Keywords |
| Networking, Network Mobile Computing, Wireless Network, Wireless Mesh Network(WMN) |
INTRODUCTION |
| Network Mobile data communication has become a very important and rapidly evolving technology as it allows
users to transmit data from remote locations to other remote or fixed locations. This proves to be the solution to the biggest
problem of business people on the move with mobility. Mobile computing is human computer interaction by which a
computer is expected to be transported during normal usage. Mobile computing involves mobile communication, mobile
hardware and mobile software. |
| Mobile software deals with the characteristics and requirements of mobile applications. Data connections used in
mobile computing take three general forms so. Cellular data service uses technologies such as GSM, CDMA or GPRS.
These networks are usually available within range of commercial cell towers. Wi-Fi connections offer higher performance
may be either on a private business network or accessed through public hotspots, and have a typical range of 100 feet
indoors and up to 1000 feet outdoors. Satellite Internet access covers areas where cellular and Wi-Fi are not available and
may be set up anywhere the user has a line of sight to the satellite's location, which for satellites in geostationary orbit
means having an unobstructed view of the southern sky. Some enterprise deployments combine networks from multiple
cellular networks or use a mix of cellular, Wi-Fi and satellite. When using a mix of networks, a mobile virtual private network (mobile VPN) not only handles the security concerns, but also performs the multiple network logins automatically
and keeps the application connections alive to prevent crashes or data loss during network transitions or coverage loss. |
| A wireless network is a computer network that uses a wireless network connection such as a cell phone network,
Wi-Fi local network or a terrestrial microwave network. Wireless networking is a method by which homes,
telecommunications networks and enterprise (business) installations avoid the costly process of introducing cables into a
building, or as a connection between various equipment locations. Wireless telecommunications networks are generally
implemented and administered using radio communication. This implementation takes place at the physical level (layer) of
the OSI model network structure. Mesh networking is a type of network topology where each node must not only capture
and disseminate its own data, but also serve as a relay for other nodes, that is, it must collaborate to propagate the data in
the network. A mesh network can be designed using a flooding technique or a routing technique. When using a routing
technique, the message is propagated along a path, by hopping from node to node until the destination is reached. To ensure
all its paths' availability, a routing network must allow for continuous connections and reconfiguration around broken or
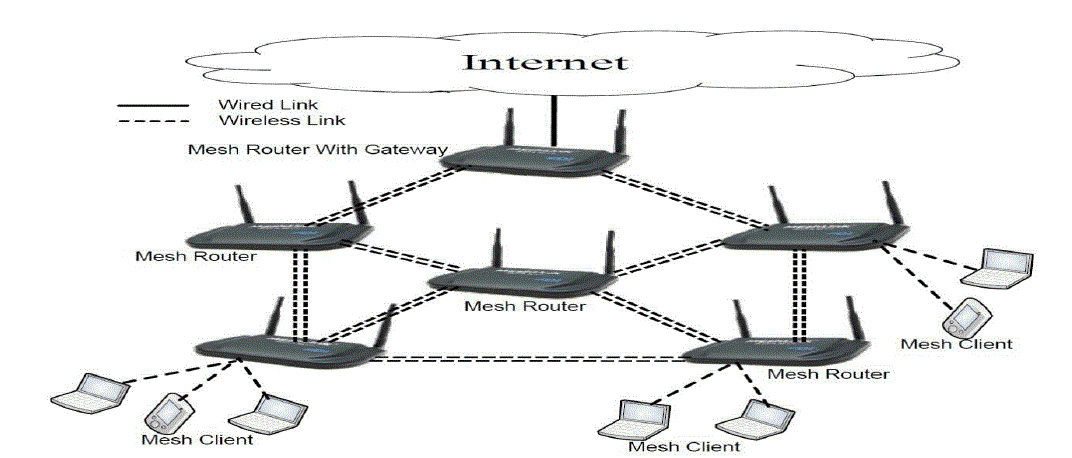
blocked paths, using self-healing algorithms. A WMN consists of two types of nodes, namely, mesh routers (MRs) that
have minimal mobility, and mesh clients (MCs) that may be highly mobile. Each WMN has one or more gateways that are
special MRs connected to the Internet. |
ARCHITECTURAL DESIGN |
| Mesh networking is a type of network topology where each node must not only capture and disseminate its own
data, but also serve as a relay for other nodes, that is, it must collaborate to propagate the data in the network. A mesh
network can be designed using a flooding technique or a routing technique. When using a routing technique, the message is
propagated along a path, by hopping from node to node until the destination is reached. To ensure all its paths' availability,
a routing network must allow for continuous connections and reconfiguration around broken or blocked paths, using selfhealing
algorithm. |
| A wireless mesh network (WMN) is a mesh network created through the connection of wireless access points
installed at each network user's location. Each network user is also a provider, forwarding data to the next node. The
networking infrastructure is decentralized and simplified because each node need only transmit as far as the next node.
Wireless mesh networking could allow people living in remote areas and small businesses operating in rural neighbor hoods
to connect their networks together for affordable Internet connections. |
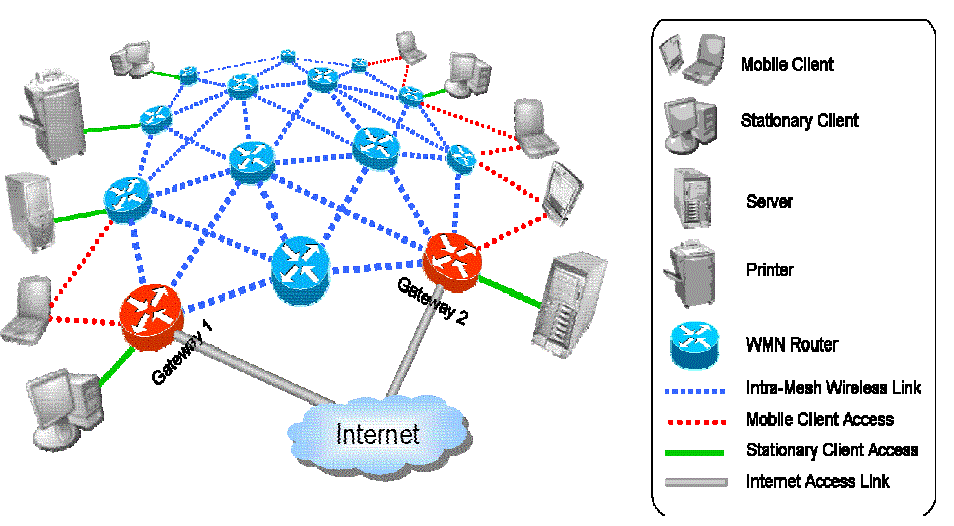
| Multiple gateways connecting the wireless mesh network to the internet. Each gateway covers a zone of the
wireless mesh network and maintains a location database for mobile clients with in the zone. For each mobile client, there
exists an entry in the location database recording its current location information, which is the address of its forwarding
chain head, i.e., the first mobile router on the chain. Routing-based location management scheme with pointer forwarding
for wireless mesh network. The mobile clients on changing the residing mobile router will be updated for non-interrupting
its data communication over the Network..Anchor mesh router of a mobile client may be co located with its current serving
mobile router. |
| The zones covered by the different gateways do not overlap with each other, such that at any time, the location
information of any mobile client is kept in the location database of the gateway with in which it reside. Two mobile client
changes can be notified and data is forwarded without updating its route but the third change will be updated for new route
calculations. For data transfers simulations, a wireless multicast network is setup with this. A mobile client connected with
the mobile router can set up and propagate its own multicast services. The other mobile client’s on the same mobile router
can get the multicast broadcast data. |
| In this proposed system use a parameter called the service to mobility ratio (SMR) of each mobile client to depict the
mobile client’s mobility and service characteristics. The physical meaning of mobility rate is the number of serving mobile
router changes per time unit. A mobile client can dynamically monitor the packet arrival rate by counting the number of
data packets arrived in a time interval and calculating the average number of data packets arrived per time unit. Also an
mobile client can dynamically count the number of serving mobile router changes in a time interval and calculate the
average number of serving mobile router changes per time unit to obtain the mobility rate. Internet traffic is the traffic
between mobile routers and the gateway, dominates peer-to-peer traffic in wireless mesh networks because wireless mesh
networks are expected mainly to be a solution for providing last-mile broadband Internet access. |
| This proposed system is making use of the Kurskal algorithm. Kurskal algorithm is used to find out the shortest path.
Due to this mesh clients can easily identify the shortest path easily. As a result uninterrupted data communication over the
network. Also this proposed system incurs low signaling cost for more number of mobile clients. In this system searching
of the particular path is relatively easy. The searched path is indicated by using the color code. |
DATA COMMUNICATION |
| The proposed location management scheme, namely location management mesh, the protocol behavior when an
mobile client is within a gateway zone, the protocol behavior when an mobile client moves from one gateway zone to
another. Propose efficient mobility management schemes based on pointer forwarding for wireless mesh networks (WMNs)
with the objective to reduce the overall network traffic incurred by mobility management and packet delivery. The
proposed schemes are per-user-based, i.e., the optimal threshold of the forwarding chain length that minimizes the overall
network traffic is dynamically determined for each individual mobile user, based on the user's specific mobility and service
patterns. This paper develops analytical models based on stochastic Petri nets to evaluate the performance of the proposed
schemes. This paper demonstrates that there exists an optimal threshold of the forwarding chain length, given a set of
parameters characterizing the specific mobility and service patterns of a mobile user. Also demonstrate that our schemes
yield significantly better performance than schemes that apply a static threshold to all mobile users. A comparative analysis
shows that our pointer forwarding schemes outperform routing-based mobility management protocols for WMNs,
especially for mobile Internet applications characterized by large traffic asymmetry for which the downlink packet arrival
rate is much higher than the uplink packet arrival rate. The SPN model captures the dynamic service and mobility behavior
of a mobile client using states and events. Proposed system choose SPN as the tool for performance modeling because: SPN
model is a concise representation of the underlying Markov or semi-Markov chain that may have a large number of states.
Also SPN model is capable of reasoning the behaviour of mobile client, as it migrates among states in response to system
events. At last SPN model consists of entities such as transitions (e.g., Move and Forward), tokens, places (e.g., Movement
and FL), and arcs that connect transitions and places. |
| This paper helps in setting up the simulator to plot the Wireless Sensor Nodes in the plotting area. The nodes can
be either mesh routers (MR) responsible for routing the data to the clients or mesh clients (MC) responsible for sending and
receiving data the mesh nodes in the wireless mesh network is either router or client. The Mesh nodes can be a real time
object in the drawing canvas to denote the actual working of the Wireless Sensor Network. The nodes can be added and
labeled on mouse events and then the route will be formed dynamically. The routing path can be generated by applying the
Kruskal algorithm, considering the nodes and vertices. |
RESULT ANALYSIS |
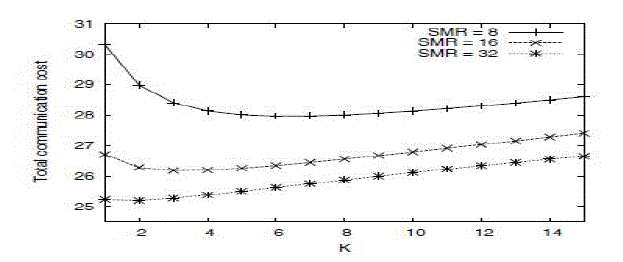
| A.Cost vs. K under the hexagonal network coverage model |
| In this compare the tunnel based scheme, Routing based scheme, pointer forwarding ,location management mesh
with k(function)along the X-axis and Total communication cost. Compared to these four schemes location management
mesh yields the best performance. In location management mesh as the k, increases total communication cost will be
decreases. Figure illustrates location management mesh as a function of K, under the hexagonal network coverage model. It
can be observed that cost curves shown in this figure exhibit high similarity in shape. |
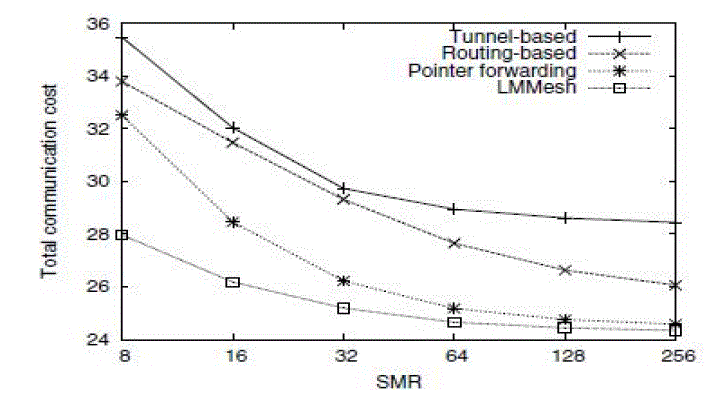
| B. Performance comparison: cost vs. SMR under the hexagonal network |
| In this compare the tunnel based scheme, Routing based scheme, pointer forwarding, location management mesh with
service to mobility ratio along the X-axis and Total communication cost. Compared to these four schemes location
management mesh yields the best performance. In location management mesh as the service to mobility ratio, increases total communication cost will be decreases. Based on these observations, we can draw the conclusion that analytical results
obtained are valid and are not sensitive to the network coverage model. |
CONCLUSIONS |
| As the popularity of the wireless network increases also its diversity. Location management is essential for any wireless
network. Many of the location management schemes exist for the wireless mesh network. Tunnel-based schemes explicitly
register or update their location information to some centralized location server. Routing based schemes find their shortest
neighbour for routing the packets to destinations. Due to this the routing table needs to be updated for every location
changes in the wireless mesh network. This incurs high signaling cost for more number of mobile clients. This research is
to provide the un-interrupted data communication to the mobile client. This proposed system is make use of the Kurskal
algorithm. Kurskal algorithm is used to find out the shortest path. Due to this mesh clients can easily identify the shortest
path easily. As a result uninterrupted data communication over the network. Also this proposed system incurs low signaling
cost for more number of mobile clients. In this system searching of the particular path is relatively easy. The searched path
is indicated by using the color code. |
Figures at a glance |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References |
- F. Akyildiz, X. Wang, and W. Wang, “Wireless mesh networks: asurvey,” Computer Networks, vol. 47, no. 4, pp. 445–487, Mar. 2005.
- Akyildiz, J. McNair, J. Ho, H. Uzunalioglu, and W. Wang, “Mobility management in next-generation wireless systems,” Proc. IEEE, vol. 87,no. 8,pp. 1347–1384, 1999.
- Akyildiz, J. Xie, and S. Mohanty, “A survey of mobility managementin next-generation all-IP-based wireless systems,” IEEE WirelessCommun.,vol. 11, no. 4, pp. 16–28, 2004.
- E. Perera, V. Sivaraman, and A. Seneviratne, “Survey on network kmobility support,” ACM SIGMOBILE Mobile Computing and Commun.Rev., vol. 8,no. 2, pp. 7–19, Apr. 2004.
- D. Saha, A. Mukherjee, I. S. Misra, and M. Chakraborty, “Mobility support in IP: a survey of related protocols,” IEEE Network, vol. 18,no. 6, pp. 34–40, 2004.
- M. Viswanathan, et al., “Performance analysis of dynamic mobilitymanagement for proxy mobile IPv6 networks,” in Proc. 2011 Int. Conf.onUbiquitous Information Management and Communication, pp. 1–6.
- H. Zhou, et al., “A proxy mobile IPv6 based global mobility management architecture and protocol,” Mobile Networks and Applications,vol. 15, no. 4,pp. 530–542, Aug. 2010.
- H. Luo, H. Zhang, Y. Qin, and V. C. M. Leung, “An approach forbuilding scalable proxy mobile IPv6 domains,” IEEE Trans. Networkand Service Management, vol. 8, no. 3, pp. 176–189, 2011.
- N.Kara,“Mobility management approaches for mobile IP networks:performancecomparison and use recommendations,” IEEE Trans. Mobile Comput.,vol. 8, no. 10, pp. 1312–1325, 2009.
- I.R. Chen, W. He, and B. Gu, “DMAP: integrated mobility and service management in mobile IPv6 systems,” Wireless Personal Commun.,vol. 43,no. 2, pp. 711–723, 2007.
- R. Chen, W. He, and B. Gu, “Proxy-based regional registration for integrated mobility and service management fornetwork cost minimizatioin mobile IP systems,” The Computer J., vol. 50, no. 3, pp. 281–293, 2007.
- E. Fogelstroem, A. Jonsson, and C. Perkins, “Mobile IPv4 regionalregistration,” RFC 4857, June 2007.
- H. Soliman , C. Castelluccia, K. El Malki, and L. Bellier, “Hierarchicalmobile IPv6 mobility management (HMIPv6),” RFC 4140, Aug. 2005.
- Misra, et al., “IDMP-based fast handoffs and paging in IP-based 4G mobile networks,” IEEE Commun. Mag., vol. 40, no. 3, pp. 138–145,Mar.2002.
- R. Chen, B. Gu, and S. T. Cheng, “On integrated location and servicehandoff schemes for reducing network cost in personalcommunicationsystems,” IEEE Trans. Mobile Comput., vol. 5, no. 2, pp. 179–192, 2006.
- R. Chen, T. M. Chen, and C. Lee, “Performance evaluation offorwarding strategies for location management in mobile networks,” TheComputer J.,vol. 41, no. 4, pp. 243–253, 1998.
- Z. Ye and A. A. Abouzeid, “Optimal stochastic location updates inmobile ad hoc networks,” IEEE Trans. Mobile Comput., vol. 10, no. 5,pp. 638–652, 2011.
|