Keywords
|
| MANET, Mobility, (DSR, DSDV. AODV) Routing Protocol, Wireless. Network simulator(NS-2). |
INTRODUCTION
|
| Mobile ad hoc networks (MANETs) are rapidly evolving as an important area of mobile mobility. MANETs are infrastructure less and wireless in which there are several routers which are free to move arbitrarily and can manage themselves in same manners. MANETs as shown in fig (1) have characteristics that network topology changes very rapidly and unpredictably in which many mobile nodes moves to and from a wireless network without any fixed access point where routers and hosts move, so topology is dynamic. |
 |
| It has to each other and can have multiple hops over wireless links; also connection point to the internet may also change. If mobile nodes are within the communication range of each other than source node can send message to the destination node otherwise it can send through intermediate node. Now-a-days mobile ad hoc networks have robust and efficient operation in mobile wireless networks as it can include routing functionality into mobile nodes which is more than just mobile hosts and reduces the routing overhead and saves energy for other node. Hence, MANETs are very useful when infrastructure is not available, impractical, or expensive because it can be rapidly deployable, without prior planning or any existing infrastructure. Mostly mobile ad hoc networks are used in military communication by soldiers, planes, tanks etc , operations, automated battlefields, emergency management teams to rescue , search, fire fighters or by police and replacement of a fixed infrastructure in case of earthquake, floods, fire etc, quicker access to patient data about record, status, diagnosis from the hospital database, remote sensors for weather, personal area network, taxi cab network, sports stadiums, mobile offices, yachts, small aircraft, electronic payments from anywhere, voting systems , vehicular computing, education systems with set-up of virtual classrooms, conference rooms, meetings, peer to peer file sharing systems , collaborative games with multi users. Major challenges in mobile ad hoc networks are routing of packets with frequently mobile nodes movement, there are resource issues like power and storage and there are also wireless communication issues. As mobile ad hoc network consists of wireless hosts that may move often. Movement of hosts results in a change in routes. In this paper we have used routing protocols from reactive, proactive and hybrid categories to make comparison. |
DESIRABLE PROPERTIES OF AD-HOC ROUTING
|
| Protocols: The properties that are desirable in Ad-Hoc Routingprotocols are |
| Distributed operation:The protocol should be distributed. It should not be dependent on a centralized controlling node. This is the case even for stationary networks. The difference is that the nodes in an ad-hoc network can enter or leave the network very easily and because of mobility the network can be partitioned. |
| Loop free:To improve the overall performance, the routing protocol should guarantee that the routes supplied are loop free. This avoids any waste of bandwidth or CPU consumption. |
| Demand based operation:To minimize the control overhead in the network and thus not waste the network resources the protocol should be reactive. This means that the protocol should react only when needed and that the protocol should not periodically broadcast control information. |
| Unidirectional link support:The radio environment can cause the formation of unidirectional links. Utilization of these links and not only the bi-directional links improves the routing protocol performance. |
| Security:The radio environment is especially vulnerable to impersonation attacks so to ensure the wanted behaviour of the routing protocol we need some sort of security measures. Authentication and encryption is the way to go and problem here lies within distributing the keys among the nodes in the ad-hoc network. |
| Power conservation:The nodes in the ad-hoc network can be laptops and thin clients such as PDA’s that are limited in battery power and therefore uses some standby mode to save the power. It is therefore very important that the routing protocol has support for these sleep modes. |
| Multiple routes:To reduce the number of reactions to topological changes and congestion multiple routes can be used. If one route becomes invalid, it is possible that another stored route could still be valid and thus saving the routing protocol from initiating another route discovery procedure. |
| Quality of Service Support:Some sort of Quality of service is necessary to incorporate into the routing protocol. This helps to find what these networks will be used for. It could be for instance real time traffic support. It should be noted that none of the proposed protocols have all these properties, but it is necessary to remember that the protocols are still under development and are probably extended with more functionality. |
ROUTING PROTOCOL CLASSIFICATION
|
| Routing protocols are classified into different categoriesdepending on their properties. |
| • Centralized vs distributed |
| • Static vs adaptive |
| • Reactive vs proactive |
| In centralized algorithms, all route choices are made at central node, while in distributed algorithms, the computation of the routes is shared among the network nodes. |
| Another classification of routing protocols relates to whether they change routes in response to the traffic input patterns. In static algorithms, the route used by the source-destination pairs is fixed regardless of traffic conditions. It can only change in response to a node or link failure. This type of algorithm cannot achieve high throughput under a broad variety of traffic input patterns. Most major packet networks uses some form of adaptive routing where the routes used to route between source-destination pairs may change in response to congestion. Proactive protocols continuously evaluate the routes within the network, so that when a packet needs to be forwarded the route is already known and can be immediately used. Reactive protocols invoke a route determination procedure on demand only. |
| Table Driven Protocols: Table driven protocols maintain consistent and up to date routing information about each node in the network [6]. These protocols require each node to store their routing information and when there is a change in network topology updation has to be made throughout the network. Some of the existing table driven protocols are |
| • Destination sequenced Distance vector routing (DSDV) |
| • Wireless routing protocol (WRP) |
| • Fish eye State Routing protocol (FSR) |
| • Optimised Link State Routing protocol (OLSR) |
| • Cluster Gateway switch routing protocol (CGSR) |
| • Topology Dissemination Based on Reverse pathforwarding (TBRPF) |
| On-Demand routing protocols: In On-Demand routing protocols, the routes are created as and when required .When a source wants to send to a destination, it invokes the route discovery mechanisms to find the path to the destination. Once a Route has been established, it is maintained until either the destination becomes inaccessible (along every path from the source), or until the route is no longer used, or expired . |
| The different types of On Demand driven protocols are: |
| • Destination-Sequenced Distance-Vector Routing (DSDV) |
| • Ad hoc On Demand Distance Vector (AODV) |
| • Dynamic Source routing protocol (DSR) |
| • Temporally ordered routing algorithm (TORA) |
| • Associativity Based routing (ABR) |
| In recent years, a variety of new routing protocols targeted specifically at this environment have been developed. We will provide routing performance estimates that were gathered through simulation, by investigating a common reactive routing protocol DSR , DSDV and AODV. |
COMPARISON OF TABLE-DRIVEN AND ON-DEMAND ROUTING PROTOCOLS
|
| The table-driven ad hoc routing approach is similar to the connectionless approach of forwarding packets, with no regard to when and how frequently such routes are desired. It relies on an underlying routing table update mechanism that involves the constant propagation of routing information. This is not the case, however, for on-demand routing protocols. When a node using an on-demand protocol desires a route to a new destination, it will have to wait until such a route can be discovered. On the other hand, because routing information is constantly propagated and maintained in table-driven routing protocols, a route to every other node in the ad hoc network is always available, regardless of whether or not it is needed. This feature, although useful for datagram traffic, incurs substantial signaling traffic and power consumption. Since both bandwidth and battery power are scarce resources in mobile computers, this becomes a serious limitation. |
| DSDV Protocol |
| Destination sequenced distance vector routing (DSDV) is adapted from the conventional Routing Information Protocol (RIP) to ad hoc networks routing. It adds a new attribute, sequence number, to each route table entry of the conventional RIP. Using the newly added sequence number, the mobile nodes can distinguish stale route information from the new and thus prevent the formation of routing loops. |
| Packet Routing and Routing Table Management |
| In DSDV, each mobile node of an ad hoc network maintains a routing table, which lists all available destinations, the metric and next hop to each destination and a sequence number generated by the destination node. Using such routing table stored in each mobile node, the packets are transmitted between the nodes of an ad hoc network. Each node of the ad hoc network updates the routing table with advertisement periodically or when significant new information is available to maintain the consistency of the routing table with the dynamically changing topology of the ad hoc network. |
| Periodically or immediately when network topology changes are detected, each mobile node advertises routing information using broadcasting or multicasting a routing table update packet. The update packet starts out with a metric of one to direct connected nodes. This indicates that each receiving neighbor is one metric (hop) away from the node. It is different from that of the conventional routing algorithms. |
 |
| Dynamic Source Routing (DSR):The key distinguishing feature of DSR is the use of source routing. Dynamic Source Routing (DSR) is a reactive protocol i.e. it doesn’t use periodic advertisements. It computes the routes when necessary and then maintains them. Source routing is a routing technique in which the sender of a packet determines the complete sequence of nodes through which the packet has to pass, the sender explicitly lists this route in the packet’s header, identifying each forwarding “hop” by the address of the next node to which to transmit the packet on its way to the destination host. |
| Ad Hoc On-Demand Distance Vector Routing (AODV):Ad hoc On-demand Distance Vector (AODV) [13] isessentially a combination of both DSR and DSDV. It borrows the basic on-demand mechanism of RouteDiscovery and Route Maintenance from DSR, plus the use of hop-by-hop routing, sequence numbers, and periodicbeacons from DSDV. It uses destination sequencenumbers to ensure loop freedom at all times and byavoiding the Bellman-Ford ”count-to-infinity” problem offers quick convergence when the ad hoc networktopology changes In this research paper we attempted to present an overview of two main categories of mobile ad-hoc routing protocols and performance comparison of both the protocols based on Random way point model and the simulation of two routing protocols focussing on their differences in their dynamic behaviours that can lead to performance differences. |
| Random way point mobility model:The random way point mobility model is simple and is widely used to evaluate the performance of MANETs. The random way point mobility model contains pause time between changes in direction and/or speed. Once a Mobile Node begins to move, it stays in one location for a specified pause time. After the specified pause time is elapsed, the MN randomly selects the next destination in the simulation area and chooses a speed uniformly distributed between the minimum speed and maximum speed and travels with a speed v whose value is uniformly chosen in the interval (0, Vmax). Vmaxis some parameter that can be set to reflect the degree of mobility. Then, the MN continues its journey toward the newly selected destination at the chosen speed. As soon as the MN arrives at the destination,it stays again for the indicated pause time before repeating the process. |
| Network Simulators |
| According to dictionary, Simulation can be defined as reproduction of essential features of something as an aid tostudy or training. In simulation, we can construct a mathematical model to reproduce the characteristics of a phenomenon, system, or process often using a computer in order to information or solve problems. Nowadays, there are many network simulators that can simulate the MANET. In this section we will introduce the most commonly used simulators. We will compare their advantages and disadvantages. |
| Network Simulator – NS-2 -Ns-2 is a discrete event simulator targeted at networking research. It provides substantial support for simulation of TCP, routing and multicast protocols over wired and wireless networks. It consists of two simulation tools. The network simulator (ns) contains all commonly used IP protocols. The network animator (nam) is use to visualize the simulations. Ns-2 fully simulates a layered network from the physical radio transmission channel to high-level applications. |
| Writing tcl to run simple wireless simulations Here I present step by step of how to do all the things as needed by one simulation in ns-2 with one tcl scriptssequence [1-5]: |
| Step 1. Create an instance of the simulator: |
| set ns_ [new Simulator] |
| Step 2.Setup trace support by opening file “trace_bbtr.tr” and call the procedure trace-all set tracefd [open trace_bbtr.tr w] |
| $ns_ trace-all $tracefd |
| Step 3.Create a topology object that keeps track # of all the nodes within boundary set wtopo [new Topography] |
| Step 4. The topography is broken up into grids and the default value of grid resolution is 1. A different value can be passed asthird parameter to load_flatgrid {}. |
| $wtopoload_flatgrid $opt(x) $opt(y) |
| Step 5. Create the object God, “GOD”(General Operations Director) is the object that is used to store global information about the state of the environment, network of nodes. set god_ [create-god $opt(nn)] |
| Step 6. Before we can create node, we first needs to configure them. Node configuration APi may sonsist of defining the type of addressing (flat/hierarchical etc.) for example. The type of adhoc routing protocol, Link Layer, MAC Layer, Ifq. |
| $ns_ node-config -adhocRouting $opt (adhocRouting) \ |
| -llType $opt(ll) \ |
| -macType $opt(mac) \ |
| -ifqType $opt(ifq) \ |
| -ifqLen $opt(ifqlen) \ |
| -antType $opt(ant) \ |
| -propType $opt(prop) \ |
| -phyType $opt(netif) \ |
| -channelType $opt(chan) \ |
| -topoInstance $wtopo \ |
| -agentTrace ON \ |
| -routerTrace ON \ |
| -macTrace |
| OFF |
| Scenario: For network traffic generating, what are generated are also statements on such as sources, connections, and so on .This work could be done as a tcl file, |
 |
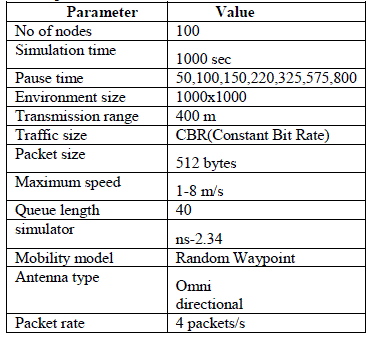
| In this paper some parameters with a specific value are considered. Those are as shown in table . For implementation of AODV, DSR and DSDV with various parameters: |
 |
| We have compared two on-demand routing protocols named as AODV & DSR & one table driven protocol DSDV. Here we generate two different scenarios with variation in number of nodes & speed of nodes. |
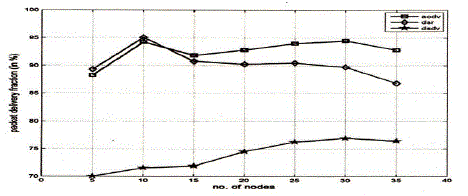
| Scenario1-:The packet delivery fraction is better in DSR as compared to DSDV & AODV , but as the number of nodes increase AODV show the better performance. |
| But in case of routing over head & End to End Delay the performance of DSR is better.as shown in result. |
| Packet delivery fraction-: |
 |
| Routing overhead-: |
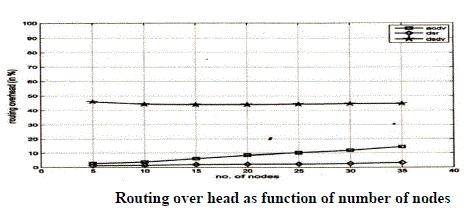 |
| End-to-End Delay-: |
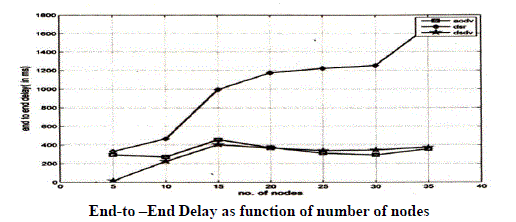 |
| Scenario2-:In case of the packet delivery fraction the simulation result show that DSR is better but the result of end to end delay & routing over head the AODV performance is better |
| Packet delivery Fraction-: |
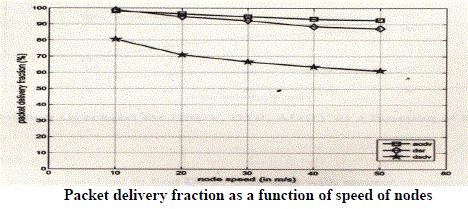 |
| Routing over-head-: |
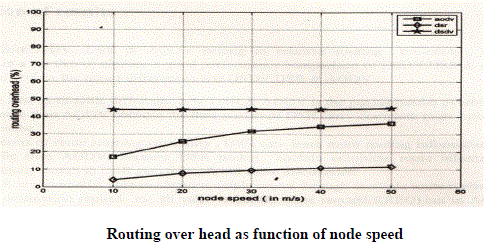 |
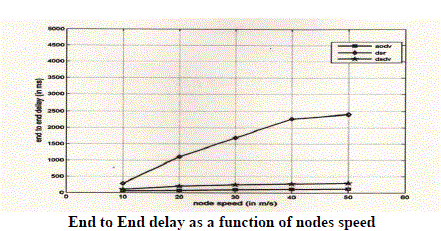
| End-to-End Delay-: |
 |
| Packet Delivery Fraction |
| We note that AODV has a better PDF value when compared to DSR & DSDV for each set of connections. This is because in the time waited at a node, AODV can find an alternate route if the current link has broken whereas DSDV is rendered useless at that point. |
| End-to-End delay of data packets |
| We note that DSR has a better average delay than AODV due to the fact if a link break occurs in the current topology, AODV would try to find an alternate path from among the backup routes between the source and the destination node pairs resulting in additional delay to the packet delivery time. In comparison, if a link break occurs in DSR, the packet would not reach the destination due to unavailability of another path from source to destination, since we assume in AODV only singular paths exist between a source and destination node. |
| Routing Overhead |
| We see that AODV has more routing overhead that DSR & DSDV for any range of pause time. This is attributed to the different mechanism of DSDV and DSR. Due to AODV being a unipath routing protocol, once a link breaks the packet delivery along that route stops. But AODV is a multipath routing protocol and it searches for alternate paths if the current route breaks by flooding the network with RREQ packets. Hence AODV incurs more routing overhead than DSDV &DSR. |
CONCLUSION
|
| Packet Delivery Fraction |
| We note that AODV has a better PDF value when compared to DSR & DSDV for each set of connections. This is because in the time waited at a node, AODV can find an alternate route if the current link has broken whereas DSDV is rendered useless at that point. |
| End-to-End delay of data packets |
| We note that DSR has a better average delay than AODV due to the fact if a link break occurs in the current topology, AODV would try to find an alternate path from among the backup routes between the source and the destination node pairs resulting in additional delay to the packet delivery time. In comparison, if a link break occurs in DSR, the packet would not reach the destination due to unavailability of another path from source to destination, since we assume in AODV only singular paths exist between a source and destination node. |
| Routing Overhead |
| We see that AODV has more routing overhead that DSR & DSDV for any range of pause time. This is attributed to the different mechanism of DSDV and DSR. Due to AODV being a unipath routing protocol, once a link breaks the packet delivery along that route stops. But AODV is a multipath routing protocol and it searches for alternate paths if the currentroute breaks by flooding the network with RREQ packets. Hence AODV incurs more routing overhead than DSDV &DSR. |
FUTURE WORK
|
| A comparison of three routing protocols, AODV and DSDV & DSR has been carried out. It is proposed to compare all other routing protocols considering the same simulation parameters so that an exhaustive comparison of various routing protocols can be made. |
| By studying and analyzing the building block of Routing Protocol it make possibilities to create better routing protocol by new change in these routing protocols |
References
|
- NS Simulator for beginners by Eitanaltman and Tania Jimenez.
- ADHOC NETWORKING by Charles E. Perkins.
- K. AdityaReddy,T Sri Harsha “An efficient DSDV Routing Protocol for Wireless Mobile AD Hoc Networks and its Performance Comparasion ”.IEEE 2005.
- Yinfei Pan “Design Routing Protocol Performance Comparasion in NS-2:AODV comparing to DSR as Example”.
- The network simulator ns-2,http://www.isi.edu/nsnam/ns/.
- V.D Park and M.S Corson, âÃâ¬Ãâ¢A highly adaptive distributed routing algorithm for mobile wireless NetworksÃâ¡ÃÂ, Proc.INFOCOM'97, Apr.1997.
- C.E. Perkins and E.M. Royer, âÃâ¬Ãâ¢Ad-hoc On-Demand Distance Vector RoutingÃâ¡ÃÂ, Proceedings of the 2nd IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, LA, pp. 90-100, February 1999.
- Elizabeth M. Royer, Chai-KeongToh, "A Review of Current Routing Protocols for Ad Hoc Mobile Wireless Networks", IEEE Personal Communications, Vol. 6, No. 2, pp. 46-55,April1999. http://users.ece.gatech.edu/~cktoh/royer.html.Gives a review of routing protocols for ad hoc networks
- Jerry Svedlund and Johan Köpman, “Routing protocols in wireless ad-hoc networks – An implementation study”. Uppsala: Uppsala
- University.Master thesis.
- Martha Steenstrup, “Routing in communication networks”. New Jersey, Prentice Hall. ISBN 0-13-010752-2. [11]Martha Steenstrup, “Routing in communication networks”. New Jersey, Prentice Hall. ISBN 0-13-010752-2.
- Mobile Ad-hoc Networks (MANET), http://www.ietf.org/html.charters/manetcharter. html. (1998-11-29).
- .M. Royer and Charles E. Perkins, âÃâ¬Ãâ¢Multicast Operation of the Ad-hoc On- Demand Distance Vector Routing AlgorithmÃâ¡ÃÂ, University of California, Santa Barbara.
- R.Balakrishna ,Performance issues on AODV and AOMDV for MANETS
- Mobile Ad-hoc Networks (MANET), http://www.ietf.org/html.charters/manetcharter. html. (1998-11-29).
- Mobile Ad-hoc Network Routing ProtocolÃâ¡ÃÂ, International Journal of Computer Science and Network Security (IJCSNS), VOL.7 No.11, pp. 77-84 November 2007.
|