ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
| G.V.Hindumathi, M.Sandhya, K.Sudha and P.Sravya Assistant Professor, Dept. Of CSE,Gayatri Vidya Parishad Enggineering College,Visakhapatnam, India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
The explosive growth of the Internet has brought many good things: electronic commerce, easy access to vast stores of reference material, collaborative computing, e-mail, and new avenues for advertising and information distribution, to name a few. As with most technological advances, there is also a dark side: Some people are sending attachments through emails like spam mails and some fraud images .In this project we check the mail before sending it to the receiver mail id for the fraud images using “Skin Detection Algorithm” and also identify the spam mails. If any fraud images and spam mails are identified then the IP address and physical location of that sender is identified by a third party application. This ethical hacking technique is effectively used for identifying the location of the spam mail. After identifying the sender of the mail, discard the mail and send some warning message to that sender mail id. If that mail doesn‟t contain any spam files or abusive images, send it to the receiver mail id.
Keywords |
| Electronic commerce, E-mail, Skin Detection Algorithm, IP address, Ethical Hacking, Spam files |
INTRODUCTION |
| The Internet or the World Wide Web is indeed a wonderful and amazing addition in our lives. The Internet can be known as a kind of global meeting place where people from all parts of the world can come together. It is a service available on the computer, through which everything under the sun is now at the fingertips of anyone who has access to the Internet. So many protocols are using for uploading and downloading the files in internet. Using internet some disadvantages are also there. Upload some obscene images into web. Using some types of softwareâÃâ¬ÃŸs we can stop the uploading. Main advantage of the internet is emailing. |
| The main problem with emailing is some people attach some obscene images and send through emails. So we canâÃâ¬ÃŸt access the email attachments and canâÃâ¬ÃŸt stop the sending. In this project check every mail attachment, if it is an image. This project mainly used for private network. |
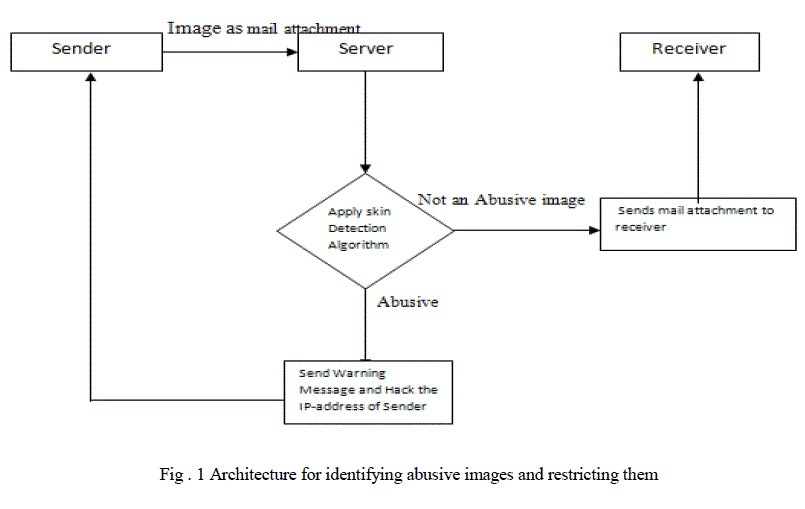
| In private network a user send a mail with attachment to other user through server. Sender sends attachment details and receiver mail ids to server mail id. Server downloads the image and applies Skin Detection Algorithm. And then send it to receiver mail ids or Hack the ip - address |
| As it is mainly intended to for private networks. We assume that the Server has access to all the mails. Integrated 2 applications, as these are already existing systems. The Project is done under 2 phases. |
| A. 1st Phase: It Deals with identification of obscene images if any in mail attachments and restricting them using skin detection algorithm. |
| B. 2nd Phase: It deals with identification of the sender IP- address, if any obscene image identified. |
| This can be extended to public networks also |
 |
METHODS |
| In this proposal we are using Java for sending mails with attachments. Platform Independent, It is a unique feature of java, which made it an internet language. |
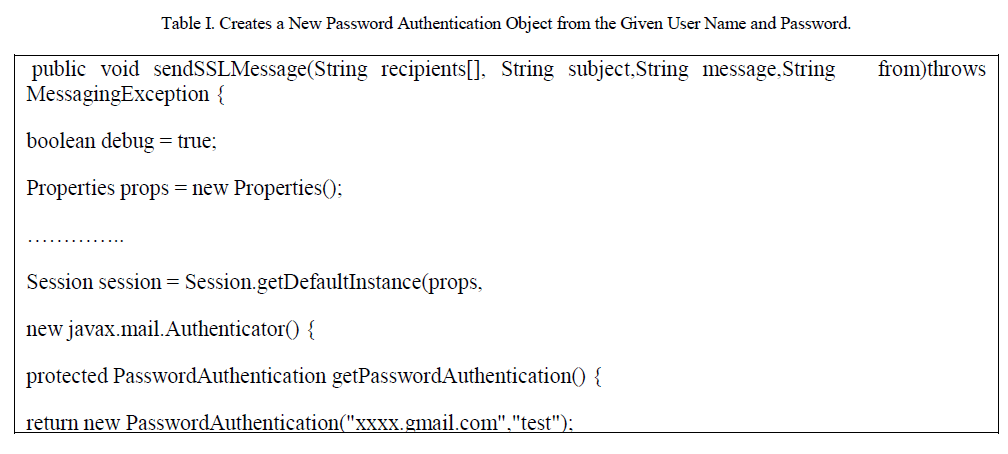
| C. Check the Authentication of Sender : |
| Here check authentication of sender mail ids.If Password authentication function returns „oneâÃâ¬ÃŸ then mail attachement try to send. In case it returns „ZeroâÃâ¬ÃŸ raise exception. |
 |
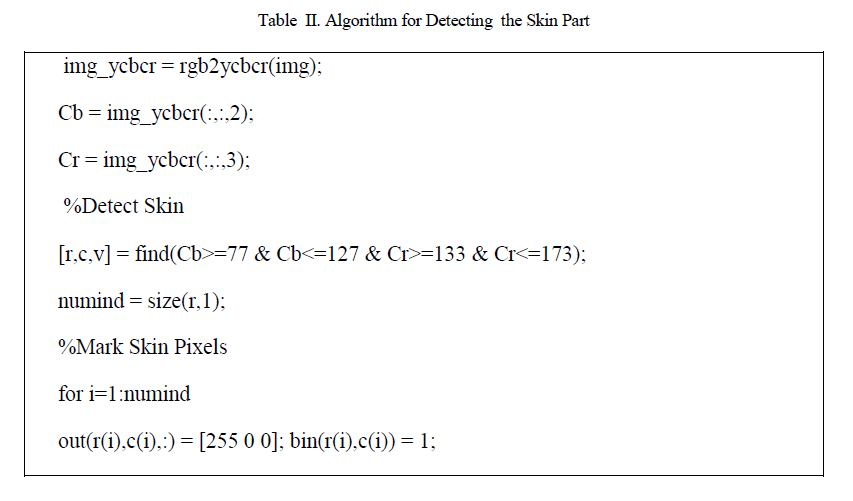
| At server side after getting mail attachment from sender, Server verifies mail attachment image by using Skin detection algorithm. For this we are using MATLAB. As suggested by its name (a contraction of "Matrix Laboratory"), MATLAB provides can create and manipulate arrays of 1 (vectors), 2 (matrices), or more dimensions. In the MATLAB vernacular, a vector refers to a one dimensional (1×N or N×1) matrix, commonly referred to as an array in other programming languages. A matrix generally refers to a 2-dimensional array, i.e. an m×n array where m and n are greater than or equal to 1. |
| D. Skin Detection Algorithm: |
 |
RESULTS |
 |
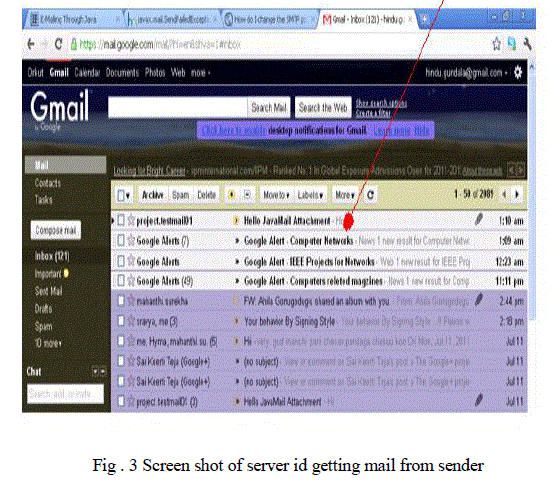 |
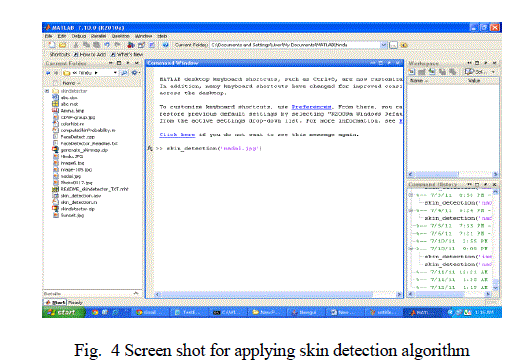 |
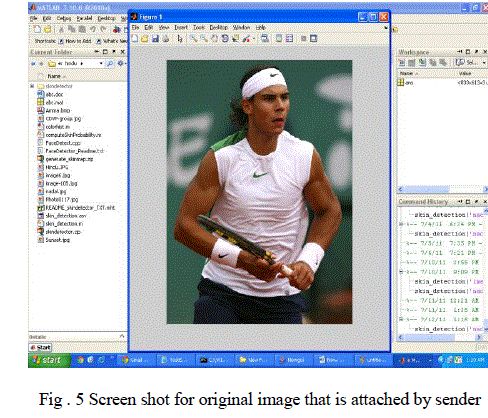 |
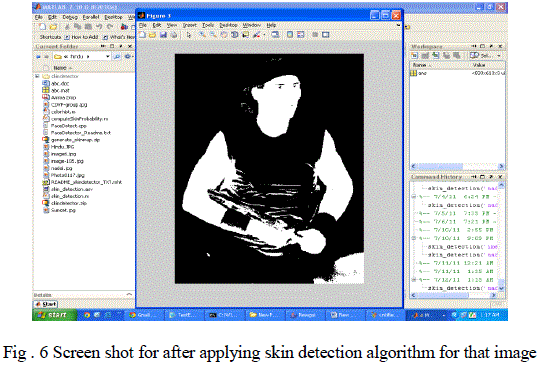 |
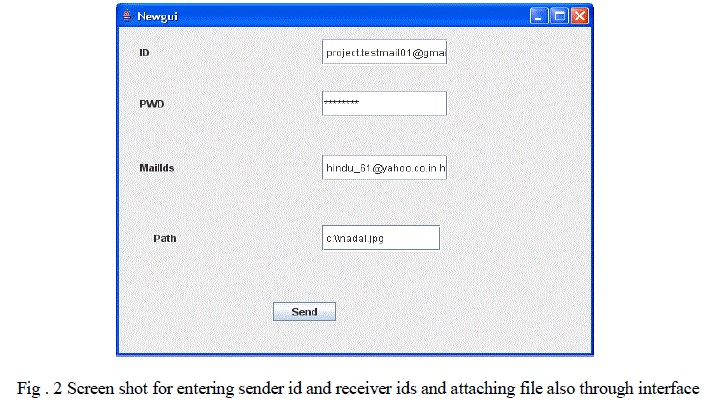
| E. Not an Abusive Mail Attachment: |
| Verify that attached image with skin detection algorithm, if Image is not an abusive image then send it to the receiver mail ids |
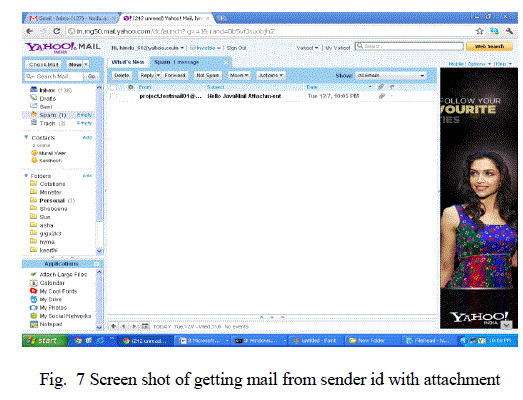 |
| F. An Abusive \Mail Attachment: |
| Verify that attached image with skin detection algorithm, if Image is an abusive image then send some warning message to the sender and hack the sender system also. |
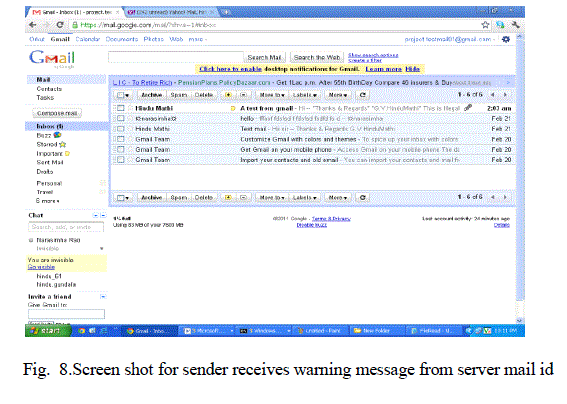 |
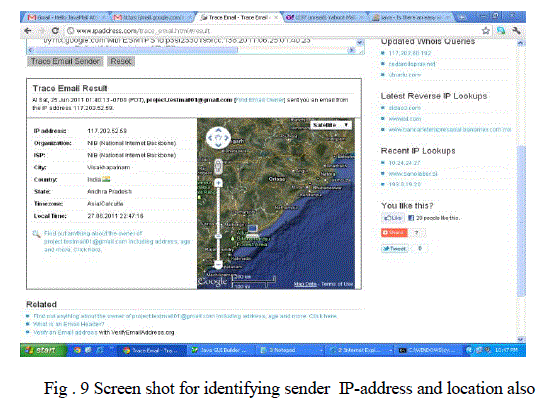 |
CONCLUSION |
| In this proposal, an attempt is been made to identify any abusive images which are sent as attachments through e-mails and restrict such mails in a private network. The mails are first checked for any attachments and if any, the attachments are checked for any abusive content using skin detection algorithm at the server. If any abusive content is present the mail is deprived of transmission to the recipient and a warning message is send to the sender. |
| The implementation is done only for private networks; it may be extended to public networks also. |
FUTURE WORK |
| The basic skin detection algorithm just gives the threshold value but this value is not very accurate. Still work has to be done for accurate skin detection algorithm to give exact value of the image. Second phase of this project is hacking where the IP address of the sender of abusive images is tracked and a warning message is sent. In this project a third party tool is used for hacking but it can be implemented by code also. |
References |
|