ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Aniruddha S. Raut1, Harshraj N. Shinde1, Shubham R. Vidhale1, Rohit V. Sawant1 and Vijay A. Kotkar2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Now-a-days, mobile phones are more powerful than what a desktop used to be few decades back. A hand held device or mobile phones are capable of performing operations what a desktop can perform. Many day-to-day operations are carried out by mobile phones but the most important is exchanging of confidential data such as documents, images etc., this needs to be encrypted. But only encryption of data is not enough in today‟s world. In this paper, we propose a solution that can enhance the security feature of an encryption algorithm using the real time location of a mobile user.
Keywords |
| DES, 3DES, AES, encryption, decryption. |
INTRODUCTION |
| TodayâÃâ¬ÃŸs smart phones are powerful and compact in size; hence its growth rate has gone up exponentially. Due to ease of accessibility and different functions available in mobile phone, it has become an integral part of human life, be it social networking, shopping or exchanging of information between users. Hence, a sense of protectiveness arises for the data to be sent. There are many encryption algorithms available to encrypt your data. But only encryption algorithm is not enough. In this paper we are proposing a solution to enhance the security of an encryption algorithm using the Global Positioning System (GPS) for tracking the location of a mobile phone. In solution, we suggest that an encrypted file can only be decrypted by being at a particular location, which would be decided by the user who would be encrypting the file. |
| Encryption is the process of converting the plain text into a text which makes no sense to humans unless it is decrypted. The text which is encrypted is known as cipher text. For conversion of normal plain text to cipher text, a key is required. Let us take a simple example; “WORK” is a plain text which when shifted by 3 letters making „3âÃâ¬ÃŸ as a key, gives us the “ZQTM” as the cipher text [1]. |
RELATED WORK |
| Hsien-Chao et al showed a method where location is extracted from the mobile in coordinates of east and north then it is multiplied by 1000 and divided by Tolerance distance (TD) due to in accuracy of G.P.S. Then bitwise EX-ORing is done and using MD5 hash algorithm 128 bits key is generated which is divided in 64 bits which is known as LDEA keys. The key generated randomly which has same length as that of LDEA key, i.e. 64-bits. LDEA keys are then EXORâÃâ¬ÃŸ ed with randomly generated key (R) separately and final keys are generated and this generated keys are used for encryption process. When receiver gets the encrypted file with TD and R-key transmitted via symmetric algorithm. The application will acquire the location from GPS sensor, which will divided by TD and operated under MD5 hash algorithm followed by combining with R-key. At the end of this operations we will get final key with which we can decrypt the text [2]. |
| Prasad reddy et al showed that on client side destinations latitude/longitude co-ordinate are given using this coordinates an LDEA key is obtained. This key is used for the encryption of given data. For providing more security R-key is also included in LDEA key. Rotationof bits of cipher text depends on the R- key after whitening( i.e. a decorrelationtransformation that transform a set of random variable having a known covariance matrix M into a set of new random variable whose covariance is the identity matrix ) with the LDEA key using the Exclusive – OR operation. After the encryption of given data ,on the receiver side ,if the receiver is receiving the exact coordinate using GPS, then the receiver can decrypt the file using that coordinate [3]. |
| Ayesha khan et al showed that the latitude and the longitude location positions of both (sender and receiver) is checked and then only the message will be decrypted. For e.g. If the sender is at (x,y) location and the receiver is at (a,b) location then using a hash function convert the values of (x,y) and (a,b) into an integer and multiply it with the RSA formula for encryption [4]. |
METHODOLOGY |
A. Data Encryption Standard (DES): |
| DES is a block cipher which encrypts the data according to block of 64-bit. In this mechanism, 64-bit key is used for encrypting the plain text but each byte of it has 1-bit as parity bit, hence actual key length is 56-bit.DES consists of two fundamental functions of cryptography viz. substitution and transposition [5]. |
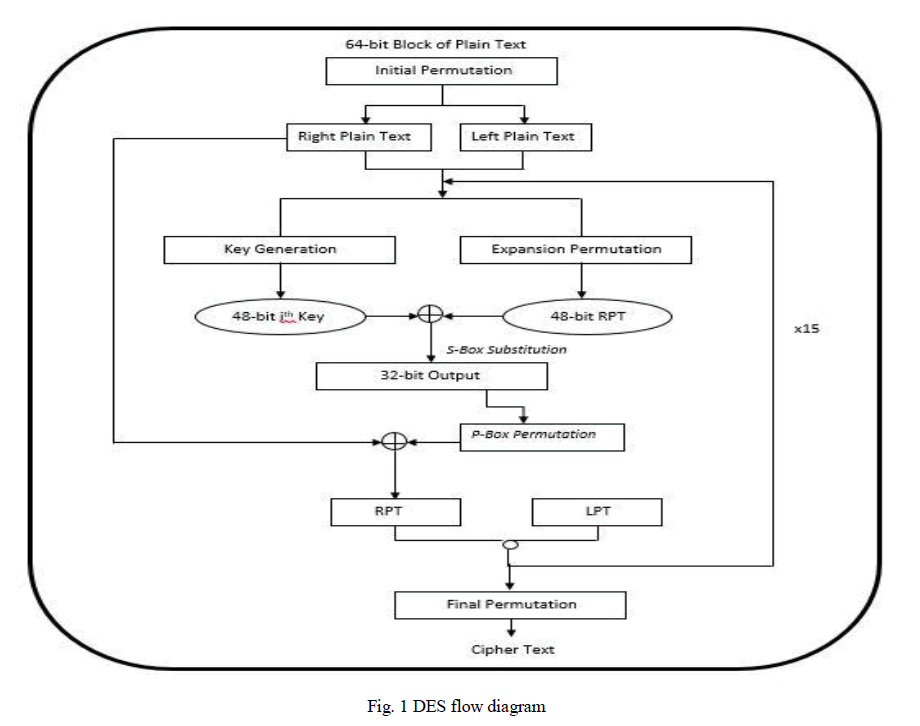 |
| The Fig. 1 shows the flow of DES. The steps shown in the figure are explained below:- |
| It consists of 16 rounds and several steps which are as follows:- |
| 1. A block of 64-bit plain text is given to Initial Permutation. |
| 2. Output of Initial Permutation gives two halves of permuted block. |
| • Left Plain Text (LPT) |
| • Right Plain Text (RPT) |
| 3. Now LPT and RPT go through 16 rounds of encryption process each of which having its own generatedkey. |
| i. By using key transformation, 48-bit key is generated from 56-bit actualkey. |
| ii. RPT of 32-bit is expanded to 48-bit using Expansion Permutation. |
| iii. RPT expanded in prior step is EX-ORed with key. |
| iv. Output got from prior step which is of 48-bit is reduced to 32-bit using S-Box substitution and output is permuted using P-Box permutation. |
| v. The P-box output is EX-ORed with LPT (32-bit) and result is stored in suppose temp. |
| vi. RPT becomes LPT and tempis stored in RPT for the next round. |
| Six steps described above are repeated 15 times. |
| Final Permutation is performed after completion of 16 rounds [6]. |
B. Triple Data Encryption Standard (3DES): |
| 3DESis similar to DES only the difference is that in 3DES, DES is performed thrice.To overcome the drawbacks of DES i.e. brute force attack, weak keys and key space size, 3DES was introduced. In 3DES, DES algorithm is repeated three times using three keys. The keys may be different or same depending on the type being used. |
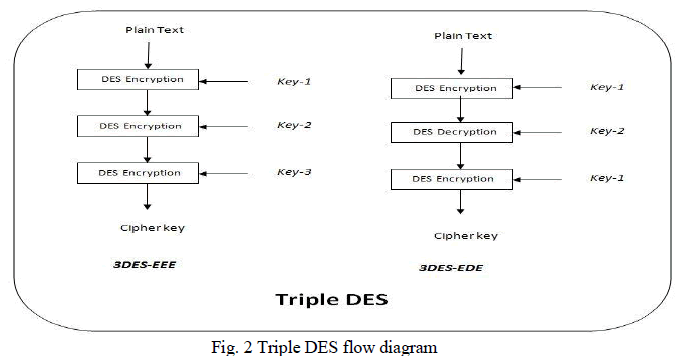 |
| The Fig. 2 shows how the DES encryption is used thrice using different keys. Different types are there of 3DES some which is showed in the diagram and a brief explanation is given below. |
| Types of 3DES are as follows:- |
| i. 3DES-EEE: - Three DES encryptions are performed using three different keys. |
| ii. 3DES-EDE2:- Two DES encryption along with DES decryption in between i.e. encryption then decryption then again encryption is performed using two keys, same key is used for first and third operation [7]. |
C. Advanced Encryption Standard (AES): |
| In the late 1990s, the U.S. National Institute of Standards and Technology (NIST) conducted a competition to develop a replacement for DES. The winner, announced in 2001, is the Rijndael (pronounced "rhine-doll") algorithm, destined to become the new Advanced Encryption Standard [8]. AES uses symmetric key and is a block cipher, it divides the plain text in number of fixed size blocks and then encrypts it. Decryption is also block by block process. |
| AES algorithm takes 128 bit plain text and produces a 128 bit cipher text using a key. Usually, 128 bit key is used but they may vary according to requirement. Different keys available are 192 and 256 bit keys. Numbers of rounds are performed for encrypting a block i.e. a single block is encrypted number of times before sending. |
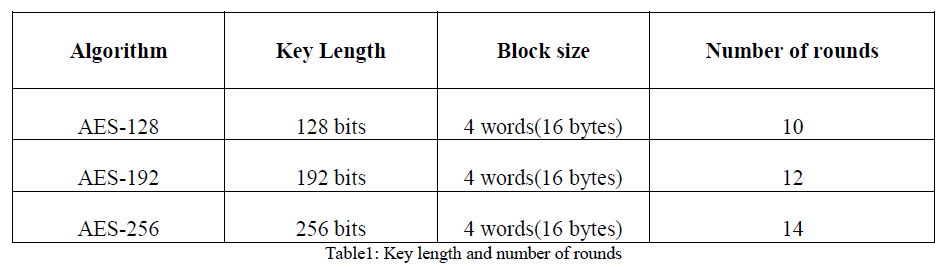 |
| For different keys, different numbers of rounds are used. Table 1 shows different keys and their associated number of rounds and block size [9]. |
Working of AES: |
| The flow diagram of AES is as shown in Fig. 3 below and each function is explained briefly accordingly. |
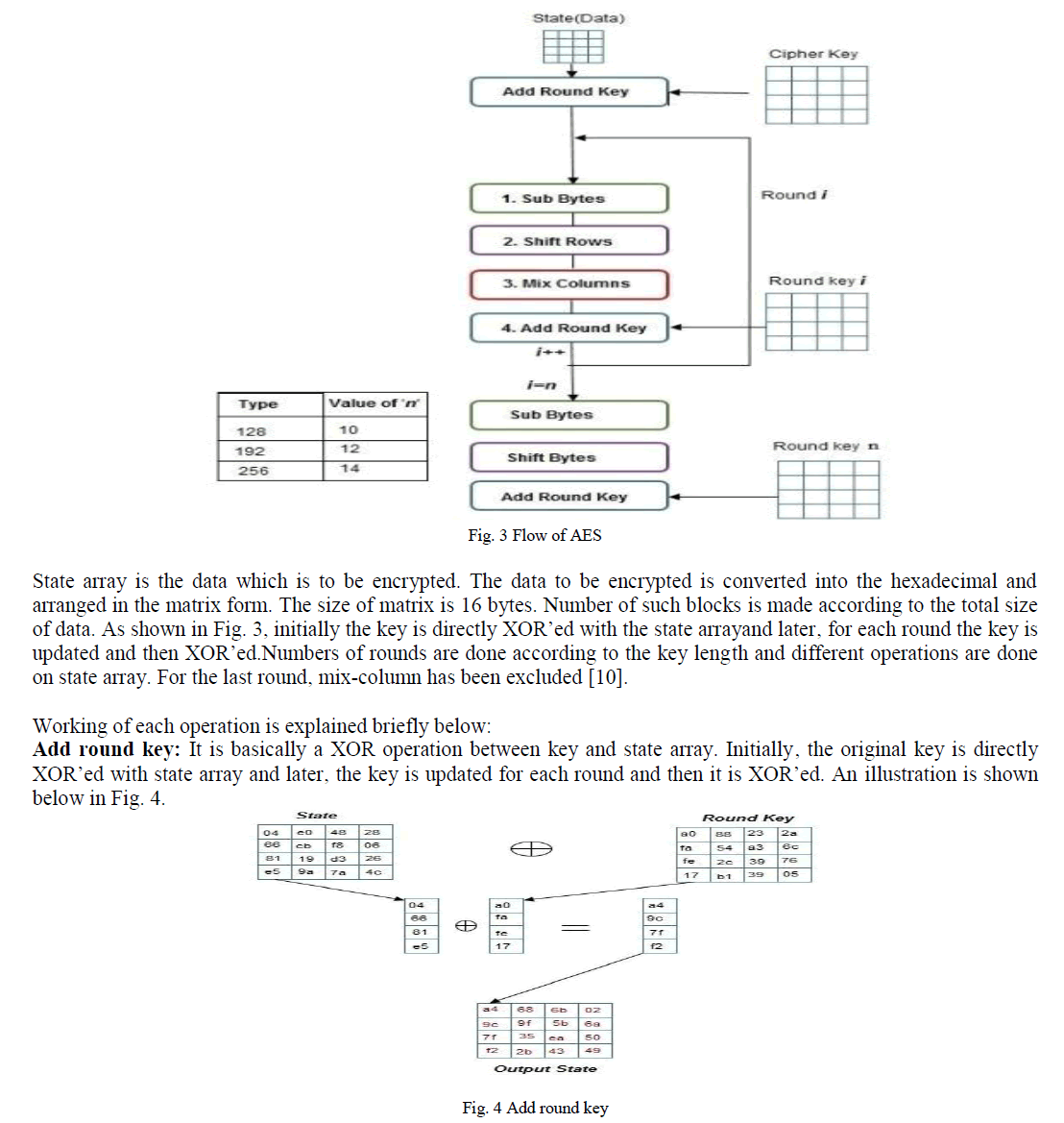 |
| As shown in Fig. 4, first column is taken from both state arrays and keys areXORâÃâ¬ÃŸed and which becomes first column of new state array.Same thing is done for all the columns and then the new state array is passed on to the later stages. Sub Bytes: This is basically a substitution operation. In this operation, the data in the state array is replaced with hexadecimal given in the S-box. S-box is standard substitution box which is pre-defined for AES algorithm. An illustration is shown below in Fig. 5. |
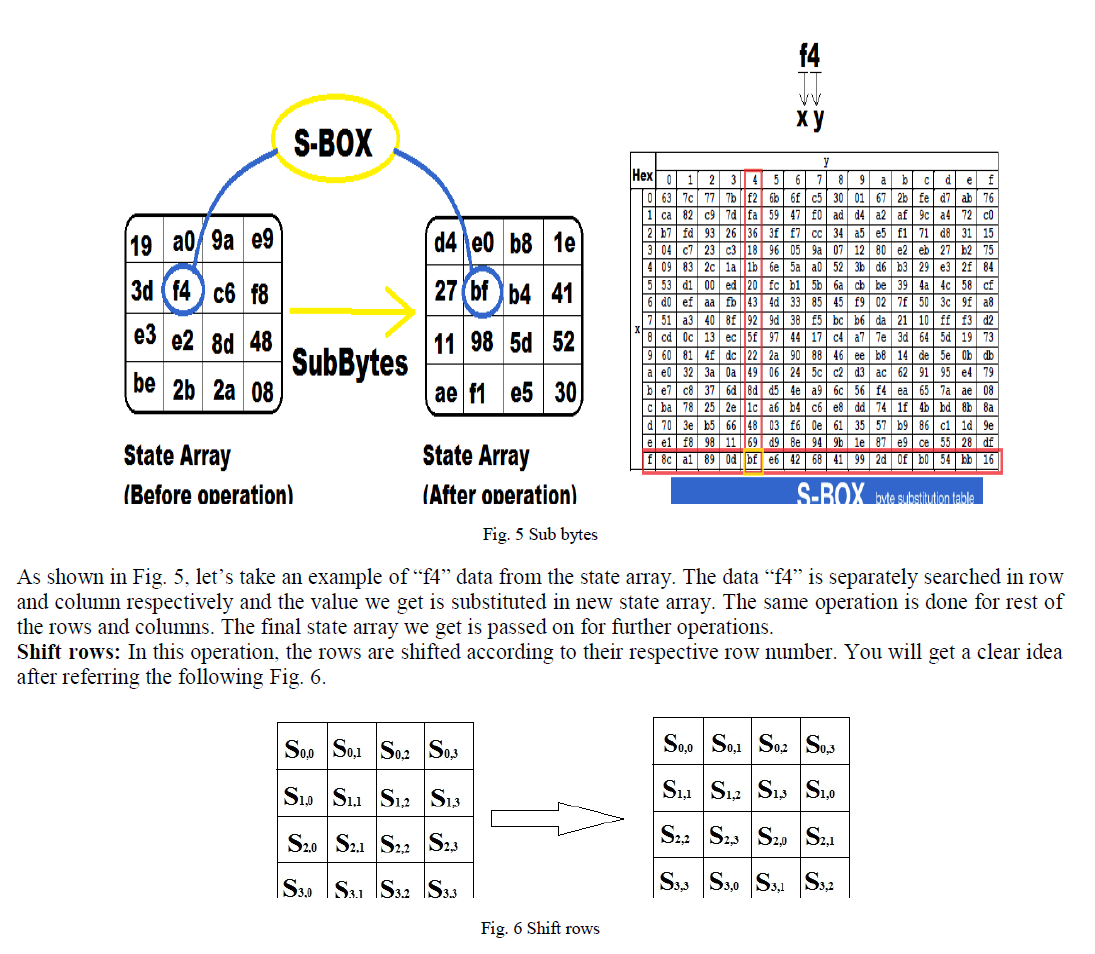 |
| As shown in the figure, the 0th row is not shifted whereas 1st, 2nd and 3rd are shifted by 1, 2 and 3 respectively. The final new state array is passed to later stages. |
| Mix columns: In this operation, each column is multiplied by a pre-defined galois matrix. Example is shown below in the Fig. 7. |
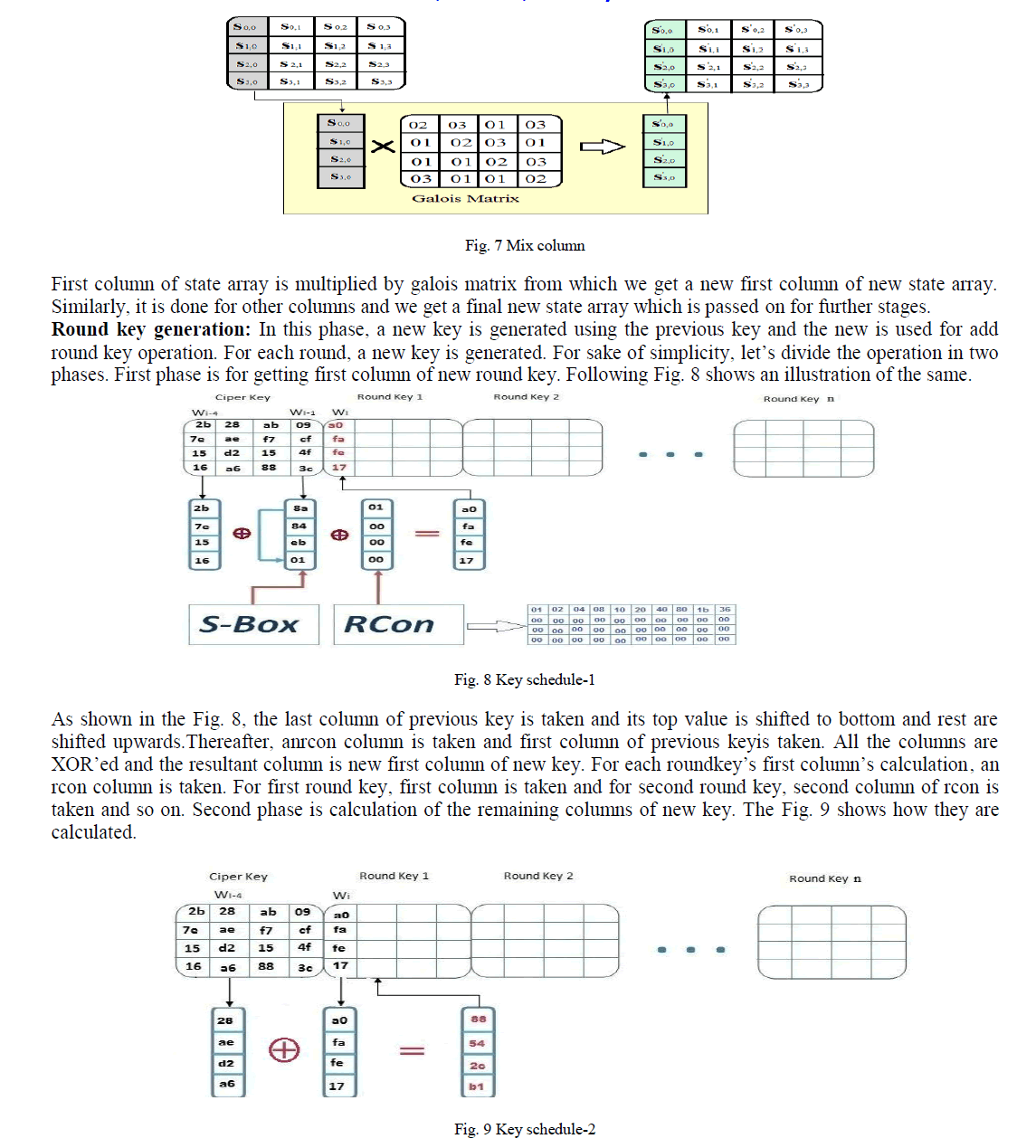 |
| As shown in the Fig. 9 for the calculation of second column, the previous column is taken i.e. Wi-1 and Wi-4 are taken and both are XORâÃâ¬ÃŸed which gives the second column of new key and similarly, it is done for remaining two columns.The above overall process is done to get a new round key which is used for add round key operation [11]. |
RESULT AND DISCUSSION |
| DES and 3DES presumably will take more time to encrypt because they use 64 bits of block as against of 128 bits of block of AES. DES and 3DES are said to be vulnerable against brute force attack, linear and differential cryptanalysis whereas AES is considered to be a secured algorithm with no breaks as of now is reported or published. |
PROBLEM DEFINITION |
| Data should be decrypted without exchange of keys between sender and receiver and at the location specified by the sender. Additionally, there should be other parameters present like date and time to download the file in the stipulated time period and auto file destructing feature on the server after the time period is exceeded. |
PROPOSED SOLUTION |
| In this solution we would need to have two things a cloud based web services which would store the encrypted file using MySQL database at back end and a mobile application for users. For mobile applications there are many platforms available but considering the popularity of Android OS let us consider the Android application is developed. As we will be using a mobile phone for encryption, considering the computing power and battery consumption we would require we have chosen AES-128 algorithm i.e. 128 bits key will be used [8]. |
| Firstly, a new user needs to sign up and his/her information will be stored in database on cloud service. Then after that user needs to select a contact from his list of contacts available (the receiver also needs to have the same application installedon his/her mobile phone and must have signed up then only it will be visible in senderâÃâ¬ÃŸs contact list). After selecting contact the sender needs to select the file to encrypt. |
| Now the user needs to specify date and time so that during that stipulated date and time the file will be visible on the receivers inbox. After the stipulated time is over the file uploaded on the server will be auto-destructed or automatically deleted. Now the sender has the option to specify One Time Password (OTP) which will be used to make the key or it will be generated automatically. The OTP is now to be sent to receiver via other channel viz SMS, email, voice call etc. whichever sender chooses according to his/her convenience. OTP can also pre-determine i.e. sender and receiver know the OTP before hand and hence there is no need of sending the OTP also which in turn increases the security. The final parameter of location is given. The location parameter is in form of the area/city name which maps the area/city to coordinates using the app built as stated earlier. Now for encryption process we have used AES algorithm (working as shown in Fig 10). |
| Using the date, OTP and location coordinates a 128 bit key is generated and the data is encrypted using AES. Note that time parameter is used only for making the file visible to receiver for that time only and not used for key generation. Using the generated key the file is encrypted and then sent to the server. Fig. 10 |
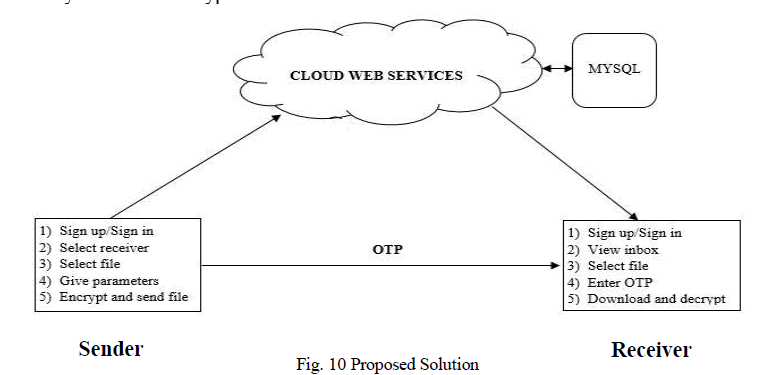 |
| On the receiver side, receiver will get to know that file is available to download then he/she selects the file to download and then he needs to specify the OTP and rest of the parameters required for key generation is fetched by the app itself. If he/she is at correct location then the file downloaded will be decrypted properly if not then the decrypted is not in correct form. |
CONCLUSION |
| We conclude that from above proposed solution we can improve the security of an algorithm using location and other parameters such as date and time which provides more robustness. Moreover, we donâÃâ¬ÃŸt have to exchange the keys which are needed generally in AES. Even if some else gets the file while transmitting the file that person will need the key to decrypt the file but the key is not exchanged in our solution making it stronger than usual AES. Even if the security of cloud service is compromised, and a person gets his hands on file and other parameters stored such as time and date; still that person wonâÃâ¬ÃŸt have OTP which is used while making key and which is sent via other channel. Hence, he wonâÃâ¬ÃŸt be able to decrypt the file. |
References |
|