Keywords
|
| Face recognition, Data compression, Face database, CR, BPP. |
INTRODUCTION
|
| Face recognition is a non-intrusive form of identifying a given face image and matching it against a set of faces in the database, in order to validate a person [1]. Today there are a number of face recognition algorithms available and it can be attributed to the rigorous research done in this regard. Even then, face recognition has been an active research domain in computer science. This is due to the fact that the inability or limited functionality of these systems in real time applications. The major reason being the variation in faces due to change in poses [2], age, goggles and other accessories, facial hair, illumination, etc [3]. |
| Data compression is an art of representing data in a compact form, either for storage or for transmission purpose.Understanding the redundancy inherent in the data is crucial for designing effective data compression algorithms. There are basically two types of compression algorithms: Lossy and lossless compression. In lossy compression, some information is usually lost during the compression process. The system discards unimportant data, thereby providing higher compression rates. Whereas in lossless compression, no information is lost during the compression schemes [4-6]. The reconstructed data is identical to the original data in this case [7]. Lossless compression is basically applicable in critical systems like medical image applications, computer programs, etc. |
| The paper aims at effectively using a few of the data compression algorithms for compressing the face images thereby increasing the storage space of the training database. This helps in addition of more images, thereby adding to the efficiency of the face recognition system. |
| The rest of the paper is organized as follows. The related work is given in Section II. Section III deals with the implementation details along with the details of the face database used for the study. The results of the proposed implementation are given in Section IV. The paper concludes in Section V. |
RELATED WORK
|
| Compression of face images in face recognition systems is being effectively deployed these days. A detailed survey of this can be found in [11]. The effects of image compression algorithms in face recognition systems have been studied in [9].The impact of lossy compression techniques on fingerprints and face recognition systems has been assessed in [13]. |
| The techniques used were JPEG, JPEG2000 and WSQ. In [10] an algorithm is devised which works directly with JPEG compressed images by using the DCT features rendered by the JPEG standard. This has also avoided the overhead of decompressing the image before recognition. Currently the shift from 2D images to 3D images to achieve better recognition results has been carried out. The storage of 3D face data requires lots of memory when compared to its 2D counterpart. A method to compress 3D face data and using it for the face recognition purpose has been proposed as in [12]. |
IMPLEMENTATION
|
| Totally 507 face images from the AR face database were taken for the study. The images were arranged with proper labelling and were assessed using Matlab. The details of the face database used in the study are as given below: |
| A. AR Face Database |
| The database was created by Aleix Martinez and Robert Benavente in the Computer Vision Center (CVC) at the U.A.B. in the year 1988. It was the first database to include occlusions. The total number of subjects used here is 126 with 4000 total images. It provides provision for variation in illumination, frontal poses, expression, scarves, eye glasses, etc. [8]. The size of the RGB colour images is 768 × 576 pixels. In a 2-week interval, the subjects face images were captured twice by subjecting them to 13 different conditions. Fig. 1 shows samples taken from the AR Face Database. |
| Each image was compressed using Progressive Coefficients Significance Methods (PCSM), Coefficients Thresholding Methods (CTM-1)and Coefficients Thresholding Methods (CTM-2). The tests used in these categories were: |
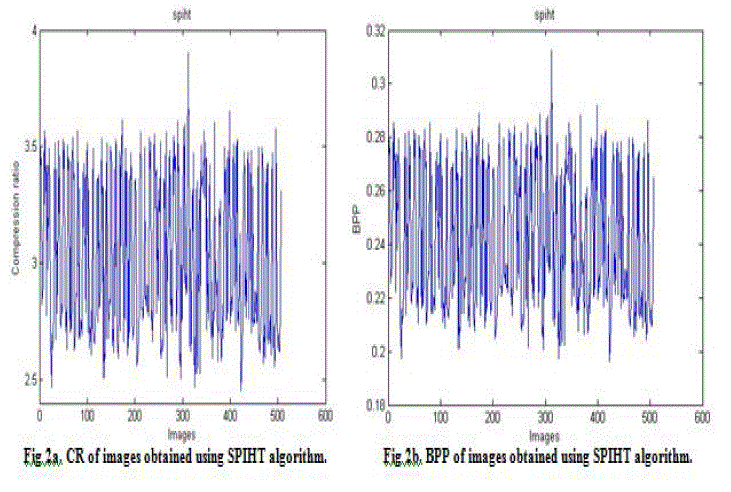
| 1) Set Partitioning In Hierarchical Trees (SPIHT). |
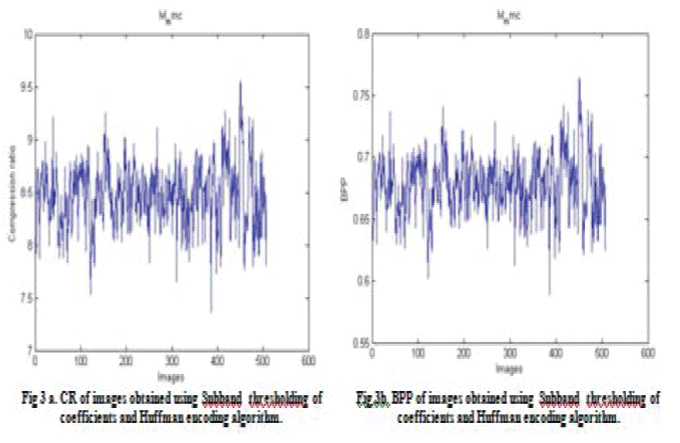
| 2) Subband thresholding of coefficients and Huffman encoding. |
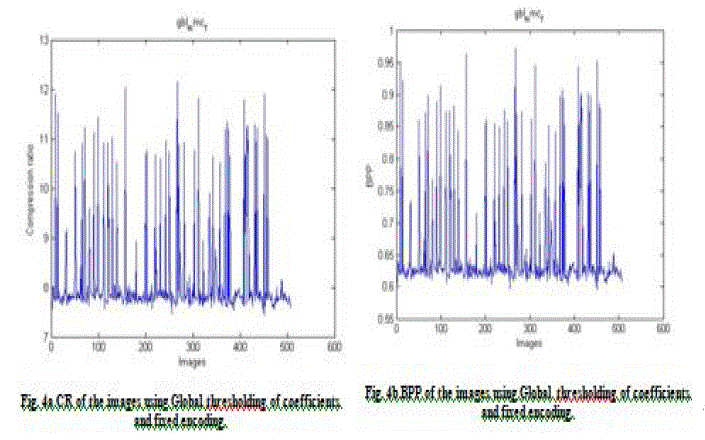
| 3) Global thresholding of coefficients and fixed encoding. |
| 4) Global thresholding of coefficients and Huffman encoding. |
| In all the above cases, the Compression Ratio (CR) and Bits Per Pixel (BPP)were computed. The results are given in the results and discussion section. |
RESULTS AND DISCUSSIONS
|
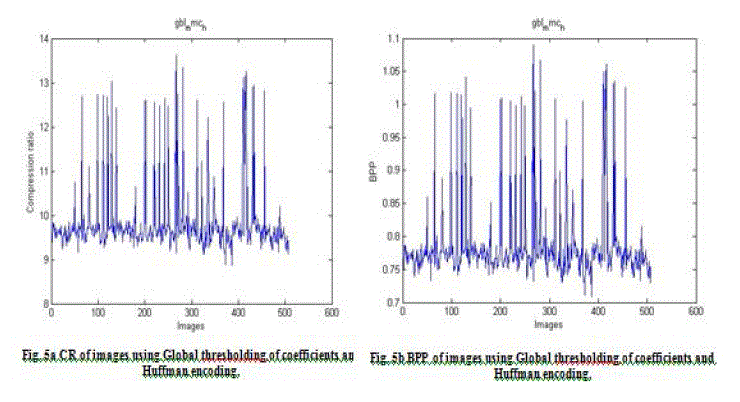
| The values of CR and BPP for the tests conducted on the face images are given through Fig. 2 through 5 respectively. Note that CR indicates that the compressed image is stored using CR % of the initial storage size while BPP is the number of bits used to store one pixel of the image. Figures 2a, 3a, 4a, and 5a depict the compression ratios bestowed by the four algorithms. X axis represents the images and Y axis depicts the compression ratios for the corresponding images. It was found that the compression ratio returned by SPHIT algorithm was better when compared to the other algorithms. Figures 2b, 3b, 4b and 5b depict the Bits Per Pixel (BPP) for the compression algorithms. X axis represents the image numbers and the corresponding BPP returned by the compression algorithms are given along Y axis. It was found that the SPIHT algorithm gave better BPP values when compared to the rest. |
| The paper aims at comparing the efficiencies of different image compression algorithms for using them in face recognition systems. The importance of image compression is stressed so as to facilitate more storage space for newer class of face images in the training database. |
ACKNOWLEDGEMENTS
|
| The authors are immensely grateful to the valuable suggestions and help provided by the Department of Electronics and Communication Engineering, KLE Dr. M.S. Sheshagiri College of Engineering and Technology, Udyambag, Belgaum, Karnataka. |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
| |
References
|
- Xiaozheng Zhang, YongshengGao, “Face recognition across pose: A review”, Pattern Recognition 42 (2009) 2876 – 2896, Elsevier.
- doi: 10.1016/j.patcog.2009.04.017
- RabiaJafri, Hamid R. Arabnia, “A Survey of Face Recognition Techniques”, Journal of Information Processing Systems, Vol.5, No.2, June 2009.
- DOI : 10.3745/JIPS.2009.5.2.041 Sheela Shankar, Dr. V. R Udupi, “A Review on the Challenges Encountered in Biometric Based Authentication Techniques”, Volume 2, Issue 6, June 2014, International Journal of Advance Research in Computer Science and Management Studies (IJARCSMS). ISSN: 2321-7782 (Online).
- R. Sankaralingam, R. Orugani, and N. Touba, “Static compaction techniques to control scan vector power dissipation,” in Proceedings of the IEEE VLSI Test Symposium (VTS '00), pp. 35–40, Montreal, Canada, May 2000.
- Manber, U.; Myers, G. Suffix arrays: A new method for on-line string searches. SIAM J. Comput.1993, 22, 935–948. 2. Larsson, N.J.; Sadakane, K. Faster suffix sorting. Theoret.Comput. Sci. 2007, 317, 258–272.
- CCSDS Secretariat, “Lossless Data Compression”, The Consultative Committee for Space Data Systems.
- Manzini, G.; Ferragina, P. Engineering a lightweight suffix array construction algorithm.Algorithmca 2004, 40, 33–50.
- Available at:http://www2.ece.ohio-state.edu/~aleix/ARdatabase.html
- Delac, Kresimir, MislavGrgic, and Sonja Grgic. "Image compression effects in face recognition systems." Face Recognition (2007): 75-92.
- Eickeler, Stefan, Stefan Muller, and Gerhard Rigoll. "High quality face recognition in JPEG compressed images." In Image Processing, 1999.ICIP 99.Proceedings. 1999 International Conference on, vol. 1, pp. 672-676. IEEE, 1999.
- Delac, Kresimir, Sonja Grgic, and MislavGrgic. "Image Compression in Face Recognition-a Literature Survey." Recent Advances in Face Recognition, edited by: KresimirDelac, MislavGrgic and Marian Stewart Bartlett (2008): 236.
- Chew, Wei Jen, KahPhooiSeng, Wai Chong Chia, Li-MinnAng, and Li Wern Chew. "3D Face Recognition System with Compression."In Proceedings of the International MultiConfer ence of Engineers and Computer Scientists, vol. 1. 2009.
|