Keywords
|
| Mobile Agent, Wireless Sensor Network, Network Management, e-commerce, Wireless Multimedia Sensors, Grid Services and Grid Computing , Distributed Data Mining, multimedia |
INTRODUCTION
|
| A mobile agent is a node or program as per requirement that once it is launched can move through the network from node to node autonomously performing various tasks. Mobile agents can reduce the bandwidth consumption and path discovery by proceeding the data at the source and sending only the proper results. Peculiarities of a MA are following : autonomous, mobile, perceptive, interactive, goal oriented. As far as mobile agents are concerned in WSNs, they are used to achieve certain intentions, or solve specific issues that are crucial for proper functioning of a WSN. Their mobility is useful for assigned work, which is done on each node. They are goal oriented in the sense that it provides users management of the MAs, once they are set up in the WSN, they perform their respective task on their own, to achieve the specified goal. |
| Technicalities of MAs technology open several feasible target issue which might be efficiently improved in WSNs' application domain. Their intelligence can be applied in many cases. One is the case of a node impairment, or an environmental change that affects a part of several nodes, in a aspect that they react to that change and allow the WSN to function commonly. Routing can be done using MAs, where routes are separately built and maintained by the MAs, who roam free inside a WSN. Mobile Agent can be used for the following reasons [1]: |
| Persistence: When a mobile agent is roams, it is no longer connected to its creator node, and will not be affected if this node fails. |
| Efficiency: If an agent moves through the network to the node where resources inhabit, then the emerging traffic is reduced since it can pre-process data locally and decide what are the most relevant data to be transferred.. |
| Peer to Peer Communication (Peer-to-peer): A failure in the node can be easily identified by the usage of mobile agents. |
LITERATURE REVIEW
|
| 1. Manvi et al. [1] in their paper used mobile agent to find multiple QoS paths and select optimum path among them to increase the network bandwidth and call success ratio. The mobile agent based on-demand quality of service is been compared with that of RSVP-based QoS routing using an internet routing protocol. The system is simulated in various network scenarios to verify performance. One of the most compelling example of mobile agents applications is the management of commercial telecommunication networks |
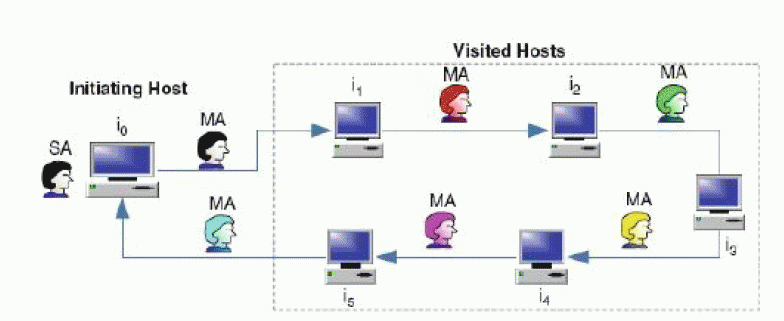
| 2. Al-Jaljouli et al [2] have implemented mobile agent in e-commerce to quest and to refine information of interest from electronic markets. The figure 2 describes the sequence of processes carried out during the agent’s lifetime. They also illustrate about robust security techniques that ensure a sound security of information collected throughout agent’s itinerary against various security attacks, as well as truncation attacks. The authors employ two co-operating agents where the initial verification terms are securely stored within a secondary agent (SA) that endure at the initiator and cooperates with a major agent (MA) that traverses the Internet. |
| 3. Distributed data mining is a elaborate system which is linked on the distribution of resources over the network as well as data mining processes. Moemeng et al. [3] done the survey on the assimilation of distributed data mining and multi-agent system. As open issues and trends, the authors provide context on Research, on software engineering, on Systems and on Users. |
| 4. Shen et al. [4] analyze the strength and instability of mobile agent based middleware. They have suggested mobile agent based publish/subscribe middleware, which enhance the efficiency of transmitting agent by using the publish/subscribe mechanism to build interest route. The experiment results show that their scheme is more adequate of agent’s transmission and it can improve the reliability of the entire application. |
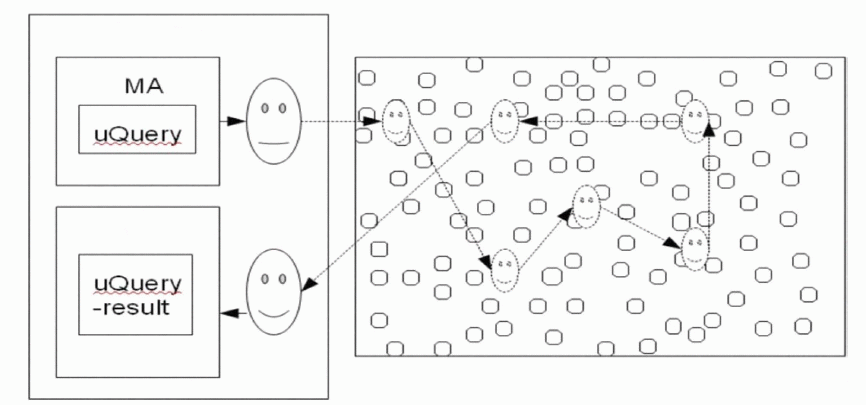
| 5. Research work was done by [Kakkasager], and is carried out in Basaveshwar Engineering College, in 2006, on the subject of increasing the responsiveness of WSNs, with enhancing the query distribution and event responsiveness, using event paths generated by MAs. The main goal of this research is to improve response time for triggering the events, by using the optimal paths from the user interface to the sensor which recognize the event. The essence of this approach is depicted in Figure 2. Optimum paths information is maintained and generated by MAs, which are discovered by local node agent (manager), using their mobility and autonomicity they hop through the network fixing and renovating optimum paths, for message routing . The drawback in this approach is that a lot of MAs are generated to find an optimum path so they don't wander off far away from the event, thereby depleting the nodes' power unnecessarily. Simulation results show that the approach is adequate for real-time event discovery, which proves its idea strength. This drawback can be overthrown by execution of an MA if it wanders off far away from the event node, rather than waiting for it to reach the edge of the WSN [ 5]. |
| 6.As in [6] describes about designing a framework for WSNs, which would maintain the needed security level in WSNs, by using multiple agents. The objective of this research is proposing a security framework for the WSN, which is done by formulating a cross-layer platform with components that allow use of multiple agents both stationary and mobile. Agents are integrated with the code for developing intrusion detection as well as intrusion detected reaction. A special attention has to be given to MA protection and authenticity from being compromised by malicious code. |
| 7. In paper [7] it describes about MA migration during data gathering in WSN's for reducing power consumption and thereby increasing the networks lifetime .The main issue when using multiple MA's is grouping the nodes, so that MA's hoping between the nodes in a group consumes as little energy as possible. This feature is achieved by introducing new agent migration algorithms which produces an agent migration itinerary. Network of WSN nodes is characterised by a totally connected graph, for which a minimum spanning tree is been calculated and appropriate number of agents is generated which is equal to vertices coming out of the root of the spanning tree. Since this algorithm has a fault when MA hops between nodes have smaller weight when compared to hop from the source node, its modification proposes a new algorithm which uses a balancing factor that balances the generated spanning tree in this exceptional case. |
| 8.As in paper [8]data acquisition in clustered WSN's, with the goal of decreasing power consumption and network delay in WSN nodes, by introducing the mobile agent technology. The role of mobile agents is to collect sensor data from all nodes within a cluster and return it to a cluster head node, thereby shrinking power consumption of individual nodes communicating to the head cluster node contribution of the proposed solution is dynamic routing of a mobile agent (MA), while traversing the nodes. The main idea is that when a mobile agent calculates the next hop node, it takes into calculate the path loss, the power consumption of the hop, and the residual energy of other nodes. The solution at hand was justified with experimental results from tests showing that the power consumption and network delay have decreased, opposed to the conventional data gathering. The optimization could save time by not testing all the neighbor nodes, but instead using the first node that satisfies the optimal energy consumption for a hop. |
| 9.Massaguer et al.[9] explains network exploration of WSNs using MA technology. This research addresses the problem of MA generation and routing with the usage of a genetic algorithm. The scheme used in this research is salient, a problem arises when MA has to skip a node in his route, so lost MAs should be taken into consideration. The genetic algorithm is resolved for creating a MA itinerary plan for each agent that is sent to WSN and MA tracking, where each MA itinerary is a route, with the best energy preservation characteristics from the collection point throughout the WSN and back. |
| 10. As in [10] mobile agent data fusion in WSNs is to reduce network communication and thereby decreasing power consumption of the nodes. The idea on which this research is based is discovering the optimal itinerary planning, with no redundant node hoping by the MA, which directly affects power consumption on the nodes. The way of finding the optimal itinerary is the most efficient one regarding the reduction of the power consumption. The idea of the approach is been inspired and shows promise to reduce power consumption. The suggestion of determining the stationary algorithm, because it is computationally complex, could be limiting because of node failure inside the WSN. |
CONCLUSION
|
| All reviewed papers recommend some novel ideas of strengthening WSNs weaknesses using strengths of the MA technology. Some of the papers aspire at replacing the client/server architecture to save power on message transmission. Most of them target power consumption for improvement using the characteristics of the MA while collecting data from the WSN. Others try to continue the performance of the WSN by recommending new frameworks as services to be used in devising new solutions to the existing problems. further developments/trends to emerge in this research area and see the benefits reaped from the ideas of the surveyed papers applied when introducing the MAs in the WSNs. |
ACKNOWLEDGMENT
|
| I would like to thank the almighty for giving me the strength to work on this subject and t hereby coming up with this review paper. I am grateful to my guide and family members for supporting me and praying for me. I would like to express my gratitude towards the professors of Mar Baselios College of Engineering and Technology for their valuable guidance. |
Figures at a glance
|
 |
 |
| Figure 1 |
Figure 2 |
|
| |
References
|
- S.S. Manvi and P. Venkataram, “Mobile agent based approach for QoSrouting,”IETCommun., pp. 430- 439,2007.
- R. Al-Jaljouli, J. Abawajy, “ Agents Based e-Commerce and Securing Exchanged Information,” Pervasive Computing, Springer London, ISBN: 978-1-84882-598-7, pp. 383-404,2009.
- C. Moemeng, V. Gorodetsky, Z. Zuo, Y. Yang, C. Zhang, “Agent-Based Distributed Data Mining: A Survey,” L. Cao (ed.), Data Mining and Multiagent Integration, Springer Science Business Media, LLC 2009.
- Z. Shen, R. LI, J. Luo, Mobile Agent Based Middleware using Publish/Subscribe Mechanism in Wireless Sensor Networks, International Conference on Communication Software and Networks, pp. 111-115,2009.
- Rezavi, R., Mechitov, K., Agha, G., Perrot, J.,"Dynamic Macro programming of Wireless Sensor Networks with Mobile Agents," IEEE Commun. Mag., vol. 46, pp. 50–55,2007.
- Kakkasageri, M.S., Manvi, S.S., Soragavi, G.D., "Mobile agent based event discovery in wireless sensor networks," Proceedings of the 5th WSEAS International Conference on Applied Computer Science, Hangzhou, China, April 16-18, Pages 731-735,2006.
- Chen, M.,Cai, W., Sergio, G., C.M. Leung,"Balanced Itinerary Planning for Multiple Mobile Agents in Wireless Sensor Networks,"inProc. IEEE CCNC 2006, pp. 625-629, Feb. 2006.
- Yuan, L., Wang, X., Gan, 1., Zhao, Y.,"A Data Gathering Algorithm Based on Mobile Agent and Emergent Event Driven in Cluster- Based WSN," JOURNAL OF NETWORKS, VOL. 5, No.10, Pages 1160-1168,October 2010.
- Massaguer, D., Fok, c., Venkatasubramanina, N.,Roman, G., Lu, C.,"Exploring Sensor Networks using Mobile Agents,"AAMAS'06 May 8-12 2006, Hakodate, Hokkaido, Japan, 2006.
- Qi, H., Wang, F.,"Optimal Itinerary Analysis for Mobile Agents in Ad Hoc Wireless Sensor Network,”IEEE Trans. Wireless Commun.,vol. 7, pp. 1326–37 ,April 2008.
|