ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
P. Sathyabama Gayathri1, J. Angela Jennifa Sujana2 and T.Revathi3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
In Cloud Computing, Storage –as –a -Service is one of the most wanted services, but the security of the data stored in the cloud using these services is the key issue. The outsourced data in the cloud has to be guaranteed with confidentiality, integrity and access control. In this work, we device a mechanism of cloud data storage based on indirect mutual trust between the Cloud Service Provider (CSP) and the cloud users through Trusted Third Party Auditor (TTPA). This work facilitates the user to store their data as blocks and enables them to perform dynamic operations on blocks. The stored data can be accessed by a group of users authorized by the data owner. The owner has the privilege to grant or revoke access of the stored data in the cloud. The present system is providing a good security mechanism for stored data and proper sharing of keys among authorized users, and data owner for the cryptographic mechanism.
Keywords |
| Mutual trust, access control, dynamic environment, outsourcing data storage |
INTRODUCTION |
| Cloud computing[1] is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. |
| In this Information age, several organizations posses huge amount of data which needs to be kept secured. These data includes personal information, health information and financial data. Local maintenance of such Storage as a Service to alleviate the burden of huge local data storage and to reduce the cost by means of outsourcing data storage to the cloud. Since the data owner outsources their sensitive data to the cloud, they want their data to be guaranteed with some security concerns like confidentiality, integrity and proper access control. In some practical applications data confidentiality is not only a security concern but also a juristic issue. For example in e-Health applications in USA the usage and exposure of data should satisfy the policies confessed by Health Insurance Portability and Accountability Act (HIPAA) [2], thus keeping the privacy of the outsourced data on the cloud is not an option, but it is a demand. Confidentiality can be guaranteed by encrypting the data before outsourcing it to the remote server. Also the outsourced data should not be modified by unauthorized users. Traditional access control techniques assume that the data owner and the storage servers in the same trust domain. However this assumption no longer holds when the data is outsourced to the cloud storage, which takes full maintenance of the outsourced data, and it, is untrusted by the data owner. To enforce access control data is encrypted with certain key and this key is shared only with the authorized users. |
| Various schemes are available which supports the data owner to outsource their sensitive data to the untrusted cloud storage by giving assurance related to the confidentiality, integrity and access control. These schemes thwart and identify malicious actions from the CSP side. Conversely the CSP needs to be protected from the dishonest owner or user, who tries to get unlawful compensations by untruly claiming data modification over CSP. If this concern is not appropriately handled, this may lead the CSP to go out of business one day [3]. |
| In this work, we proposed a technique which addresses some important concerns associated with outsourcing sensitive data to the untrusted remote CSP, namely dynamic data, newness, mutual trust and access control. The outsourced data can be modified and scaled by the data owner. After doing modification, the authorized users are enabled to get the most recent version (newness property) of the outsourced data. A technique is required to identify the staleness of the received data. This issue is dangerous for applications in which critical decisions are made based on the received data. Mutual trust between the data owner and CSP is enabled in the proposed scheme. A method is established to resolute dishonest party from any side. Finally, the access control is considered, which allows the data owner to grant or revoke access rights to the outsourced data. |
RELATED WORK |
| Existing work related to our proposed work can be found in the areas of integrity verification of remotely stored data and file encryption schemes in distributed systems and access control mechanisms over outsourced data. Ateniese et al. [4] designed a model based on PDP (Provable Data Possession) protocol which allows a client to verify the server’s data possession. In this scheme the client preprocesses the file and generates meta-data, stores it locally, and then outsource the file to the server. The server stores the file and starts respond to challenges issued by the client. Integrity verification is done through batch verification of homomorphic hash functions. |
| Curtmola et al. [5] designed a model based on MRPDP which uses replication in order to improve data availability and reliability. By storing multiple copies, if some copies are destroyed still the data can be recovered from the remaining copies. But challenges incur relatively more cost in MR-PDP. |
| Dodis et al. [6] presented a model based on POR (Proofs of Retrievability) in which the client stores a file F on a server and keeps only a short private verification string locally. Later, the client can run an audit protocol to verify the server’s data possession, in which the client acts as a verifier and the server proves that it possesses the data. POR is a complementary approach to PDP, and is stronger than PDP in the way that it can be reconstructed from the portions of the data which are reliably stored on the remote server. |
| Kallahalla et al. [7] presented a cryptographic based file system called Plutus: Scalable secure file sharing on untrusted storage, which enforces access control over outsourced data. In which a file is divided into blocks and each block is encrypted with File-block key and each File-block key is encrypted with File- lockbox key. If the data owner wants to share the file with his clients he just distributes the File- lockbox key to them. |
| Goh et al. [8] presented SiRiUs, which enforces access control over outsourced data. In this scheme each dfile( data file) is attached with a md-file(meta data file). The md-file contains an encrypted key block for each authorized users with some access right, more precisely the md-file contains d-file’s access control list. The d-file is encrypted with FEK and FEK is further encrypted under the public key of each authorized user. |
| Green et al. [9] presented improved proxy re encryption scheme, in which a semi trusted proxy computes a function that converts ciphertext for Alice into ciphertext for Bob without knowing the underlying plaintext. |
PROPOSED SYSTEM |
| Our proposed work addresses some important concerns regarding outsourcing data storage to the remote untrusted storage, such as dynamic data, mutual trust, access control and newness. In our proposed work the owner is allowed to do data modifications on the outsourced data. To validate the newness property of the outsourced data, it requires some metadata which mirror the latest modifications on the outsourced data issued by the data owner. However the block indices must have the awareness that the CSP has modified the blocks at the requested position. At this end, the proposed scheme uses combined hash values and a small data structure called Block Status Table (BST). The TTPA (Trusted Third Party) establishes mutual trust between data owner, CSP and authorized users in an indirect way. To enforce access control the proposed scheme uses three cryptographic functions, namely BrdEnc (Broadcast Encryption), Key Rotation and Lazy Revocation. The BrdEnc allows the data owner to encrypt some confidential information to only authorized users allowing them to access the outsourced data. Lazy revocation enables the revoked users to access the older version of the outsourced data i.e. only the authorized users are allowed to access the most recent version of the outsourced data. Using key rotation authorized users can access both latest version of the data and older version of the data. |
| Block Status Table |
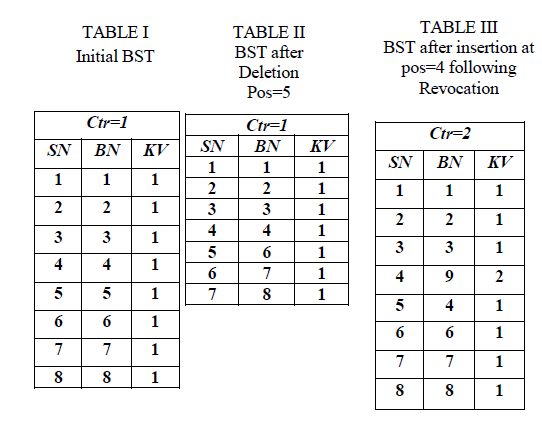
| The block status table is a small data structure used to access and restructure the received file blocks. BST will contain three columns SN, BN, and KV. SN is a serial number which indicates physical positioning of the file blocks. BN indicates the block number of the file blocks. KV indicates the Key Version under which the file block is encrypted. Table 1-3 shows the example BST structure for a file with 8 blocks. |
| Initially the ctr is initialized to 1 as in Table I. The KV is set to ctr. Table II indicates the BST entries for the deletion of block at position = 5 while there is no revocation of users. Hence, the ctr remains unchanged. But in Table III the ctr is incremented by 1 i.e., ctr=2 since, there is an revocation. Hence, insertion of new block following revocation is encrypted under KV =2. |
 |
| A. Our System Model |
| Cloud storage model considered in our proposed work has four main components as depicted in Fig.1 |
| i. A data owner can be an organization, which generates sensitive data that is to be outsourced to the cloud and made available for only authorized users. |
| ii. A Trusted Third Party Auditor (TTPA) [17] who is trusted by all other components and has the capability to detect the dishonest party. |
| iii. A CSP who manages cloud services and provides paid storage service on its infrastructure to the data owner, where he outsources the file and makes them available for authorized users. |
| iv. Authorized users – a set of owner’s clients who have the right to access the outsourced file. |
| Our cloud storage system model can be adopted by many practical applications. For example, Educational applications can be visualized by our model as in Fig.1, where the student’s database that contains large and sensitive information can be stored on cloud servers. In this type of application, an institution can be considered as a data owner, the teaching staffs can be considered as the authorized users, who has given the access rights over the outsourced student’s information, and an independent organization can be considered as the TTPA. Likewise more practical applications can be envisioned in similar settings. The auditing process of the data received from the CSP is done by authorized users. We used TTPA only to solve disputes that may arise due to data integrity and newness verification. |
| B. Outsourcing, updating and accessing |
| The data owner has a file F, which is divided into m blocks and is to be outsourced to CSP, who will provide paid storage space to the data owner. Before outsourcing the file to the cloud server, to achieve confidentiality the owner encrypts the file blocks. After doing so, the owner can interact with the CSP to do full block-level dynamic operations on the file. These block-level operations include insert, delete, append, and modify certain blocks of the outsourced file. For time being, we have considered only insert and delete operations in our work. An authorized user receives the encrypted file, by sending the data access request to the CSP. The encrypted file can be decrypted using a secret key which can be generated by the authorized user. |
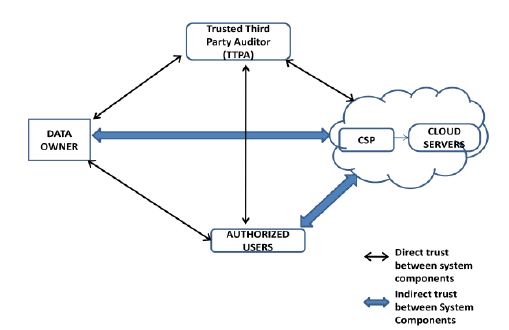 |
| Fig.1 Cloud Storage System Model |
| We imagine that, the verification of the authorized users’ identity has already been done with the data owner; hence we haven’t considered this in our work. And also all authorized users have the same access privilege over the outsourced data. |
| The TTPA is an autonomous entity, and thus has no motivation to collude with any party in the system. The TTPA and the CSP are always online, while the data owner can be online or offline. Even though the owner is in offline, the authorized users can access the outsourced data from the CSP. |
| C. Access control mechanism |
| The three cryptographic techniques Lazy Revocation, Key Rotation and Broadcast Encryption which are discussed below are combined to enforce access control over outsourced data. |
| i. Lazy Revocation |
| The data owner in our proposed work is allowed to revoke access right of some users from accessing the outsourced data at any time. The revoked users are allowed to access unmodified blocks in Lazy Revocation. However, modified or new blocks must not be accessed by such revoked users. This is equivalent to accessing the file blocks from caches. The idea behind this scheme is, modified or new blocks following revocation are encrypted under new key. Thus each data block may have more than one key. Lazy Revocation trades re-encryption cost. Lazy Revocation has been used in many cryptographic schemes [10], [11], [12] |
| ii. Key Rotation |
| In this technique [7], a sequence of keys can be generated from an initial key and a master secret key. The sequence of keys has two main characteristics |
| i. The next key in the sequence can only be generated by the owner of the master secret key. |
| ii. The authorized users knowing the key in the sequence can able to generate previous keys in the sequence. i.e. given the ith key keyi in the sequence, the authorized users can compute the previous keys in the sequence |
| { Keyj } where j < i, but it is infeasible to compute |
| { Keyj }, where j > i without having the master secret key. |
| Property i. allows the data owner to revoke the access right over outsourced data |
| Property ii. Allows the authorized users to maintain access to the file blocks |
 |
IMPLEMENTATION PROCEDURE |
| The implementation procedure of the proposed system is discussed in this section. This section explains about algorithms used for dynamic block level operations over outsourced data. Also this section explains the algorithms used for data access and cheating detection procedure. |
| Procedural Steps |
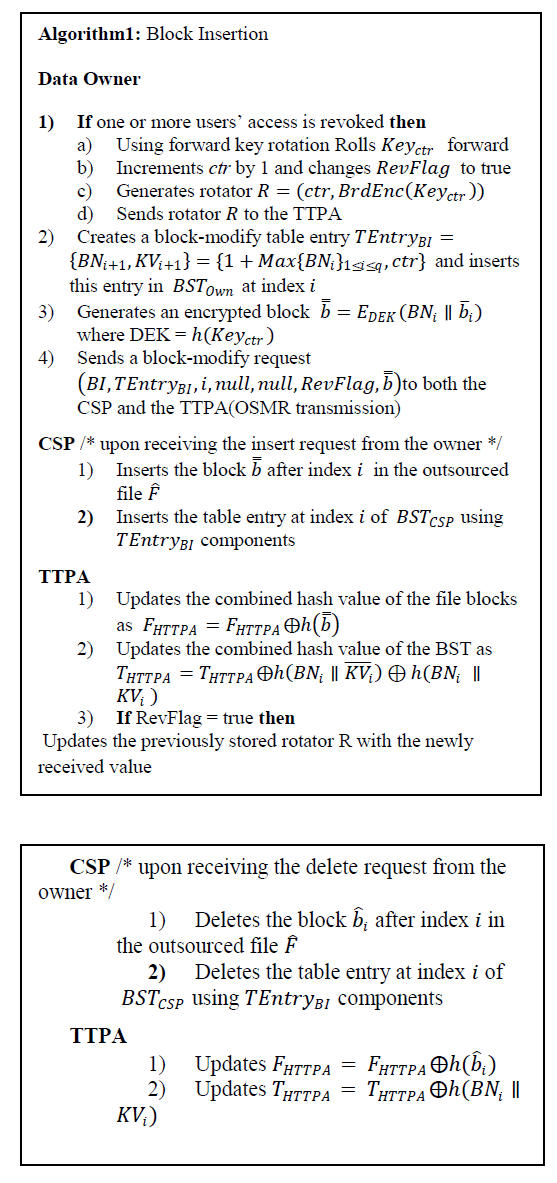
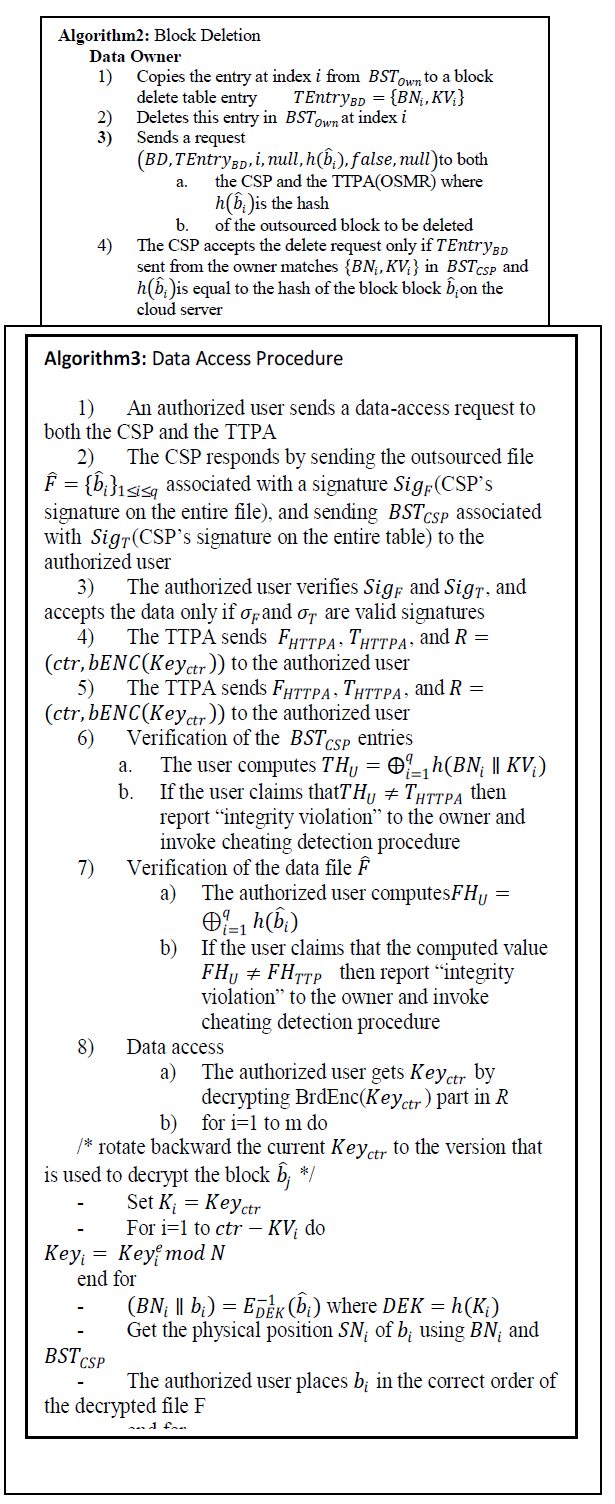
| a) File Preparation |
| File preparation may contain two parts. one is owner’s part and another one is TTPA’s part. |
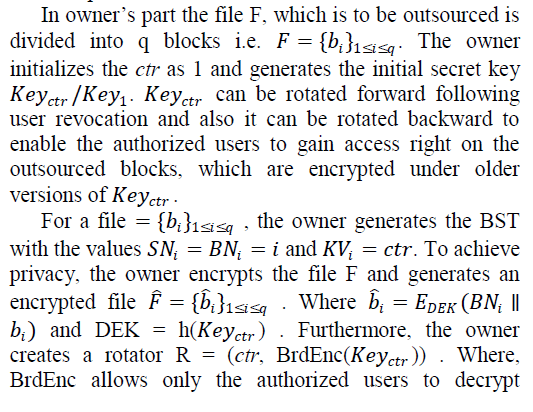
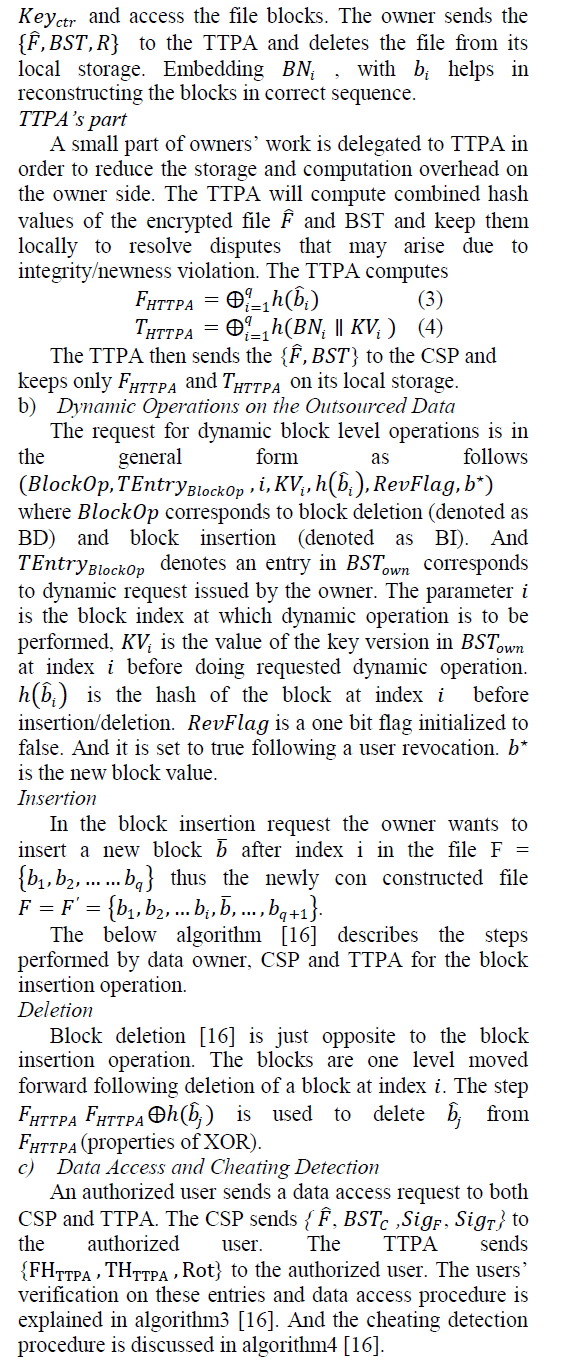
| Owner’s part |
 |
 |
 |
 |
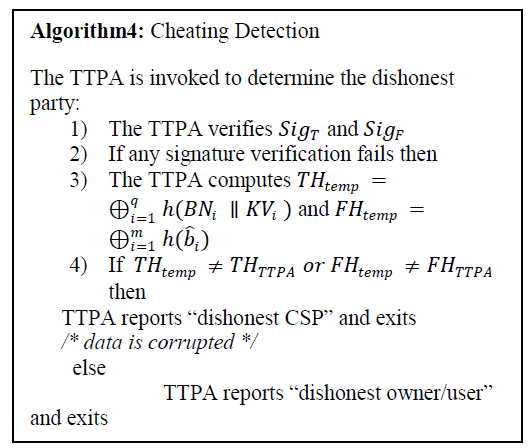 |
| cloudsim. Our implementation consists of four modules: owner module, CSP module, TTPA module and user module. For BrdEnc algorithm we have implemented using jpair library. To implement this algorithm we use an elliptic curve with a 256 bit group order. And we have used MD-5, SHA-256 for hashing, and digital signature algorithms. |
PERFORMANCE ANALYSIS |
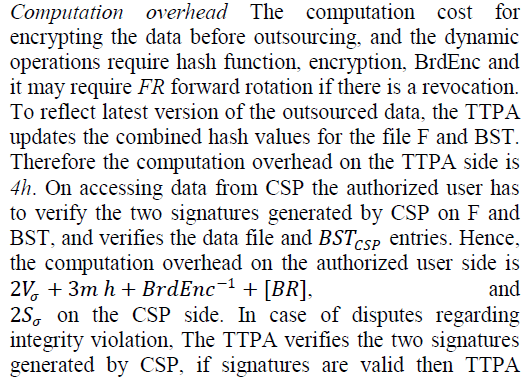
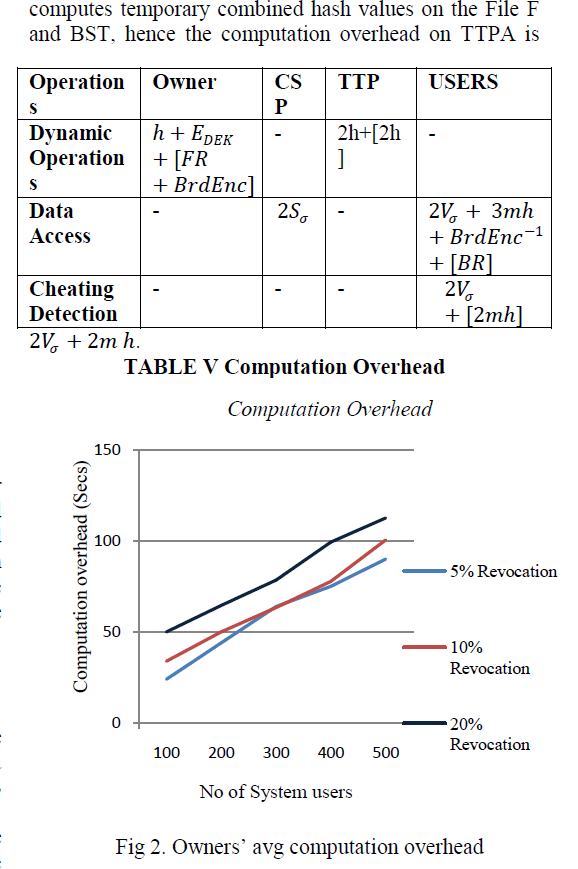
| We evaluate the performance of the proposed scheme by analyzing storage and computation overhead. The data file we have used for our experiments is of size 10GB with block size of 100MB. |
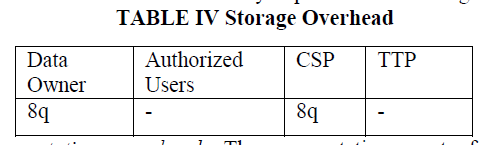
| Storage overhead. This is the additional storage space required to store necessary information other than the outsourced file F. An entry of BST at the owner side is of 8bytes, and the no of entries will be equal to number of blocks q of the file F. Likewise, at the CSP side the additional storage of BST requires 8q bytes, where q is the number of blocks. Each may require 800 MB storage. |
 |
 |
 |
CONCLUSION |
| In this project, we have envisaged a cloud-based storage scheme which supports outsourcing of dynamic data, where the owner is capable of not only archiving and accessing the data stored by the CSP, but also updating and scaling this data on the remote servers. The proposed scheme enables the authorized users to ensure that they are receiving the most recent version of the outsourced data. Moreover, in case of dispute regarding data integrity/newness, a TTPA is able to determine the dishonest party. The data owner enforces access control for the outsourced data by combining three cryptographic techniques: broadcast encryption, lazy revocation, and key rotation. The experimental results show that the proposed scheme is a robust model in terms of security. |
References |
|