Keywords
|
| DWT, ECC, Security, Watermarking |
INTRODUCTION
|
| In the past, people used hidden tattoos or invisible ink to convey steganographic content. In this paper we proposed the various techniques used during cryptographic and steganographic algorithms. The principal operation in elliptic curve cryptographic systems is point multiplication based on Fermat’s little theorem. Basically, Cryptography uses two main styles or forms of encrypting data; symmetrical and asymmetrical. Symmetrical encryptions use the same key for encryption as they do for decryption. While asymmetrical encryptions use the different keys for encryption and decryption. In this paper, a text data is used for cryptography and a more powerful efficient method ECC (elliptic curve cryptography) was used, which is an asymmetrical one employed for encryption and decryption of text message. In this proposed method, the group of points on elliptic curves over finite fields can be used for public-key cryptography. According to [1], the two most common methods used for hiding information inside a picture, audio and video files are LSB (Least Significant Bit) and Injection. In this paper, an image medium was used for Steganography and a more powerful modified DWT (Discrete Wavelet Transform) has been employed for encoding the message into the image file. The Discrete Wavelet Transform, which is based on sub-band coding, is found to be yield a fast computation of wavelet transform. |
| Watermarking technology is used for copyright protection of images, audios and videos. A digital watermark is a piece of information which is a piece of information which is embedded in the digital media and hidden in the digital content in such a way that it cannot be separable from its original data. This piece of information known as watermark, a tag, or a label into multimedia object such that the watermark can be detected or extracted later to make an assertion about the object. The object may be an image, audio, video, or text. |
RELATED WORK
|
| In [2] authors presented a various existing text-based steganography techniques, an overview of text steganography and a brief history of steganography. Also highlighted the problems present in the text steganography and issues with existing solutions. |
| In [3] described the techniques used for cryptography and steganography, and explained the digital watermarking process. Presented the basic types of cryptography ie., symmetrical and asymmetrical and least significant bit approach used in steganography. |
| In [4] presented a data hiding system that is based on audio steganography, and proposed cryptographic technique to secure the data transfer between the source and destination. Audio medium is used and a LSB (least significant bit) algorithm is employed to encode the message inside the audio file. |
| In [9] presented the design of a new high-speed point multiplier for elliptic curve cryptography using either field programmable gate array or application-specified integrated circuit technology. Different levels of digit-serial computation were applied to the data path of Galois field (GF) multiplication and division to explore the resulting performances and find out an optimal digit size. |
| In [11] presented a high speed and efficient pipelined partially serial architecture to enhance the speed and area efficiency. |
PROPOSED SYSTEM
|
| In Cryptographic system we basically used the elliptic curve cryptography (ECC) technique. Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. Elliptic curves are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic curve factorization. The entire security of ECC depends on the ability to compute point-multiplication. The size of the elliptic curve determines the difficulty of the problem. The primary benefit of ECC is a smaller key size, reducing storage and transmission requirements than RSA-based system. For current cryptographic purpose, an elliptic curve is a plane curve which consists of the points satisfying the equation |
 (1) (1) |
| In steganographic system we applying LSB technique during Discrete Wavelet Transform (DWT) on cover image. |
| The following steps are followed in this case:- |
| 1. The image is broken into data units each of them consists of 8x8 block of pixels. |
| 2. Working from top-left to bottom-right of the cover image, DWT is applied to each pixel of each data unit. |
| 3. After applying DWT, one DWT coefficient is generated for each pixel in data unit. |
| 4. Each DWT coefficient is then quantized. |
| 5. The LSB of binary equivalent the quantized DWT coefficient can be replaced by a bit from secret message. |
| 6. Encoding is then applied to each modified quantized DWT coefficient to produce compressed image. When the embedded data’s bits are substituted into the least significant bits (LSB’s) location it will have little no effect on the image appearance to the human eye. |
| Watermarking is used to signify ownership and source authenticity. The aim of watermark is to mark digital data permanently and unalterably, so that the source as well as the intended recipient of the digital work is known. Watermarks can be visible or invisible. In this proposed system, we uses invisible water marking method. Where in invisible watermarks a digital label is used to signify the ownership and authentication. |
METHODOLOGY
|
| Elliptic Curve Cryptography(ECC): |
| Elliptic curve cryptography is gaining popularity because it offers similar security to traditional systems, such as Ron Rivest, Adi Shamir and Leonard Adleman (RSA), but with significantly smaller key lengths. It is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. The ECC method was employed during encryption of text data, the below flow chart shows the steps involved in generating public and private key to encrypt and decrypt the data respectively. |
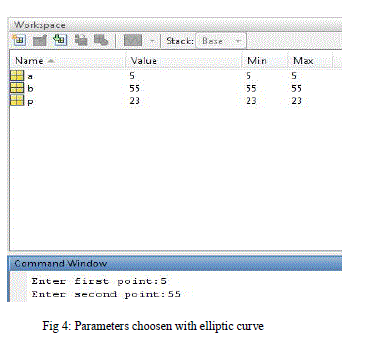
| To use ECC all parties must agree on all the elements defining the elliptic curve, that is, the domain parameters of the scheme. The field is defined by p in the prime case and the pair of m and f in the binary case. The elliptic curve is defined by the constants a and b used in its defining equation. Finally, the cyclic subgroup is defined by its generator point G. For cryptographic application the order of G, that is the smallest value of n such that nG = 0 is a prime number. |
PSEUDO CODE
|
| Step 1: Generate domain parameters. |
| Step 2: Calculate the generator point using eq. (1). |
| Step 3: Generate private key and public key. |
| Step 4: Encode the message to generator point. |
| Step 5: Choose public key to encrypt the message and send as cipher text. |
| Step 6: Use private key to decrypt the cipher text. |
| Step 7: Message in generator point is decoded. |
| Step 8: End. |
SIMULATION RESULT
|
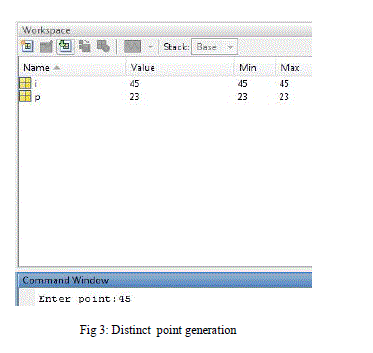
| The proposed system was developed using MAT Lab programming. During execution, the main class displays the following preliminary operations: point addition, point doubling and point multiplication. |
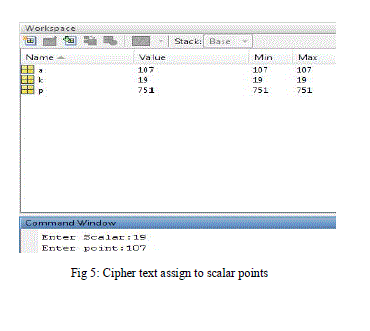
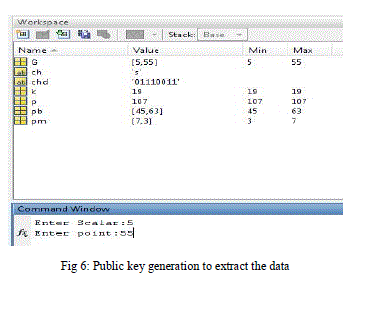
| In fig 3 Point addition uses two distinct points such that to generate slope of line. The Point doubling used in fig 4 is the next step of point addition which determines the point of coordinates to be assign with the elliptic curve. The point multiplication uses both point addition and point doubling. Let P be a point on an elliptic curve. Let k be a scalar that is multiplied with the point P to obtain anther point Q on the curve. i.e. to find Q = kP in fig 5 and generate d binary code for the character ‘S’ and provides the private key to extract the message as shown in fig 6. |
CONCLUSION AND FUTURE WORK
|
| A comparative study from the survey of previous methodologies about the cryptography, steganography and watermarking has been made. High performance architecture for point multiplication, the key operation of ECC, has been proposed. In the next section, we consider the effectiveness of DWT (Discrete Wavelet Transform) employed to encode the message inside the image file and watermarking technology for authenticating. The system therefore, make its security more robust. |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
| |
 |
 |
 |
| Figure 4 |
Figure 5 |
Figure 6 |
|
| |
References
|
- Sridevi R, Damodaram A, and Narasimham S. “Efficient Method of Audio Steganography by Modified LSB Algorithm and Strong Encryption KeyWith Enhanced Security. ” Journal of Theoretical and Applied Information Technology (JATIT), Vol.5, pp.768-771, 2005.
- M.Grace Vennice, Prof.Tv.Rao, M.Swapna and Prof.J.Sasi kiran. “Hiding the text information using Steganography.” International national journalof Engineering Research and Application (IJERA),ISSN: 2248-9622 Vol. 2, Issue-1, jan-Feb 2012, pp.126-131.
- Sarita Poonia, Mamtesh Nokhwal, and Ajay Shankar. “A Secured Image based Steganography and Cryptography with Watermarking”. InternationalJournal of Engineering Science and Engineering (IJESE), Vol.1, pp.66-70, 2013.
- Abikoye Oluwakemi, Adewole Kayode S and Oladipupo Ayotunde J “Efficient Data Hiding System using Cryptography and Steganography”International Journal of Applied Information Systems (IJAIS), Vol.4, pp.6-11, 2012.
- M. Bellare and P. Rogaway. “Optimal Asymmetric Encryption-How To Encrypt With RSA”. International conference on advances in Cryptography-Eurocrypt techniques, Vol.950, pp.92-111, 1995.
- M. Bellare And P. Rogaway. “The Exact Security Of Digital Signatures-How To Sign With RSA and Rabin”. International Conference on Theoryans Application of Cryptographic Techniques, Vol.96, pp.399-416, 1996.
- 7. N .Provos and P. Honeyman, “Hide and Seek: An introduction to Steganography,” IEEE transaction on Security & Privacy Journal, Vol.1, pp.32-44,2003.
- S.Lyu and H.Farid, “Steganography using higher order image statistics,” IEEE Transaction on Information Forensics and Security, Vol.1, pp.111-119, 2006.
- Gustavo D. Sutter, Jean-Pierre Deschamps, and José Luis Imaña “Efficient Elliptic Curve Point Multiplication Using Digit-Serial Binary FieldOperations” IEEE Transactions on Industrial Electronics, Vol. 60, pp.217-225, 2013.
- Reza Azarderakhsh and Koray Karabina “A New Double Point Multiplication Algorithm and its Application to Binary Elliptic Curves withEndomorphisms”. IEEE Transactions on Computers society, Vol.62, pp.1-7, 2013.
- Sugreev Kaur and Rajesh Mehra, “High Speed and Area Efficient 2D DWT Processor Based Image Compression”, Signal and Image Processing: An International Jpournal (SIPIJ), Vol.1, pp.22-31, 2010.
|