Keywords
|
| GSM, RFID, PIC Microcontroller, Security, GSM modem |
INTRODUCTION
|
| The risk of insecure is increasing with increasing populations, as the consequence, large magnitude of hijacks is reported. The major risk faced by the school management as well as the parental side is that the identification of the location of the pupils and their safety measures. The statistical reports perceive that most of the students are hijacked, when they are crossing the school boundary or school entrance area [1-2]. In this respect, the level of security is an important criterion to avoid hijacks that lacks in many of the schools of rural as well as urban areas. Appointing too many security persons or watch guards is not advisable due to high expenditure towards the remedy. The organizations are required a system that ensures each and every movement of the object is monitored and further tracking the system for reasonable distance. |
| Advanced embedded system assisted GSM and RFID based smart school management system is used to give an access for the operation by habitual recognition of the person based upon the RFID tag information. As an example, for entrance control of an organization, the RFID tag and its reader are designed with predefined unique code of tag for individual school student. Whenever the tag is read by reader, it compares the code with the predefined codes in the machine. On the basis of correctness of the information, it sends an acknowledgement (in the form of text message) to the parents of that particular student and the same protocol is followed for all the pupils of the school. |
| Another important feature of the system is that it maintains a record of attendance about the pupil (i.e.) “in time” “out time” which can be further transferred to the administrator via network systems. Through which we can easily compute the attendance status of the students within no time. This machine can also help to avoid human involvement in keeping the attendance record. Thus, reduction of the manpower held in the organization. This machine ensures accurate access control and record keeping. |
DESIGN AND CONSTRUCTION DETAILS
|
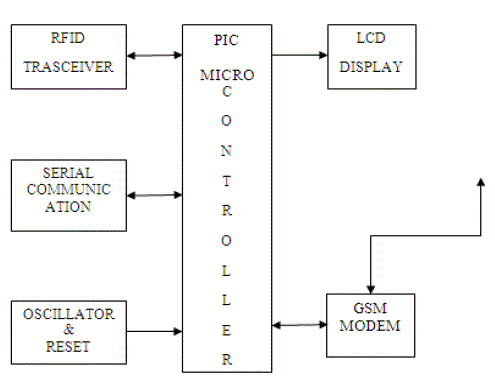
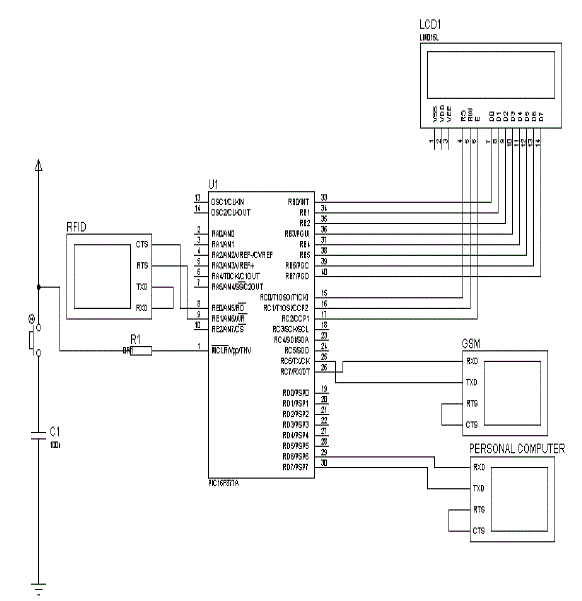
| A. RFID: Many types of RFID exist, but at the highest-level, we can classify RFID devices into two classes namely, active and passive tags. Active tags require power source either connected to powered infrastructure or use energy stored in an integrated battery. In the laterals, tag’s lifetime is limited by stored energy, balanced against the number of read operations. As an example, an active tag is the transponder attached to an aircraft that identify the national origin. The numbers insisted in the tags represent the identification number of the candidate. The RFID utilized in the current system is given below (Figure. 2) |
| B. GSM System: The GSM system has been recognized as a successful cellular phone technology for diverse applications including the ability to roam worldwide with the certainty of being able to operate on GSM networks in exactly the same way. GSM achieved this by the digital TDMA (time division multiple access) approach. By adopting this technique, more users can be accommodated within the available bandwidth. In addition to this, ciphering of the digitally encoded speech is adopted to retain privacy. Using the earlier, it is possible for anyone with aid of scanner receiver to listen the calls and a number. |
| C. GSM network interface: The network structure is defined within the GSM standards. Additionally each interface between the different elements of the GSM network is also defined[11]. This facilitates the information interchanges can take place. It also enables to a large degree that network elements from different manufacturers can be used. However, as many of these interfaces were not fully defined until after many networks had been deployed, the level of standardization may not be quite as high as many people might like. |
| [11]Although the interfaces for the GSM cellular system may not be as rigorously defined as many might like, they do at least provide a large element of the definition required, enabling the functionality of GSM network entities to be defined sufficiently. |
| D. PIC micro controller: PIC 16F77A PIC micro controller is used for this project. The PIC micro controller program reads the data of RFID. The micro controller programming is done using embedded C, a middle level language for control units. The PIC microcontroller 16F877A has an operating speed Max 20 MHZ, voltage (2-5.5v). Memory consists of flash program RAM, EEPROM and data memory. Displayed data of RFID are transferred into RS 232, which is interfaced with microcontroller through MAX232. |
FUNCTIONS
|
| Three students and their respective codes are predefined in the RFID set up and identity tags. Whenever the candidates enter or leave the campus, the LCD will display the status or position of the candidate. In addition, it is also sent a text message as “NAME, IN-TIME” or “NAME, OUT-TIME” to the parent as well as to the school administrative office. Based upon the information given by the designed software interfaced system, the security, attendance, position status of the candidate is monitored. |
RESULTS AND DISCUSSION
|
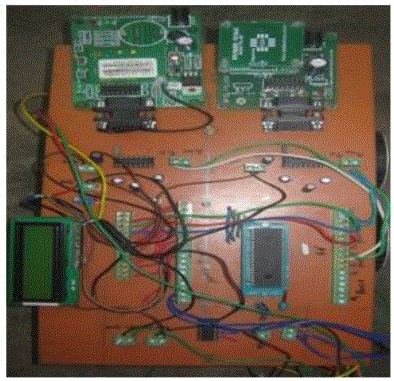
| The RFID and GSM are connected with PIC microcontroller and varying data is sent to GSM modem which is simultaneously displayed in LCD and also send as message both parents and school admin. Through this experiment and implementation we came to know that the student can be monitored using RFID and sent the status as SMS to the particular mobile successfully. RFID assisted GSM based smart school management system can be extended to monitor the objectives and also can be controlled the hijacking further consequences. The system can be controlled and monitored via short message service (SMS) from anywhere that covered by GSM service. |
CONCLUSION
|
| The efficient utilization of the RFID assisted GSM technology is successfully designed and implemented at the laboratory scale. The observations clearly showed that the each and minute movement of the objects can be precisely followed with the help of the presented system. The accuracy and security level may be extended to the public level. Developments in RFID and GSM technology continue to wider reading ranges, yield larger memory capacities, and faster processing as real time system. |
ACKNOWLEDGMENTS
|
| Our thanks to the experts who have contributed towards development of the template, especially my Rajiamma Gomathiamma. |
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
| |
References
|
- AL-Rousan M, AI-Ali A. R, and Darwish K, (2004) “GSM-Based Mobile Tele-Monitoring and Management System for Inter-Cities PublicTransportations”, IEEE International Conference on Industrial Technology (ICIT).
- Manelis V.B, Kaioukov I.V, and Novikov A.V, (2009) “Identification and Analysis of Interference Effects of GSM Base Stations”,CJSCIRKOS, Radioelectronics and Communications Systems, Vol. 52, No. 2, pp. 55-62.
- Mohamed Khalaf-Allah and Kyandoghere Kyamakya () “Mobile Location in GSM Networks using Database Correlation with BayesianEstimation” Proceedings of the 11th IEEE Symposium on Computers and Communications (ISCC'06)0-7695-2588-1/06 $20.00 © 2006 IEEE.
- Ding-Bing Lin, and Rong-Terng Juang, (2005) “Mobile Location Estimation Based on Differences of Signal Attenuations for GSM Systems”,IEEE Transactions On Vehicular Technology, Vol. 54, No. 4,
- M. Shengguang, K.W.Dickson, E.K. Chiu, W. Liu and Q. Li, “Automated management of assets based on RFID triggered alarm messages”
- Baburao Kodavati, Raju, V.K, Srinivasa Rao, S, Prabu, A.V, Appa Rao, T, and Narayana Y.V. “GSM and GPS based vehicle location andTracking system” IJERA Vol. 1 Issue 3, pp.616-625.
- Malik Sikandar Hayat Khiyal, Aihab Khan, and Erum Shehzadi, (2009) “SMS Based Wireless Home Appliance Control System (HACS) forAutomating Appliances and Security”, Informing Science and Information Technology Vol. 6,
- Balaji, R. and Ganesan, R. “Remote Water Pollution Monitoring System Using GSM” International Journal of Computer Science and itsApplications.
- Luca Catarinucci, Riccardo Colella, Alessandra Esposito, Luciano Tarricone and Marco Zappatore, RFID Sensor-Tags Feeding a Context-Aware Rule-Based Healthcare Monitoring System.
- Amit Sachan, (2012) “Microcontroller Based Substation Monitoring and Control System with GSM Modem”, IOSR Journal of Electrical andElectronics Engineering.[11] Google search website.
|