security and implementation. In asymmetric key encryption RSA algorithm is better in terms of speed and security. |