Index Terms
|
| Cognitive Radio Network, Selfish Attack, COOPON, Markov Chain Model. |
INTRODUCTION
|
| A cognitive radio is an intelligent radio that can be programmed and configured dynamically. Its' transceiver is designed to use the best wireless channels. Such a radio automatically detects available channels in wireless spectrum Depending on transmission and reception parameters; there are two main types of cognitive radio |
| • Full Cognitive Radio: - In which every possible parameter observable by wireless node (or network) is considered. |
| • Spectrum –sensing cognitive Radio:- In which only the radio-frequency spectrum is considered. |
| Licensed-Band Cognitive Radio, capable of using bands assigned to licensed users (except for unlicensed bands, such as the U-NII band or the ISM band. The IEEE 802.22working group is developing a standard for wireless |
| Unlicensed-Band Cognitive Radio, which can only utilize unlicensed parts of the radio frequency (RF) spectrum. One such system is described in the IEEE 802.15Task Group 2 specifications, which focus on the coexistence of IEEE 802.11 and Bluetooth. |
| As wireless communication devices have been tremendously widespread, we have faced excessive spectrum demands and the need to better utilize the available spectrum. In traditional spectrum management, most of the spectrum is allocated to licensed users for exclusive use. CR technology is carried out in two steps. First, it searches for available spectrum bands by a spectrum-sensing technology for unlicensed secondary users (SUs). When the licensed primary user (PU) is not using the spectrum bands, they are considered available. Second, available channels will be allocated to unlicensed SUs by dynamic signal access behavior. Whenever the PU is present in the CR network, the SU will immediately release the licensed bands because the PU has an exclusive privilege to use them CR nodes compete to sense available channels. But some SUs are selfish, and try to occupy all or part of available channels. Usually selfish CR attacks are carried out by sending fake signals or fake channel information. |
SYSTEM DESCRIPTION
|
| A. Existing System |
| Introducing a selfish attack detection technique, COOPON (called Cooperative of Neighboring), for the attack type. We focus on selfish attacks of SUs toward single channel access in cognitive radio networks. COOPON is designed for CR networks with single channels and is designed for the case, that, the channel allocation information is broadcasted for transmission of Primary users. We make use of the decision capability of a communication network based on exchanged channel allocation information among neighboring SUs. |
| B. Proposed System |
| To identify the selfish attack and the rectification of node, we introduce the detection technique of, Markov chain Model. Proposed technique is an intuitive approach and simple to compute, but reliable due to deterministic channel allocation information as well as the support of cooperative neighboring nodes. We focus on, multiple channels and is designed for the case of channel allocation. Node information is broadcast for transmission. We make use of the multiple decision capability of communication network based on exchanging the channel information among the neighboring nodes. |
| C. Attacks and Detection Mechanism |
| 1) Attack Mechanism |
| In a cognitive radio network, the common control channel (CCC) is used to broadcast and exchange managing information and parameters to manage the CR network among secondary users. The CCC is a channel dedicated only for exchanging and managing, information and parameters. A list of current channel allocation information is broadcast to all neighboring SUs. The list contains all other neighboring users’ channel allocation information. A selfish secondary user (SSU) broadcasts separate channel allocation information lists through individual CCC to the left-hand side legal selfish user (LSU) and the right-hand side LSU, respectively. In reality, a list is broadcast once, and it contains the channel allocation information on all of the neighboring nodes. The SU will use the list information distributed through CCC to access channels for transmission. A selfish secondary node will use CCC for selfish attacks by sending fake current channel allocation information to its neighboring SUs |
| When the attackers try to pre-occupy available channels, they will broadcast an inflated larger number of currently used spectrum channels than they actually are. On the other hand, other legitimate SUs are prohibited from using available channel resources or are limited in using them. The selfish SU, or SSU, sends a current fully preoccupied channel list to the right hand side LSU even though it is only occupying three channels. In this case, the right-hand side legitimate SU will be completely prohibited from accessing available channels. Also, the SSU could broadcast a partially pre-occupied channel list even though it actually only uses fewer channels. For instance, the SSU is currently using only three channels, but, broadcasting to the left hand side LSU that it is using four channels. In this case, legitimate SUs can still access one available channel out of five maximum, but are prohibited from using one channel that is actually still available |
| 2) Detection Mechanism |
| Use of Channel Allocation Information. We consider a cognitive radio network, Networks have distributed and autonomous management characteristics. Our proposed detection mechanism in Markov chain is designed for a communication network. We make use of the autonomous decision capability of a communication network based on exchanged multiple channel allocation information among neighboring SUs. The target node, TNode, is also a SU, but other 1-hop neighboring SUs, NNode 1, N-Node 2, N-Node 3, and N-Node 4, will scan any selfish attack of the target node. The target SU and all of its 1-hop neighboring users will exchange the current channel allocation information list via broadcasting on the dedicated channel. We notice that T-Node 2 reports that there are two channels currently in use, while N-Node 3 reports that there are three currently in use, which creates a discrepancy. NNode 4 also receives faked channel allocation information from the target node. On the other hand, all other exchanged information pairs, T-Node/ N-Node 1 and TNode/ N-Node 2, are correct. Thus, all of the 1-hop neighboring SUs will make a decision that the target SU is a selfish attacker. |
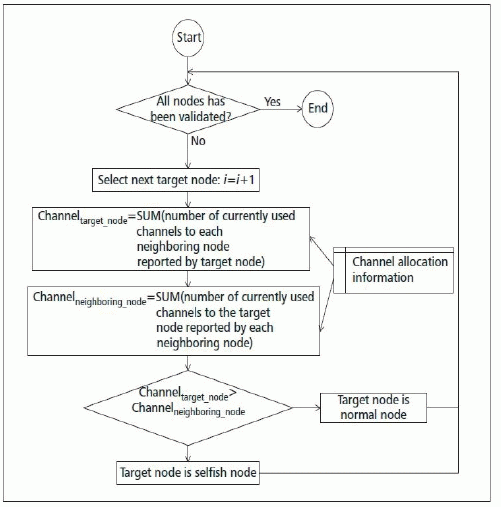
| D. Detection Algorithm |
| Fig.1, shows the Selfish attack detection algorithm flow chart using Markov chain model. As mentioned above all currently used channels in the target node and neighboring nodes are summed up into 2steps channel targets & channel neighbouring will be compared to channel targets & channel neighbouring |
| According to example channel targets & channel neighbouring is 10(4+4+2) and channel targets & channel neighbouring is 5(3+1+1). Because 10 ≠5, the target secondary node is identified as a selfish attacker. Table 1 shows the simulation parameters for the analysis. |
SIMULATION RESULTS AND ANALYSIS
|
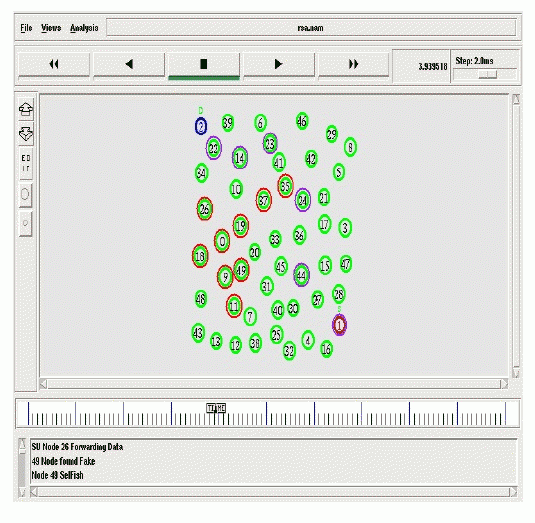
| COOPON identifies the attacks and drops the misbehaving SU’s nodes and use the transmission path with using active nodes and COOPON has single channel transmission path Markov chain model. Fig.2 shows the output of the COOPON with 50 SUs nodes. |
| Fig. 3 shows the Markov chain model output which identifies the attacks of Selfish SU’s nodes and rectifies the selfish SU’s nodes and uses the nodes in the transmission path and Markov chain model has multiple channel transmission paths. |
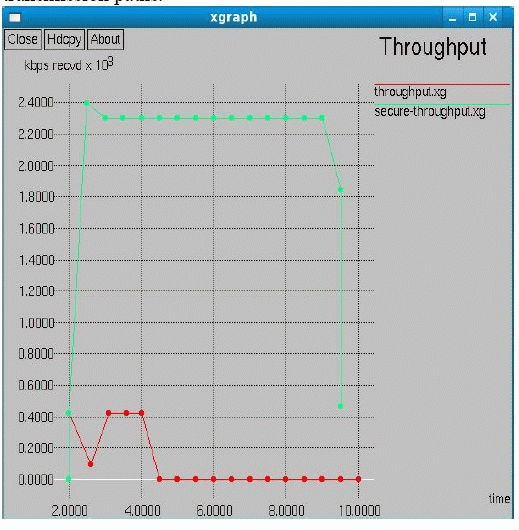
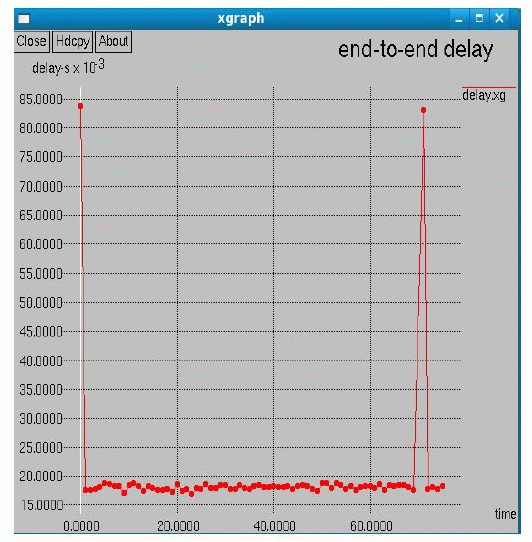
| In the above graph, we shown, the difference between the COOPON technique and Markov chain model technique. X-axis is time and Y-axis is bit rate (kbps) recevied per packets. The red trace indicates the COOPON technique. The Green trace indicates the Markov chain technique. Where, the throughput is very high using the markov chain model Fig. 5 shows the delay of the Cognitive radio Network using Markov chain model and from the graph we can infer, that, the delay of the network reduces with respect to me. |
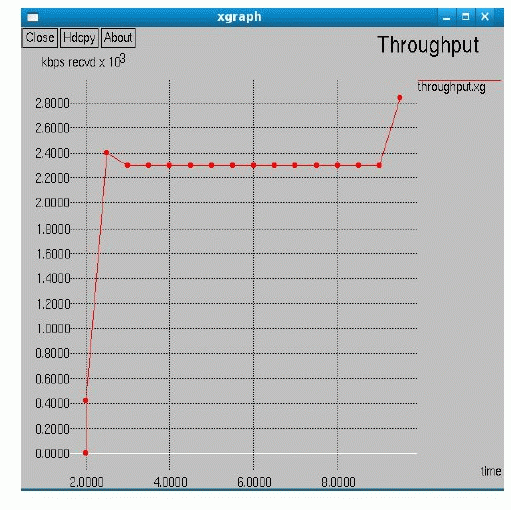
| Fig. 6 shows the throughput of the Cognitive Radio Network with Markov Chain Model and we found that the overall throughput increased Compare to COOPON and it increases the performance of the system. |
CONCLUSION
|
| Hence, we detect the selfish attack at the SU’s and this attacks node were reduced .The transmission path can be constructed through this reduced nodes. Thus Markov chain model provides secure communication to cognitive radio networks. |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
 |
 |
 |
| Figure 4 |
Figure 5 |
Figure 6 |
|
| |
References
|
- ––X. Tan and H. Zhang, “A CORDIC-Jacobi Based SpectrumSensing Algorithm for Cognitive Radio,” KSII Trans. Internetand Info. Systems, vol. 6, no. 9, Sept. 2012, pp. 1998–2016.
- C.-H. Chin, J. G. Kim, and D. Lee, “Stability of Slotted Alohawith Selfish Users under Delay Constraint,” KSII Trans.Internet and Info. Systems, vol. 5, no. 3, Mar. 2011, pp. 542–59.
- S. Li et al., “Location Privacy Preservation in CollaborativeSpectrum Sensing,” IEEE INFOCOM’12, 2012, pp. 729–37.
- Z. Gaoet al., “Security and Privacy of Collaborative SpectrumSensing in Cognitive Radio Networks,” IEEE WirelessCommun., vol. 19, no. 6, 2012, pp. 106–12.
- Z. Dai, J. Liu, and K. Long, “Cooperative Relaying withInterference Cancellation for Secondary Spectrum Access,”KSII Trans. Internet and Information Systems, vol. 6, no. 10,Oct. 2012, pp. 2455–72.
- H. Hu et al., “Optimal Strategies for Cooperative SpectrumSensing in Multiple Cross-over Cognitive Radio Networks,”KSII Trans. Internet and Info. Systems, vol. 6, no. 12, Dec.2012, pp. 3061–80.
- R. Chen, J.-M. Park, and J. H. Reed, “Defense against PrimaryUser Emulation Attacks in Cognitive Radio Networks,” IEEEJSAC, vol. 26, no. 1, Jan. 2008, pp. 25–36.
- M. Yan et al., “Game-Theoretic Approach Against Selfish Attacksin Cognitive Radio Networks,” IEEE/ACIS 10th Int’l. Conf.Computer and Information Science (ICIS), May 2011
- J. Ma , G. Y. Li and Β. Η.Juang "Signal processing incognitive radio", Proc. IEEE, vol. 97, 2009
- Q. Zhao , L. Tong and A. Swami "Decentralized cognitiveMAC for dynamic spectrum access", Proc. IEEE DySPAN, 2005
- C.-K. Yu , K.-C. Chen and S.-M.Cheng "Cognitive radionetwork tomography", IEEE Trans. Veh. Technol., vol. 59, 2010
- F. Digham , M.-S. Alouini and M. K. Simon "On the energydetection of unknown signals over fading channels", IEEETrans. Commun., vol. 55, 2007
- W. Hastings "Monte Carlo sampling methods using Markovchains and their applications", Biometrika, vol. 57, no. 1, 1970
- Simon Haykin, “Cognitive Radio: Brain-Empowered Wire-lessCommunications”, IEEE journal on Selected Areas inCommunications.vol. 23, no. 2, February 2005,pp. 201-220.
- “A Survey of Spectrum Sensing Algorithms for Cognitive RadioApplications”, Communications Surveys & Tutorials, IEEE2009 BY TevfikYucek and Husey in Arslan.
|