ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Mamatha H1, Anitha devi M D2, K B Shiva kumar3 and M Z Kurian4
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
This paper considers a situation where the copyright of distributed images/photos is violated. Since the images/photos published on social networks or any networks are usually modified and/or compressed to the match the template provided by the service providers, this paper propose a digital image watermarking based on DWT coefficients modification to be used for such images/photos. Basically, there are two parts in the image processing, in the embedding process, the blue component of original host image is decomposed by the Discrete Wavelet Transform (DWT). Then image is transmitted. At the receiver end, original components of the watermark image are extracted by using adaptive mean filter.
Keywords |
| Digital watermarking, discrete wavelet transforms, mean filter. |
INTRODUCTION |
| Presently, social networking services, e.g. Facebook, Google+, Instagram and etc., have more influence to our daily life than they did in the past, judged from an on-going increasing number of social network subscribers. Because of attractive features provided for multimedia data, subscribers can simply publish and/or exchange these data. However, multimedia data published in the social networks is easy to be copied and distributed without any permission from the real owner and very difficult to differentiate the copied version from the original one. In order to protect the copyright of the distributed data, digital watermarking techniques have been developed and implemented. Because the images/photos published on them are always changed and/or compress by the uploading process such as JPEG quantization table, pixel resolution and related metadata. Therefore, the digital watermarking techniques developed for social networking services should be robust against image compression attacks. |
| Despite being primarily used to communicate and socialize with friends, the diverse and anonymous nature of social networking websites makes them highly vulnerable to cyber crimes. Publishers, fraudsters, child predators, and other cyber criminals can register to these services with fake identities, hiding their malicious intentions behind innocent appearing profiles. Social networks also encourage the publication of personal data, such as age, gender, habits, whereabouts, and schedules. The wealth of personal information uploaded to these websites makes it possible for cyber criminals to manipulate this information to their advantage and use it to commit criminal acts. Other abusive activities that can be committed on these websites include uploading illegal or inappropriate material, defaming, and stalking (de Paula, 2009). The large number of criminal acts that can be performed through social networks raises the importance of digital forensics in this area. Electronic evidence retrieved from social networking activities on a suspect’s machine can be of great assistance in investigating a criminal case by incriminating or proving the innocence of a suspect. Hussein [8] proposed a digital watermarking method based on log-average luminance. Some 8×8 pixels blocks were chosen and used for watermark embedding if they had a log-average luminance greater than or equal to the log-average luminance of the whole image. |
| This paper proposes a digital image watermarking for social networking services based on DWT coefficients modification. In the embedding process, the blue component of original host image is decomposed by the Discrete Wavelet Transform (DWT) to obtain the coefficients in LL sub-band in order to embed watermark. In the extraction process, original coefficients prediction based on mean filter is used to increase the accuracy of the extracted watermark. The performance obtained from the proposed method. |
LITERATURE SURVEY |
| Jamal a.hussein has proposed a new watermarking scheme on log average luminance. A colored image is divided into blocks after converting the rgb color image into ycbcr color space. To embed the watermark selected blocks are chosen and to extract the watermark, the selected blocks are chosen [1]. |
| Aree ali mohammed has proposed an image watermarking scheme based on multi bands wavelets transformation method. In this work three methods are developed to embed the watermark [2]. |
| Guangyong gao et al., has proposed a new technique based on composite chaos and rmsbm in nsct domain. The watermark is embedded according to the principle of human visual system in nonsubsampled contourlet(NSCT) domain and maximum likehood(ml) detector is used for extraction of watermark [3]. |
| Aleksey kovel et al., has proposed a new method of a pseudo-random pixel rearrangement algorithm based on gaussian integers for image watermarking. It improves the security of most image watermarking techniques [4]. |
| Yuan-hui yu et al., has suggested a steganographic method for embedding a color image in a true color image. Secret data are protected by the conventional crypto system des. This was compared with previous method. The results are improved compare to previous methods [5]. |
| Ali-al-ataby et al., has proposed a method pre-adjusts the original cover image in order to guarantee that the reconstructed pixels from the embedded coefficients wound not exceed its maximum value and hence the message will be correctly recovered [6]. |
| S.a.m.gilani et al., has suggested a novel scheme for watermarking of color images. Color spaces with linear relation to rgb color space with uncorrelated components. Watermark detection is fast and blind [7]. |
| Atallah m. Al-shatnawi has proposed a new method in image steganography with improved image quality. The proposed method hides the secret message based on searching about the identical bits between the secret messages and image pixels values [8]. |
| Komwit surachat has proposed a method for improving the watermark extraction performance of the digital watermarking based on the modification of image pixels. Embedding watermark data with a multiple sections technique in the blue channel [9]. |
| The technique of digital watermarking has always been a topic of great research. The DCT algorithm provides security to the data, but hackers can hack the data from trail, and error method. This paper proposes the one basic technique of digital watermarking by using the wavelets decomposition and mean filter bank. |
PROPOSED METHOD |
| The watermarking algorithm is shown in Fig.1. Consider a cover image and watermark image. The 2D-DWT is applied to cover image as well as watermark image. And only low frequency band (LL) is selected for further processing. |
| The next step is embedded the watermark image into the cover image. Then transmit the watermarked image through communication channel. At the receiver end, receive the watermarked image and extract the watermark image. |
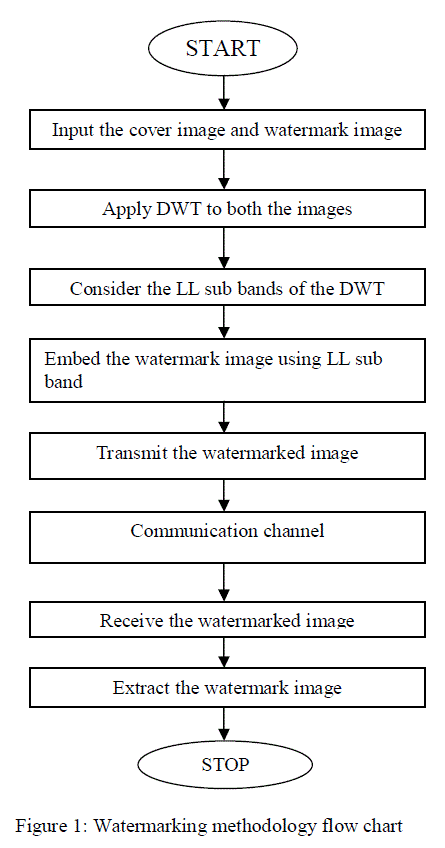 |
IMPLEMENTATION |
| The proposed watermarking method is separated into two processes: |
| Watermark embedding and extraction processes. |
| A. Watermark embedding process: |
| In this process, a black and white logo image (I) with the same size (M×N) as original host image (I) is considered as a watermark logo. It is decomposed by 2D-DWT to obtain four sub-bands. Fig 2 show watermark logo and its sub-bands respectively. |
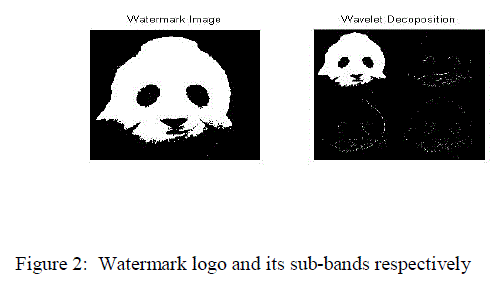 |
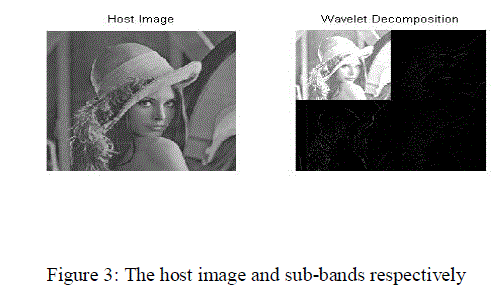
| Figure 3 shows the host image and its sub-bands respectively. Then, the watermark coefficients in LL sub-band whose value can be 0, 1, 1.5, and 2 are selected and converted to two-value coefficients, 1 or 0, as follow. |
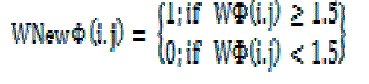 (1) (1) |
 |
| An outstanding property of the Haar functions is that except function haar(0, t), the i–th Haar function can be generated by the restriction of the (j − 1)–th function to be half of the interval where it is different from zero, by multiplication with p2 and scaling over the interval [0, 1] [11]. |
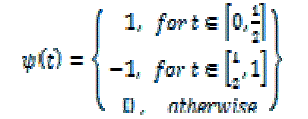 (2) (2) |
| After that WNew Ψ(i,j), is permuted by using Gaussian distribution for spreading the watermark bits pattern, and XORed with a pseudo-random bit stream generated from a key based stream cipher to provide security to finally obtain WE Φ(i,j). The resultant coefficient is converted to 1 and -1 before embedding it to the coefficients in LL sub-band of the original host image, one bit by one coefficient. Figure 4 shows the block diagram of proposed watermark embedding process. |
| The blue component of original host image (B) is decomposed by the 2D-DWT to obtain 4 sub-bands, which are approximation sub-band (BÃÂÃ⢠(i, j)), horizontal sub-band (BH ψ (i, j)), vertical sub-band (BVψ (i,j) ) and diagonal subband ( BD ψ (i, j) ). |
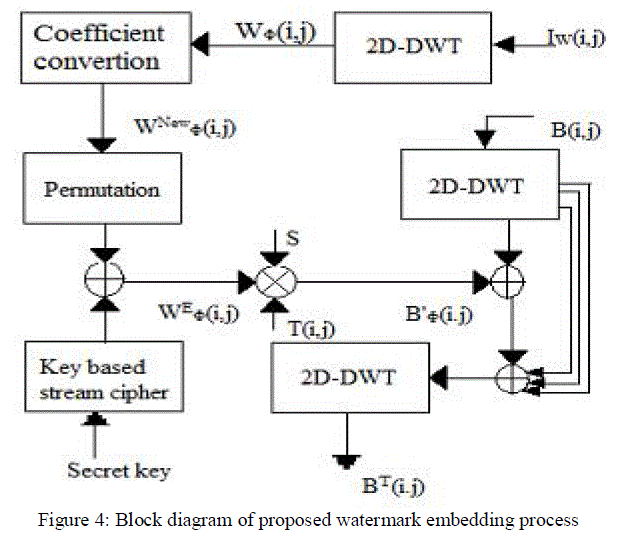 |
| The coefficient in LL sub-band (BÃÂÃ⢠(i,j)) is selected to embed watermark (WEÃÂÃâ¢(i,j)) ) by using equation (2). |
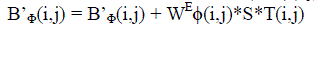 (3) (3) |
| Where B’Φ (i,j) is watermarked coefficient, s is signal strength which is a constant factor used for the entire watermarking area and T (i, j) is the tuned coefficient value for each embedding bit which is derived from resizing the luminance of original host image, |
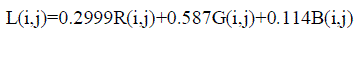 (4) (4) |
| Finally B’Φ(i,j), BH ψ (i, j) , BV ψ (i,j) , and BD ψ (i,j)are inverse transformed by using the 2D-IDWT, and then the result BT (i,j) is combined with original red (R) and green (G) components to construct the watermarked image ( I '). |
CONCLUSION |
| In this paper the digital watermarking method based on DWT coefficients modification for social networking services embedding process has been presented. In the embedding process, the coefficients in LL sub-band were used to embed watermark. In this paper the embedding process is implemented. Future this method can also apply to 3-D images and to the videos. |
References |
|