ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
K R Remesh Babu, Geethu K Mohan, Philip Samuel
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Wireless Sensor Network (WSN) is a collection of sensors that are of heterogeneous in nature. Data sensed from the environment are traversed through the network till it reaches the sink. The main focused problem of Wireless Sensor Network is the data integrity throughout the network. If the data is corrupted, considerable amount of energy is wasted at each time when the data is forwarded to the next node. The critical data corruption attack is done by compromised nodes. Various strategies have been introduced to identify the corrupted data and compromised node. This paper focuses a hybrid double layered security strategy for sensed data. The first step of security is applied by appending a Keyed Message Authentication Code (HMAC) to the sensed data by Secure Hash Algorithm (SHA-2/512) which is robust algorithm to ensure message security throughout the network. The second step of security is implemented by a modified form of ConstrAined Random Perturbation based pairwise keY (CARPY+) mechanism. In CARPY+ mechanism guaranteed key exchange between sender and receiver proves the sender nodes identity. Any fail while comparing the key which is extracted from the received message identifies the sender node as a malicious node. The proposed methodology improves the network performance by avoiding data corruption at the network layer and same time identifies the compromised nodes.
Keywords |
| Wireless Sensor Network, Compromised Node Attack, Data Corruption, Secure Hash Algorithm, ConstrAined Random Perturbation based pairwise keY(CARPY) |
INTRODUCTION |
| A Wireless Sensor Network (WSN) consisting of heterogeneous sensors, that are capable of managing and privacy over the network. There are many techniques that are implemented for WSN to maintain the data integrity throughout the network. Most of the applications are implemented in static nodes. Since the advancement in the technology a static node application faces a difficult problem as its mobility. When we are introducing mobility to nodes, it is impossible to maintain a network topology. This paper introduces some technique to keep the data secrecy at the same time it identifies whether a node is compromised or not. |
EXISTING SYSTEM |
| Wireless Sensor Networks are vulnerable to a variety of attacks like altered routing information, selective forwarding, sink hole, worm hole, attack on transit etc. By access, attacks are classified mainly into two categories. Routing attacks and attacks on transit. Data corruption is a type of attack on transit. Data corruption is either by compromised nodes or by attack on data in the network layer. Different techniques are adopted to reduce or to identify such attackers or to reduce such corrupted data. Detailed analyses on techniques are given in the literature survey below. |
| A. Literature Survey |
| Many approaches have been evolved for the packet filtration over the past few decades. One of an effective approach is Statistical En-Route Filtering of Injected False Data in Sensor Networks by Fan Ye, Haiyun Luo, Songwu Lu, Lixia Zhang (IEEE INFOCOM ‟04, Mar. 2004) [5] The main objective is to detect and drop false report. Same event is sensed by multiple sensors. Multiple MAC is associated with forwarding report. Each legitimate report carries multiple MACs generated by different nodes that detect the same stimulus. |
| Intermediate forwarding nodes detect incorrect MACs and filter out false reports. [1] At the sink level the report is tested once again so as to ensure the message integrity. Another important technique proposed was CAT: Building Couples to Early Detect Node Compromise Attack in Wireless Sensor Networks[4] by Xiaodong Lin (IEEE GLOBECOM ‟09, Nov.-Dec. 2009)[9]. This technique proposes a naval compromised node detection method. This is the first effort on addressing the node compromise problem in the first stage. This method presents a new couple-based scheme to detect the node compromise attack in early stage. Specifically, after sensor nodes are deployed, they first build couples in adhoc pattern. Then, the nodes within the same couple can monitor each other to detect any node compromise attempt. The major disadvantages of all the above technique are, the above, mentioned are applicable with static node and static sink. The proposed methodology focuses on mobile compromised nodes[6]. As an added advantage this method detects and drops false data as well as identifies compromised nodes also. |
| B. Problem Definition |
| Data corruption attacks [1] in Wireless Sensor Network are through compromised nodes and network layer data corruption. Any intruder can easily pass corrupted data through this nodes thereby they can drop the equilibrium of the sensor network [12]. Each node in a Wireless Sensor Network preloaded with identification key uniquely. When a node compromised, it is easier for the intruder to corrupt the messages, which in turn results wrong data interpretation and it produces false result. Sensed data is transmitted through the network, while forwarding each packet to the next node consumes considerable amount of energy as well as time. |
| Addressed Problem: |
| Ensure Data integrity while sensing the data (Before sent to the network) |
| Ensure entire message integrity throughout the network. |
| The main aim of this paper is to provide end to end security for data. Once data received in the sink it will process it directly. Wrong information will result in a faulty result. The available mechanism cannot be implemented easily because of high computation and storage issues of security keys. Also compromised node [4] identification needs much more complex algorithms. When come to the corrupted data identification many methods have been introduced. As an effective mechanism intermediate node filtering possesses high filtering capacity but it drains much energy [2]. |
PROPOSED SYSTEM |
| Each sensor node is deployed in the area of interest with specific keys to ensure the integrity of the nodes. The proposed methodology gives importance to both the data sensed from the sensor node and also the entire message that sending towards the sink. This is an effective mechanism which meets all the requirements of sensor nodes. This method successfully identifies large number of compromised nodes. This solution is explained in two sections. |
| Giving security to the sensed data before sending. |
| Giving security to the entire packet while sending to the network. |
| The implementation of security is done by two sections, which is explained below. |
| Using Secure Hash Algorithm |
| Modified ConstrAined Random Perturbation based pairwise keY (CARPY+) [2] |
| Advantages of the proposed methodology, |
| Probability of presence of corrupted data in the network is less. |
| Removal of malicious node increases the network performance. |
| A. Modified Random Perturbation based pairwise keY (CARPY+) |
| The ConstrAined Random Perturbation based pairwise keY (CARPY+) is derived from Blom‟s model. In modified CARPY+ scheme we are assumed [3] that of N nodes I = {S0, S1, S2…… SN} In the CARPY+ method, defined the field Fq = {0, . . . , q−1},q > N, be a finite field. Every calculations are confined under a finite field called Fq, with security parameter „λ‟. It is possible to address λ compromised nodes. For a matrix G, we denote the element in the i-th row and j- th column of G by Gi,j , irow of G by Gi,_ and the j-th column ofG by G_,j . Assume that a symmetric matrix D ∈ F(λ+1)×(λ+1) q and a matrix G ∈ F(λ+1)×N q are randomly generated. |
| For each sensor node i, the row vector Ai,_ and the column vector G_,i are stored in the node i. When two nodes i and j would like to have a common key, they exchange their columns of G in plaintext and then use their private rows of A to calculate Ki,j (= Ai,_· G_,j ) and Kj,i (= Aj,_· G_,i), respectively. When D is totally known by the adversary [4], Blom‟s scheme becomes insecure. The communications become insecure after more than λ sensor nodes are compromised. The reason for this is that the row vector Ai,_ in the sensor node i is directly related to the private matrix D. |
| To enhance security in Blom‟s key, we are adding a random noise to distort key. If the length of the key is „l‟ then only the least r (r <l) bits of Blom‟s key are perturbed after the CRP is added. Thus, the first l-r bits of Blom‟s key are retained. If the desired key length is „L‟, then CARPY+ have to execute l/(L-r) rounds to produce pair wise key. This is explained with an example given below. |
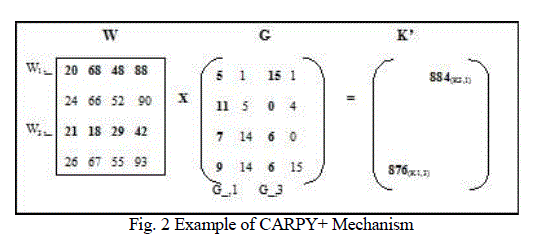 |
| To enhancing the security we are adding noise represented as ɸ, so that the addition of matrix with ɸ obtains the same matrix. |
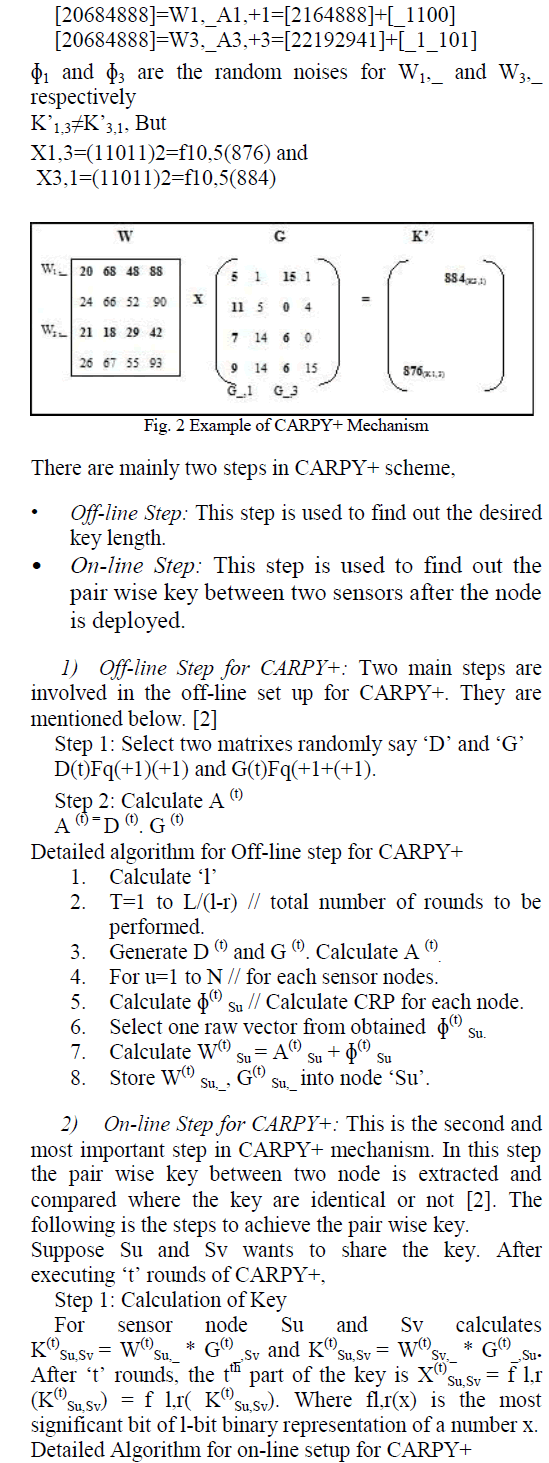 |
 |
| Parsed message =N*1028 -------------------------------- (2) |
| Each message is represented as 64 bits and total of 16 blocks of 64 bits. |
| Step 2: Setting up of initializing values |
| Since it uses hexadecimal hash values 8 hash values have to be generated as H0 0, H0 1, H0 2, H0 3, H0 4, H0 5, H0 6 and H0 7. These values are the initial hash values which can be initialized with the hashing function. |
| Hash Computation |
| Step 1: Produces message Schedule:- The produced message schedule is of 80 constants of 64 bit length. Each hash values is of 64 bit length and finally 8*64 bit is generated [9]. |
| Step 2: Iteratively generate values for hash function:- In the preprocessing step itself the first set of hash value is generated. By function the iteratively the next is generated. |
IMPLEMENTATION |
| The implementation in the real time is much costlier, hence this is done ad a simulation to identify various scenarios in the identification of compromised nodes as well as the message security. This can be much explained in another way. That is the number of messages that have been rejected or dropped without forwarding. The corrupted message is filtering is explained in the section III A. |
| The filtering probability ratio FPR can be calculated by, |
| FPR = number of false data filtered by en-route nodes -------------------------------------------------------- Total number of false data |
| In what follows, we provide the simulation results for FPR. |
| A. Simulation Settings |
| We are simulating the experiment in NS2 environment. 1000 sample nodes are taken for experiment. We fix the transmission range as R in a certain interest region (CIR) of region 300 × 300 m2. Initially we start with 15 nodes [4]. |
PERFORMANCE EVALUATION |
| A Energy Consumption in Non-interactive Key pair Establishments |
| To analyses the total energy consumption we have to consider both the energy consumption for CARPY+ and for SHA. Both analyses are explained separately. Firstly let us find out the energy consumption CARPY+ mechanism only. |
| CARPY+ [2] scheme provide high level of security to the data at the same tome identified the compromised node. While calculating the energy consumption, consider the energy spend for communication and also for computation[6]. That includes energy for encryption (ee) and decryption (ed) in computation and energy for receiving (er) and transmitting (et) in communication. |
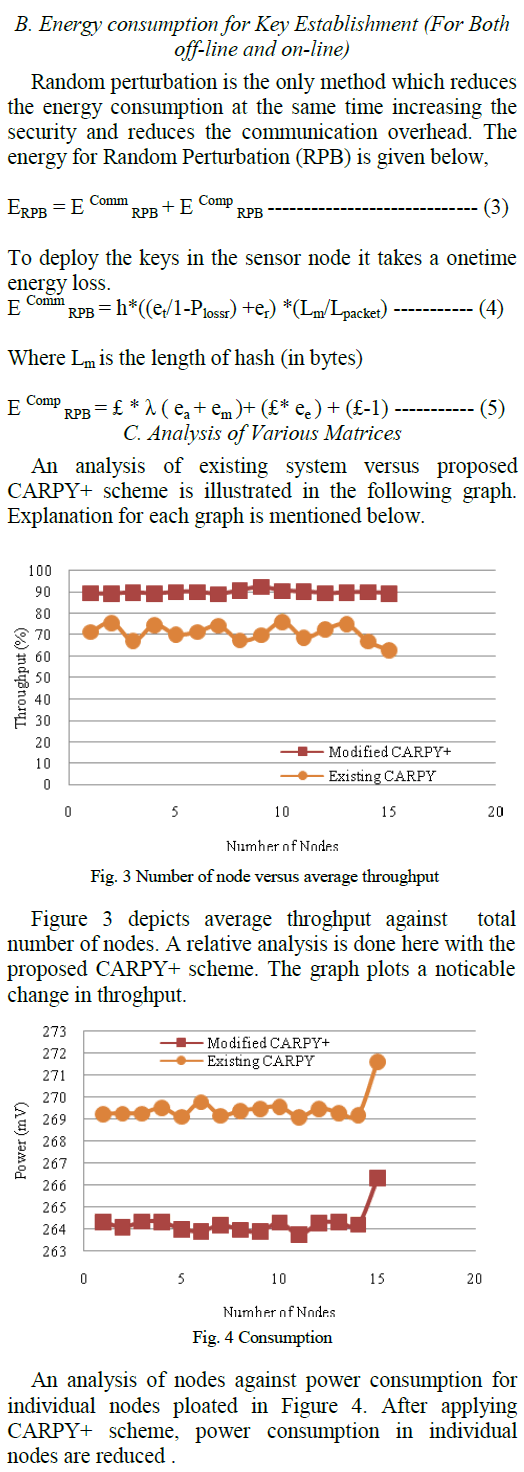 |
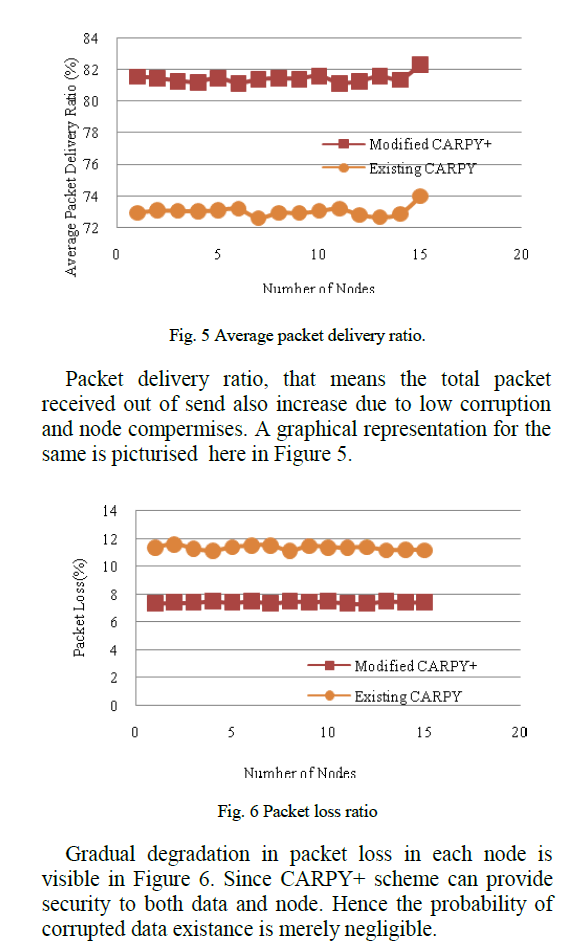 |
CONCLUSION |
| This paper addresses a couple of security mechanisms that together detect corrupted data and there by compromised node also. This scheme is an effective and efficient method to filter false data injected by compromised nodes and gang injection of false data. Rather than filtering the data entirely on the sink intermediate filtering strategy is added to avoid more traffic at the sink, hence it reduces energy wastage in each node. To confirm the node compromising feature a software attested code base testing can add as a future work. |
References |
|