Keywords |
| Wireless sensor networks, energy conservation, number of reporting nodes, information reliability,
performance analysis |
INTRODUCTION |
| Nowadays, there is a huge increase of handled devices. Laptops, mobile phones and PDAs take an important place in
the everyday life. Hence, the challenge is now to make all these devices communicate together in order to build a
network. Obviously, this kind of networks has to be wireless. Indeed, the wireless topology allows flexibility and
mobility. In this context, the idea of ad hoc networks was developed. our proposal is to limit the reporting tasks of a
detected event to a small subset of sensor nodes in order to save energy consumption while respecting both latency and
reliability constraints. Indeed, by reducing the number of access nodes, significant energy gain can be achieved, thanks
to three enabling factors: First, such a method alleviates the energy wastage by minimizing collisions. . Second, we also
reduce the number of redundant transmitted packets, and hence, more energy is conserved. . Finally, additional nodes
(i.e., the no selected nodes to report the detected event) undergo the sleep state, which reduces the idle listening. We
note that idle listening represents the major source of energy inefficiency, we will show how we can derive the
optimal number of reporting nodes that achieve minimal energy consumption while respecting the latency and
reliability constraints. Such an algorithm runs at the sink level, and it determines dynamically, according to the current
network state, the optimal setting parameters (i.e., the number of active reporting nodes N and the associated required
number of reports to achieve the desired reliability RðNÞ). This information concerning the number of reporting nodes
to be activated is then to be broadcast to all the sensor nodes, which must be able to make use of it in order to regulate
their access. This is typically the role of the MAC protocol. Following this philosophy, the CC-MAC protocol exploits
the information about correlation, sent by the sink node, to select only a small subset of sensor nodes among all the
potential ones to report the detected event. |
| The aim in this case is to suppress the redundant information from being injected into the WSN. The selection
process is achieved based on correlation radius Rcorr, which is calculated at the sink node and indicates the average
distance allowable between selected representative nodes. Note that in our study, a new set of reporting nodes is elected
for each event occurrence, even if the same event occurs again in the same region. As such, the reporting node role
rotates among the sensor nodes within the event area, which allows us to equalize the energy consumption throughout
the network. The operation of the CC-MAC protocol can be described as follows: At the beginning, all the sensor
nodes in the event area contend for the medium access according to the basic IEEE 802.11 DCF protocol, Once a
sensor node accesses the medium by sending correctly a RTS frame, all the other nodes within the Rcorr radius stop
their transmission attempt and undergo the sleep mode. Then, the remaining active nodes try again to access the
medium, and the selection process is executed once more until all the representative nodes are elected. |
| As stated before, communications in current deployed WSN are usually carried using the basic IEEE 802.11 DCF
protocol and its optional RTS/CTS mechanism. Specifically, once an event is detected, the N active reporting nodes
compete to access the common data channel to report the event to the sink. The IEEE 802.11 DCF access method is
based on the CSMA/CA technique. Accordingly, a host wishing to transmit a frame first senses the channel activity
until an idle period equal to a Distributed Inter frame Space (DIFS) is detected. Then, the station waits for a random
back off interval before transmitting. The back off time counter is decremented in terms of time slots, as long as the
channel is sensed free. The counter is suspended once a transmission is detected on the channel. It resumes with the old
remaining back off interval when the channel is sensed idle again for a DIFS period. The station transmits its frame
when the back off time becomes zero. In this case, the host starts the process by sending a RTS frame. If the frame is
correctly received, the receiving host sends a CTS frame after a Short Inter frame Space (SIFS). Once the CTS frame is
received, the sending host transmits its data frame. If the sending host does not receive the CTS frame, a collision is
assumed to have occurred. In this case, the sending host attempts to send the RTS frame again when the channel is free
for a DIFS period augmented by the new backoff. |
SENSOR NODE |
| A sensor node, also known as a 'mote' (chiefly in North America), is a node in a wireless sensor network that is
capable of performing some processing, gathering sensory information and communicating with other connected nodes
in the network. The typical architecture of the sensor node is shown in figure. |
 |
| Components of a Sensor Node |
| The main components of a sensor node as seen from the figure are microcontroller, transceiver, external memory,
power source and one or more sensors. |
Microcontroller |
| Microcontroller performs tasks, processes data and controls the functionality of other components in the sensor node.
Other alternatives that can be used as a controller are: General purpose desktop microprocessor, Digital signal
processors, Field Programmable Gate Array and Application-specific integrated circuit. Microcontrollers are most
suitable choice for sensor node. Each of the four choices has their own advantages and disadvantages. Microcontrollers
are the best choices for embedded systems. Because of their flexibility to connect to other devices, programmable,
power consumption is less, as these devices can go to sleep state and part of controller can be active. In general purpose
microprocessor the power consumption is more than the microcontroller; therefore it is not a suitable choice for sensor
node. Digital Signal Processors are appropriate for broadband wireless communication. But in Wireless Sensor
Networks, the wireless communication should be modest i.e., simpler, easier to process modulation and signal
processing tasks of actual sensing of data is less complicated. Therefore the advantages of DSP’s are not that much of
importance to wireless sensor node. Field Programmable Gate Arrays can be reprogrammed and reconfigured
according to requirements, but it takes time and energy. Therefore FPGA's is not advisable. Application Specific
Integrated Circuits are specialized processors designed for a given application. ASIC's provided the functionality in the
form of hardware, but microcontrollers provide it through software. |
Transceiver |
| Sensor nodes make use of ISM band which gives free radio, huge spectrum allocation and global availability. The
various choices of wireless transmission media are Radio frequency, Optical communication (Laser) and Infrared.
Laser requires less energy, but needs line-of-sight for communication and also sensitive to atmospheric conditions.
Infrared like laser, needs no antenna but is limited in its broadcasting capacity. Radio Frequency (RF) based
communication is the most relevant that fits to most of the WSN applications. WSN’s use the communication
frequencies between about 433 MHz and 2.4 GHz. The functionality of both transmitter and receiver are combined into
a single device know as transceivers are used in sensor nodes. Transceivers lack unique identifier. The operational
states are Transmit, Receive, Idle and Sleep. |
| Current generation radios have a built-in state machines that perform this operation automatically. Radios used in
transceivers operate in four different modes: Transmit, Receive, Idle, and Sleep. Radios operating in Idle mode results
in power consumption, almost equal to power consumed in Receive mode. Thus it is better to completely shutdown the
radios rather than in the Idle mode when it is not Transmitting or Receiving. And also significant amount of power is
consumed when switching from Sleep mode to Transmit mode to transmit a packet.External Memory |
| From an energy perspective, the most relevant kinds of memory are on-chip memory of a microcontroller and
FLASH memory - off-chip RAM is rarely if ever used. Flash memories are used due to its cost and storage capacity.
Memory requirements are very much application dependent. Two categories of memory based on the purpose of
storage a) User memory used for storing application related or personal data. b) Program memory used for
programming the device. This memory also contains identification data of the device if any. |
Power Source |
| Power consumption in the sensor node is for the Sensing, Communication and Data Processing. More energy is
required for data communication in sensor node. Energy expenditure is less for sensing and data processing. The
energy cost of transmitting 1 Kb a distance of 100 m is approximately the same as that for the executing 3 million
instructions by 100 million instructions per second/W processor. Power is stored either in Batteries or Capacitors.
Batteries are the main source of power supply for sensor nodes. Namely two types of batteries used are chargeable and
non-rechargeable. They are also classified according to electrochemical material used for electrode such as
NiCd(nickel-cadmium), NiZn(nickel-zinc), Nimh (nickel metal hydride), and Lithium-Ion. Current sensors are
developed which are able to renew their energy from solar, thermo generator, or vibration energy. Two major power
saving policies used are Dynamic Power Management (DPM) and Dynamic Voltage Scaling. DPM takes care of
shutting down parts of sensor node which are not currently used or active. DVS scheme varies the power levels
depending on the non-deterministic workload. By varying the voltage along with the frequency, it is possible to obtain
quadratic reduction in power consumption. |
Sensors |
| Sensors are hardware devices that produce measurable response to a change in a physical condition like temperature
and pressure. Sensors sense or measure physical data of the area to be monitored. The continual analog signal sensed
by the sensors is digitized by an Analog-to-digital converter and sent to controllers for further processing.
Characteristics and requirements of Sensor node should be small size, consume extremely low energy, operate in high
volumetric densities, are autonomous and operate unattended, and be adaptive to the environment. As wireless sensor
nodes are micro-electronic sensor device, can only be equipped with a limited power source of less than 0.5 Ah and 1.2
V. Sensors are classified into three categories. |
| • Passive, Omni Directional Sensors: Passive sensors sense the data without actually manipulating the
environment by active probing. They are self powered i.e energy is needed only to amplify their analog signal. There is
no notion of “direction” involved in these measurements. |
| • Passive, narrow-beam sensors: These sensors are passive but they have well-defined notion of direction of
measurement. Typical example is ‘camera’. |
| • Active Sensors: This group of sensors actively probes the environment, for example, a sonar or radar sensor or
some type of seismic sensor, which generate shock waves by small explosions. |
| The overall theoretical work on WSN’s considers Passive, Omni directional sensors. Each sensor node has a certain
area of coverage for which it can reliably and accurately report the particular quantity that it is observing. Several
sources of power consumption in sensors are a) Signal sampling and conversion of physical signals to electrical ones,
b) signal conditioning, and c) analog-to-digital conversion. Spatial density of sensor nodes in the field may be as high
as 20 nodes/ m3. |
PROTOCOL IMPLEMENTATION |
| Sensor nodes in order to save energy consumption while respecting both latency and reliability constraints. Indeed,
by reducing the number of access nodes, significant energy gain can be achieved, thanks to three enabling factors: First,
such a method alleviates the energy wastage by minimizing collisions. . Second, we also reduce the number of
redundant transmitted packets, and hence, more energy is conserved. . Finally, additional nodes (i.e., the non selected
nodes to report the detected event) undergo the sleep state, which reduces the idle listening. We note that idle listening
represents the major source of energy inefficiency; we will show how we can derive the optimal number of reporting
nodes that achieve minimal energy consumption while respecting the latency and reliability constraints. Such an
algorithm runs at the sink level, and it determines dynamically, according to the current network state, the optimal
setting parameters (i.e., the number of active reporting nodes N and the associated required number of reports to
achieve the desired reliability RðNÞ). |
| This information concerning the number of reporting nodes to be activated is then to be broadcast to all the sensor
nodes, which must be able to make use of it in order to regulate their access. This is typically the role of the MAC
protocol. Following this philosophy, the CC-MAC protocol exploits the information about correlation, sent by the sink
node, to select only a small subset of sensor nodes among all the potential ones to report the detected event. |
| The aim in this case is to suppress the redundant information from being injected into the WSN. The selection
process is achieved based on correlation radius Rcorr, which is calculated at the sink node and indicates the average
distance allowable between selected representative nodes. Note that in our study, a new set of reporting nodes is elected
for each event occurrence, even if the same event occurs again in the same region. As such, the reporting node role rotates among the sensor nodes within the event area, which allows us to equalize the energy consumption throughout
the network.The operation of the CC-MAC protocol can be described as follows: At the beginning, all the sensor nodes
in the event area contend for the medium access according to the basic IEEE 802.11 DCF protocol,Once a sensor node
accesses the medium by sending correctly a RTS frame, all the other nodes within the Rcorr radius stop their
transmission attempt and undergo the sleep mode. Then, the remaining active nodes try again to access the medium,
and the selection process is executed once more until all the representative nodes are elected. |
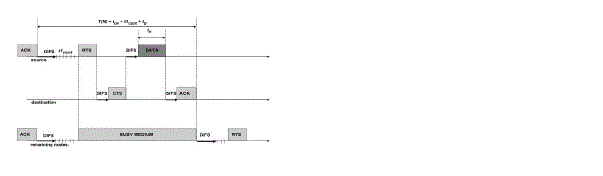
| As stated before, communications in current deployed WSN are usually carried using the basic IEEE 802.11 DCF
protocol and its optional RTS/CTS mechanism. Specifically, once an event is detected, the N active reporting nodes
compete to access the common data channel to report the event to the sink. |
| The IEEE 802.11 DCF access method is based on the CSMA/CA technique. Accordingly, a host wishing to transmit
a frame first senses the channel activity until an idle period equal to a Distributed Inter frame Space (DIFS) is detected.
Then, the station waits for a random backoff interval before transmitting. The backoff time counter is decremented in
terms of time slots, as long as the channel is sensed free. The counter is suspended once a transmission is detected on
the channel. It resumes with the old remaining backoff interval when the channel is sensed idle again for a DIFS period.
The station transmits its frame when the backoff time becomes zero. In this case, the host starts the process by sending
a RTS frame. If the frame is correctly received, the receiving host sends a CTS frame after a Short Inter frame Space
(SIFS). Once the CTS frame is received, the sending host transmits its data frame. If the sending host does not receive
the CTS frame, a collision is assumed to have occurred. In this case, the sending host attempts to send the RTS frame
again when the channel is free for a DIFS period augmented by the new backoff, Successful transmission from the first
attempt. We propose the spatial Correlation-based Collaborative MAC (CC-MAC) protocol that aims to
collaboratively regulate sensor node transmissions. It follows from our earlier discussion in Section III that the
distortion constraint can be achieved even though the number of nodes sending information about an event is
decreased. Furthermore, by intelligently selecting the locations of representative nodes, the distortion DE(M) can be
further reduced. |
 |
| In order resides at the sink, determines the correlation radius, rcorr for a distortion constraint, Dmax, as explained in
Section IV. This information is then broadcast to each sensor node during the network setup. The CC-MAC protocol,
which is implemented at each sensor node, then performs MAC distributively. CC-MAC exploits spatial correlation in
the MAC layer by using the correlation radius, rcorr, to suppress the redundant information from being injected into the
WSN. We now present the principles of CC-MAC protocol in detail. When a specific source node, ni, transmits its
event record to the sink, all of its correlation neighbors have redundant information with respect to the distortion
constraint, Dmax. This redundant information, if sent, increases the overall latency and contention within the
correlation region, as well as wasting scarce WSN energy resources. Our proposed spatial Correlation-based
Collaborative MAC (CC-MAC) protocol aims to prevent the transmission of such redundant information and in
addition, prioritize the forwarding of filtered data to the sink. In WSN, the sensor nodes have the dual functionality of
being both data originators and data routers. Hence, the medium access is performed for two reasons: |
| • Source Function: Source nodes with event information perform medium access in order to transmit their packets to
the sink. |
| • Router Function: Sensor nodes perform medium access in order to forward the packets received from other nodes
to the next destination in the multi-hop path to the sink. |
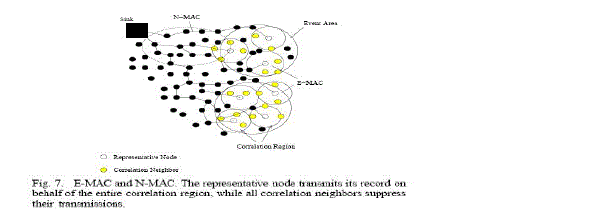
| In order to address these two different contention attempts in WSN, our spatial Correlation-based Collaborative
MAC (CCMAC) protocol contains two components corresponding to the source and router functionalities. Event MAC
(E-MAC), filters out the correlated records and Network MAC (N-MAC) ensures prioritization of route-thru packets.
More specifically, a node performs E-MAC when it wants to transmit its sensor reading to the sink, while N-MAC is
performed when a node receives a packet and tries to forward it to the next hop. A typical WSN with the E-MAC and
N-MAC application areas are shown in |
 |
| Since centralized medium access is not preferred in WSN, we use a distributed protocol to determine the
representative nodes. Both E-MAC and N-MAC use a CSMA/CA based medium access control with appropriate
modifications and enhancements. The information about correlation formation is embedded inside the
RTS/CTS/DATA/ACK packets. Each node is informed about the correlation information about a node using these
packets. As a result, additional signalling is not required for our CC-MAC protocol. We explain the packet structure
and the principles of both E-MAC and N-MAC in the following sub-sections. |
| A.Event MAC (E-MAC) |
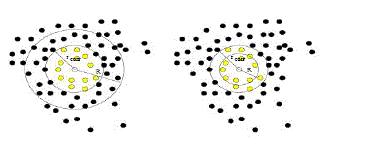
| The Event MAC (E-MAC) protocol aims to filter out correlated event information by forming correlation regions
based on the correlation radius, rcorr, in each correlation region; a single representative sensor node transmits data for a
specific duration, while all other nodes stop their transmission attempts. After each transmission duration a new
representative node is selected as a result of the contention protocol. All sensor nodes contend for the medium for the
first time so that the representative nodes are selected by the help of the spatialreuse property of the wireless channel.
This initial phase is called as the first contention phase and is explained as follows. |
| B.Network MAC (N-MAC) |
| As a node records an event and transmits its packets using E-MAC, these packets are forwarded through the
network by intermediate nodes which perform the router functionality. In addition, node deployment over large sensor
fields may have to deal with multiple concurrent events. Hence, when a packet is routed to the sink, it may traverse
through nodes corresponding to other concurrent events. However, since the correlation has already been filtered out
using E-MAC, the route-thru packet must be given priority over the packets generated by another concurrent event.
This is the reason why we need a Network MAC (N-MAC) component. When an intermediate node receives a DATA
packet, it performs N-MAC to further forward that packet to the next hop. The route-thru packet is given precedence in
two phases. When a correlation neighbor receives an RTS regarding a route-thru packet during the random listening
period of the SSS, it switches from SSS to receive state and receives the packet. During the transmission, the
representative node defers its transmission and the route-thru packet is received by the correlation neighbor. In order to
further exploit the higher priority of the routethru packet, we use a priority scheme similar to that in IEEE 802.11 Point
Coordinate Function (PCF). |
 |
| A node in a correlation region with a route-thru packet listens to the channel for PCF Inter Frame Space (PIFS) time
units, which is smaller than the DCF Inter Frame Space (DIFS) used by the nodes performing E-MAC. The router
node, then, sets its backoff window size to a random number which is between [0, CWmax − 1], where CW max is a
value smaller than the actual CWmax used by the representative node. Such a principle increases the probability that
the router node captures the channel since the router node begins backoff before the representative node of the
correlation region. As a result, the route-thru packet is given precedence. Since backoff procedure is still used, the
collision between multiple route-thru packets that may be in the same correlation region is prevented. If, on the other
hand, the representative node receives the routethru packet, it simply gives precedence to the route-thru packet over its
generated packet and forwards the route-thru packet. |
| C. AOMDV Protocol |
| When a source has data to transmit to an unknown destination,it broadcasts a Route Request (RREQ) for that
destination . At each intermediate node, when a RREQ is received a route to the source is created. If the receiving node
has not received this RREQ before, is not the destination and does not have a current route to the destination, it
rebroadcasts the RREQ. If the receiving node is the destination or has a current route to the destination, it generates a
Route Reply (RREP). The RREP is unicast in a hop-byhop fashion to the source. As the RREP propagates, each
intermediate node creates a route to the destination. When the source receives the RREP, it records the route to the
destination and can begin sending data. If multiple RREPs are received by the source, the route with the shortest hop
count is chosen. As data _ows from the source to the destination, each node along the route updates the timers
associated with the routes to the source and destination, maintaining the routes in the routing table. |
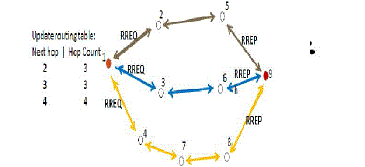 |
| Figure AOMDV in NS2 |
IMPLEMENTATION ENVIRONMENT |
| Network simulator 2 is used as the simulation tool in this project. NS was chosen as the simulator partly because of
the range of features it provides and partly because it has an open source code that can be modified and extended. There
are different versions of NS and the latest version is ns-2.1b9a while ns-2.1b10 is under development. |
| Network Imulator (Ns) |
| Network simulator (NS) is an object–oriented, discrete event simulator for networking research. NS provides
substantial support for simulation of TCP, routing and multicast protocols over wired and wireless networks. The
simulator is a result of an ongoing effort of research and developed. Even though there is a considerable confidence in
NS, it is not a polished product yet and bugs are being discovered and corrected continuously. |
| NS is written in C++, with an OTcl1 interpreter as a command and configuration interface. The C++ part, which is
fast to run but slower to change, is used for detailed protocol implementation. The OTcl part, on the other hand, which
runs much slower but can be changed very quickly, is used for simulation configuration. One of the advantages of this
split-language program approach is that it allows for fast generation of large scenarios. To simply use the simulator, it
is sufficient to know OTcl. On the other hand, one disadvantage is that modifying and extending the simulator requires
programming and debugging in both languages. |
| NS can simulate the following: |
| 1.Topology: Wired, wireless |
| 2. Sheduling Algorithms: RED, Drop Tail, |
| 3. Transport Protocols: TCP, UDP |
| 4. Routing: Static and dynamic routing |
| 5. Application: FTP, Telnet, Traffic generators. |
CONCLUSIONS |
| The spatial Correlation-based Collaborative MAC (CCMAC) protocol proposed in this work is designed for
distributed implementation and has two components: Event MAC (E-MAC) that filters out the correlation in source
records and Network MAC (N-MAC) that prioritizes the transmission of route-thru packets over other packets. Routethru
packets are representative of an entire correlation region and hence given higher priority on their way to the sink.
Using simulations, the performance of the CC-MAC protocol is investigated and significant performance gains in terms
of energy consumption, latency and packet drop rate are shown. Our work shows that, by exploiting spatial correlation,
the transmission of redundant nodes can be controlled. Moreover, controlling the transmission of sensor nodes has also
been investigated in the application layer in terms of topology control these protocols focus on connectivity of the
network and the traffic properties of the generated traffic, CC-MAC provides a localized control based on the spatial
correlation in the physical phenomenon. |
| |
References |
- I. Akiyldiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci, âÃâ¬ÃÅA Survey on Sensor Networks,âÃâ¬Ã IEEE Comm. Magazine, vol. 40, no. 8, pp. 102-114, Aug. 2002.
- S. Singh and C.S. Raghavendra, âÃâ¬ÃÅPAMAS: Power Aware Multi-Access Protocol with Signaling for Ad Hoc Networks,âÃâ¬Ã ACM Computer Comm. Rev., pp. 5-26, July 1998.
- F. Dai and J. Wu, âÃâ¬ÃÅDistributed Dominant Pruning in Ad Hoc Wireless Networks,âÃâ¬Ã Proc. IEEE IntâÃâ¬Ãâ¢l Conf. Comm. (ICC âÃâ¬Ãâ¢03),May 2003.
- M. Miller and N. Vaidya, âÃâ¬ÃÅA MAC Protocol to Reduce Sensor Network Energy Consumption Using a Wake-Up Radio,âÃâ¬Ã IEEE Trans. Mobile Computing, vol. 4, no. 3, pp. 228-242, May/June 2005.
- W. Ye, J. Heidemann, and D. Estrin, âÃâ¬ÃÅMedium Access Control with Coordinated Adaptive Sleeping for Wireless Sensor Networks,âÃâ¬Ã IEEE/ACM Trans. Networking, vol. 12, no. 3,pp. 493-506, June 2004.
- T. van Dam and K. Langendoen, âÃâ¬ÃÅAn Adaptive Energy-Efficient MAC Protocol for Wireless Sensor Networks,âÃâ¬Ã Proc.ACM First IntâÃâ¬Ãâ¢l Conf. Embedded Networked Sensor Systems(SenSys âÃâ¬Ãâ¢03), pp. 171-180, Nov. 2003.
- R.C. Shah and H.M. Rabaey, âÃâ¬ÃÅEnergy-Aware Routing for Low Energy Ad Hoc Sensor Networks,âÃâ¬Ã Proc. Second IEEE WirelessComm. and Networking Conf. (WCNC âÃâ¬Ãâ¢02), Mar. 2002.
- J. Chang and L. Tassiulas, âÃâ¬ÃÅMaximum Lifetime Routing in Wireless Sensor Networks,âÃâ¬Ã IEEE/ACM Trans. Networking, vol. 12, no. 4, pp. 609-619, Aug. 2004.
- S. Tilak, B. Abu-Ghazaleh, and W. Heinzelman, âÃâ¬ÃÅInfrastructure Tradeoffs for Sensor Networks,âÃâ¬Ã Proc. First ACM Workshop Wireless Sensor Networks and Applications (WSNA âÃâ¬Ãâ¢02), pp. 49-58,Sept. 2002.
- O.B. Akan and I.F. Akyildiz, âÃâ¬ÃÅEvent-to-Sink Reliable Transport forWireless Sensor Networks,âÃâ¬Ã IEEE/ACM Trans. Networking, vol. 13,no. 5, pp. 1003-1016, Oct. 2005.
- C.F. Chiasserini and M. Garetto, âÃâ¬ÃÅAn Analytical Model for Wireless Sensor Networks with Sleeping Nodes,âÃâ¬Ã IEEE Trans.Mobile Computing, vol. 5, no. 12, pp. 1706-1718, Dec. 2006.
|