In the near future, computing environment can be expected based on the recent progresses and advances in the computing and communication technologies. Next generation of mobile communications will include both prestigious infrastructure wireless networks and novel infrastructure less mobile ad hoc networks (MANETs). Power heterogeneity is common in mobile ad hoc networks (MANETs). With high power nodes, MANETs can improve network scalability, connectivity and broadcasting robustness. However, the throughput of power heterogeneous MANETs could be severely impacted by high-power nodes. In 802.11 based power heterogeneous MANETs, mobile nodes have different transmission power, and power heterogeneity becomes a double-edged sword. On one hand, the benefits of high-power nodes are the expansion of network coverage area and the reduction in the transmission delay. The proposed system considers the power aware routing protocol for a MANET formed of heterogeneous nodes. The proposed approach takes into consideration the battery status of nodes when building the routing table. The developed routing scheme is to optimize packet forwarding by avoiding data packet forwarding through high-power nodes. Due to high mobility of nodes in mobile ad hoc networks (MANETs), there exist frequent link breakages which lead to frequent path failures and route discoveries. A neighbour coverage-based probabilistic rebroadcast protocol is used for reducing routing overhead in MANETs. This approach combines the advantages of the neighbour coverage knowledge and the probabilistic mechanism, which can significantly decrease the number of retransmissions so as to reduce the routing overhead, and can also improve the routing performance.
Keywords |
| Clustering, mobile ad hoc networks (MANETs), power heterogeneous, routing. |
INTRODUCTION |
| A technology that allows transmission of data, via a computer, without having to be connected to a fixed
physical link. Mobile computing encompasses a number of technologies and devices, such as wireless LANs, notebook
computers, cell and smart phones, tablet PCs and PDAs. Basically, any electronic device that helps you organize your
life, communicates with coworkers or friends, or do your job more efficiently is part of mobile computing. Mobile
voice communication is widely established throughout the world and has had a very rapid increase in the number of
subscribers to the various cellular networks over the last few years. An extension of this technology is the ability to
send and receive data across these cellular networks. This is the principle of mobile computing. |
| The goal of "transparent virtual networking" or "mobile computing" is precisely to permit users and programs
to be as effective as possible in this environment of uncertain connectivity, without changes to the manner in which
they operate Mobile computing addresses those application and technical issues that arise when persons move around
within a region or country, or travel between countries and continents. Mobile data communication has become a very
important and rapidly evolving technology as it allows users to transmit data from remote locations to other remote or
fixed locations. This proves the solution to the biggest problem of business people on the move mobility. |
| Routing protocol plays very important part in implementation of mobile ad hoc networks. Due to the nature of
mobile ad hoc networks it is non-trivial problem to find path from source to the destination and perform the
communication between nodes for a long period of time. A number of routing protocols using a variety of routing
techniques have been proposed for use in MANET’s. Adhoc On demand Distance Vector Routing (AODV), Dynamic
Source Routing (DSR), Temporally Ordered Routing Algorithm (TORA), Location Aided Routing (LAR) (in which
nodes search for or maintain a route only when route is needed), and periodic (proactive) protocols such as Destination Sequence Distance Vector (DSDV) , Distributed Bellman Ford (in which nodes periodically exchange routing
information and then can always know a current route to each destination). Also, several protocols use both reactive
and proactive mechanism such as Zone Resolution Protocol (ZRP), Cluster Based Routing Protocol (CBRP). |
| The main focus of research on routing protocols in MANETs has been network performance. There has been
some study on power aware routing protocols for MANETs. Presented below is a brief review of some of them. The
proposed approach takes into consideration the battery status of nodes when building the routing table. It aims to avoid
exhausting the nodes that are falling on optimal routes across the network, thus providing better connectivity and
extending the network lifetime. We implemented the protocol as an extension to JiST/SWANS network simulator, and
compared its performance to other heterogeneous and power aware routing protocols found in the literature |
RELATED WORK |
| The ability of lower power nodes to receive transmissions from higher power nodes but not vice versa. This not only
poses challenges at the routing layer, but also results in an increased number of collisions at the MAC layer due to high
power nodes initiating transmissions while low power communications are in progress. Previously proposed routing
protocols for handling unidirectional links largely ignore MAC layer dependencies [3]. The capacity scaling laws of
mobile ad-hoc networks comprising heterogeneous nodes and spatial in homogeneities [4]. Most of previous work
relies on the assumption that nodes are identical and uniformly visit the entire network space. Moreover even the
channels may not all be identical; they may possibly have different propagation characteristics, and may support
different sets of transmission rates. Much prior research on multi-channel networks has assumed identical channels and
radio capabilities [5]. Flooding [12] in mobile adhoc networks has poor scalability as it leads to serious redundancy,
contention and collision. It can also enhance the reliability of broadcasting. It can also used in mobile and static
wireless networks to implement scalable broadcast and multicast communications. Broadcasting [11] is a fundamental
and effective data dissemination mechanism for route discovery, address resolution and many other network services in
ad hoc networks. While data broadcasting has many advantages, it also causes some problems such as the broadcast
storm problem, which is characterized by redundant retransmission, collision, and contention. In a MANET, one
challenging issue is to construct a virtual backbone [8] in a distributed and localized way while balancing several
conflicting objectives: small approximation ratio, fast convergence, and low computation cost. Many existing
distributed and localized algorithms select a virtual backbone without resorting to global or geographical information.
However, these algorithms incur a high computation cost in a dense network. We consider multi-channel networks
where nodes may be equipped with heterogeneous radios [6], each potentially capable of operation on a limited portion
of the total available spectrum. Moreover even the channels may not all be identical; they may possibly have different
propagation characteristics, and may support different sets of transmission rates. Much prior research on multi-channel
networks has assumed identical channels and radio capabilities. However heterogeneity of channels and radios
introduces a host of new issues that must be handled. Efficient routing [10] is very important for mobile ad hoc
networks (MANETs).Most existing routing protocols consider homogeneous ad hoc networks, in which all nodes are
identical, i.e., they have the same communication capabilities and characteristics. Although a homogeneous network
model is simple and easy to analyze, it misses important characteristics of many realistic MANETs such as military
battlefield networks. In addition, a homogeneous ad hoc network suffers from poor performance limits and scalability. |
PROPOSED ALGORITHM |
| A. Design Considerations: |
| Initial network formation for 100 nodes. |
| Update the location information for each node. |
| Discover the route from source to destination. |
| Route maintenance is considered for each failure route. |
| Performance can be calculated for throughput, packet delivery ratio and end to end delay. |
| B. Description of the Proposed Algorithm: |
| Aim of the proposed algorithm is to improve the performance of the network. The proposed algorithm is consists of
two main steps. |
| Step 1: Calculating Uncovered neighbour set and rebroadcast delay: |
| The Uncovered neighbour set can be calculated by using RREQ packet from its neighbours (eq 1) and the rebroadcast
delay can be calculated by using neighbour list in the RREQ packet and its own neighbour list. |
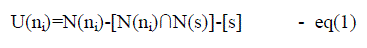 |
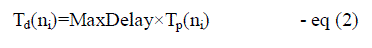 |
| Where N(s) and N(ni) are the neighbors sets of node s and ni, respectively. s is the node which sends an RREQ packet
to node ni. Tp(ni) is the delay ratio of node ni, and MaxDelay is a small constant delay. |
| Step 2: Calculating neighbour knowledge and Rebroadcast probability: |
| When the timer of the rebroadcast delay of node ni expires, the node obtains the final UCN set. The nodes belonging to
the final UCN set are the nodes that need to receive and process the RREQ packet. Note that, if a node does not sense
any duplicate RREQ packets from its neighborhood, its UCN set is not changed, which is the initial UCN set. The
additional coverage ratio (of node ni as |
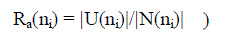 |
| Each node connects to more than 5.1774 log n of its nearest neighbors, then the probability of the network being
connected is approaching 1 as n increases, where n is the number of nodes in the network. Then, we can use 5.1774 log
n as the connectivity metric of the network. We assume the ratio of the number of nodes that need to receive the RREQ
packet to the total number of neighbors of node ni is Fc(ni) |
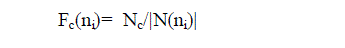 |
| where Nc =5.1774 log n, and n is the number of nodes in the network. |
PSEUDO CODE |
| if ni receives a new RREQs from s then |
| {Compute initial uncovered neighbors set U(ni;Rs:id)
for RREQs:} |
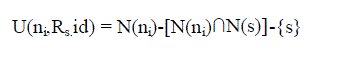 |
| Compute the rebroadcast delay Td(ni):} |
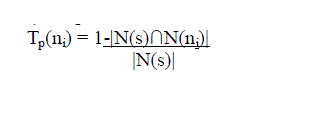 |
| Td(ni) = Maxdelay×Tp(ni) |
| Set a Timer(ni;Rs:id) according to Td(ni) |
| end if |
| while ni receives a duplicate RREQj from nj before |
| Timer(ni;Rs:id) expires do |
| { Adjust U(ni,Rs.id) : } |
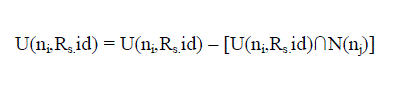 |
| discard(RREQj) |
| end while |
| if Timer(ni;Rs:id) expires then |
| {Compute the rebroadcast probability Pre(ni):} |
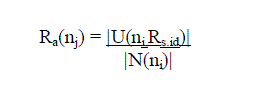 |
| Pre(ni)=Fc(ni).Ra(ni) |
| If Random(0,1) ≤ Pre(ni) then |
| broadcast(RREQs) |
| else |
| discard(RREQs) |
| end if |
| end if |
SIMULATION RESULTS |
| The proposed algorithm implemented with Network Simulator 2. Simulation parameters are as follows: The Distributed
Coordination Function (DCF) of the IEEE 802.11 protocol is used as the MAC layer protocol. The radio channel model
follows a Lucent’s Wave LAN with a bit rate of 2 Mbps, and the transmission range is 250 meters. We consider
constant bit rate (CBR) data traffic and randomly choose different source-destination connections. Every source sends
four CBR packets whose size is 512 bytes per second. The mobility model is based on the random waypoint model in a
field of 1;000 m _ 1;000 m. In this mobility model, each node moves to a random selected destination with a random
speed from a uniform distribution [1, max-speed]. After the node reaches its destination, it stops for a pause time
interval and chooses a new destination and speed. In order to reflect the network mobility, we set the max-speed to 5
m/s and set the pause time to 0. The Max Delay used to determine the rebroadcast delay is set to 0.01 s, which is equal
to the upper limit of the random jitter time of sending broadcast packets in the default implementation of AODV in NS-
2. |
CONCLUSION AND FUTURE WORK |
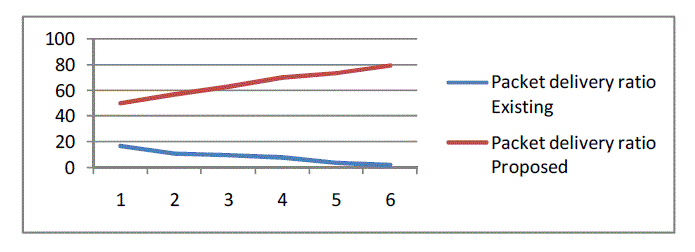
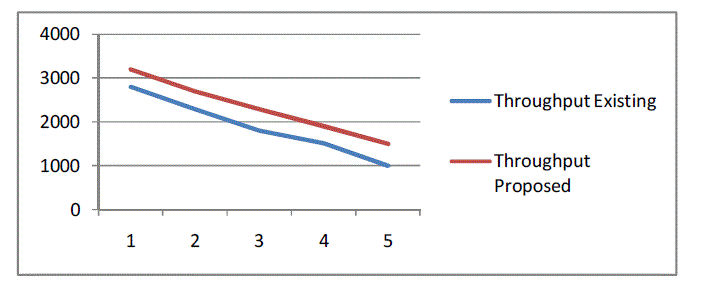
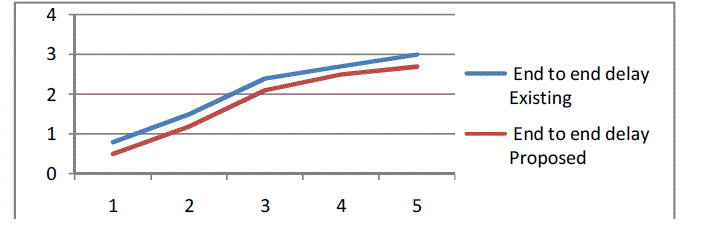
| The simulation results showed that the proposed algorithm performs better with the end to end delay metric,
throughput metric and packet delivery ratio metric. The proposed algorithm reduces the routing overhead and improves
the performance of entire network. As the performance of the proposed algorithm is analyzed between two metrics in
future with some modifications in design considerations the performance of the proposed algorithm can be compared
with other routing protocol. We have used very small network of 50 nodes, as number of nodes increases the
complexity will increase. We can increase the number of nodes and analyze the performance. |
Figures at a glance |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
|
References |
- M. K. Marina and S. R. Das, “Routing performance in the presence of unidirectional links in multihop wireless networks,” in Proc. ACMMobiHoc, Lausanne, Switzerland, Jun.2002,pp.12–23.
- Y. Huang, X. Yang, S. Yang, W. Yu, and X. Fu, “A cross-layer approach handling link asymmetry for wireless mesh access networks,”IEEE Trans. Veh. Technol., vol. 60, no. 3, pp. 1045–1058, Mar. 2011.
- V. Shah, E. Gelal, and P. Krishnamurthy, “Handling asymmetry in power heterogeneous ad hoc networks,” J. Comput. Netw.—Int. J.Comput. Telecommun. Netw., vol. 51, no. 10, pp. 2594–2615, Jul. 2007.
- W. Liu, C. Zhang, G. Yao, and Y. Fang, “Delar: A device–energy–load aware relaying framework for heterogeneous mobile ad hocnetworks eous networks,” IEEE J. Sel. Areas Commun., vol. 29, no. 8, pp. 1572–1584, Sep. 2011.
- P. Leonardi, E. Garetto, and M. Giaccone, “Capacity scaling in ad hoc networks with heterogeneous mobile nodes: The super-criticalregime,” IEEE/ACM Trans. Netw., vol. 17, no. 5, pp. 1522–1535, Oct. 2009.
- V. Bhandari and N. Vaidya, “Heterogeneous multi-channel wireless networks: Routing and link layer protocols,” ACM SIGMOBILEMobile Comput. Commun. Rev., vol. 12, no. 1, pp. 43–45, Jan. 2008.
- Y. M. Huang, M. Y. Hsieh, H. C. Chao, S. H. Hung, and J. H. Park, “Pervasive, secure access to a hierarchical sensor-based healthcaremonitoring architecture in wireless heterogeneous networks,” IEEE J. Sel. Areas Commun., vol. 27, no. 4, pp. 400–411, May 2009.
- J. Wu and F. Dai, “Virtual backbone construction in MANETs using adjustable transmission ranges,” IEEE Trans. Mobile Comput., vol.5, no. 9, pp. 1188–1200, Sep. 2006.
- A. A.Jeng and R.-H. Jan, “Adaptive topology control for mobile ad hoc networks,” IEEE Trans. Parallel Distrib. Syst., vol. 22, no. 12,pp. 1953– 1960, Dec. 2011
- X. Du, D. Wu, W. Liu, and Y. Fang, “Multiclass routing and medium access control for heterogeneous mobile ad hoc networks,” IEEETrans. Veh. Technol., vol. 55, no. 1, pp. 270–277, Jan. 2006.
|