ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
M.Natarajan1, T.Mekala2 and R.Vikram1
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Cryptography is the science of keeping secrets. It is mainly related to data security when transmitting data over networks. During data transmission intruders may possible to acquire information without the knowledge of sender and receiver. So it needs some mechanism to prevent unauthorized access. The security system deals with Multi-Modal biometric features namely Finger-Knuckle-Print and Finger Print for recognition and verification. This approach proves to be more secure. For every transaction, random key will be generates from the user’s samples and it could be highly distinct. Random Triangle Hashing method is used for random key generation [15]. Shuffling process is used for key management and reliable transaction. This system keeping secret the content of information from unauthorized parties, detecting the alteration of data, identifying data origin and preventing an entity from denying previous actions.
Keywords |
| Finger-Knuckle-Print, Finger Print, Multi-Modal biometric features, Random Triangle Hashing, Shuffling Process. |
INTRODUCTION |
| Security is an essential factor for reliable communication over networks. Cryptography is an autonomic element in order to build security. It also deals for user recognition. It is consider as one of the fundamental building block of internet security. There are three classes are cryptographic algorithms are available namely Secret key, Public key and Hash function. Symmetric cryptographic systems use the same key i.e. the decryption key is derived from the encryption key). Public key cryptographic systems use a different key i.e. the decryption key cannot be derived from the encryption key. Hash function takes as variable size message as input and delivers a fixed size hash value [1]. |
| Biometrics is a powerful tool for human verification and authentication. It is done with the help of human biometric templates namely Finger- Knuckle-Print, Finger Print, I ris, Palm Print etc. |
| Recently more research going on hand based samples, because it is highly sensitive and distinct. Moreover, hand based samples provides high accuracy in their results and provides more advantageous for verification. Cryptography needs for reliable communication, but cryptography alone is not enough to achieve it. In such a way, cryptography deals with security levels and biometric handles identity of human. |
| Biometric key generation is mainly used for user identification. The generated key is totally differs from biometric features. So the key is never ever overridden with cryptographic systems. |
PROPOSED SYSTEM |
| The main attention of this approach is to achieve secure communication during data transmission, typically the internet. |
 |
| This approach uses multi-modal biometric features namely Finger-Knuckle-Print and Finger Print. The key will be generated from Finger-Knuckle-Print and Finger print for transaction. This key will be generated randomly for every transaction. The biometric key will be combined with key generated from the user’s data. So it could be secure for sharing files between sender and receiver. |
KEY GENERATION |
 |
| A. Image Enhancement |
| This process helps us to improve the texture of Finger-Knuckle-Print present between the knuckle lines or palm lines. The objective of image enhancement is to achieve better image from human perception. This is done by manipulating it. |
| B. Image Segmentation |
| The session key will be generated from the knuckle portion of the finger. It is mainly because of the bending surface of the fingers are highly distinct in nature. This process achieves greater compatibility for key generation. |
| Overview of Finger Print |
| Fingerprints basically consist of ridges (raised skin) and furrows (lowered skin) that twist to form a distinct pattern. |
 |
| B. Random Triangle Hashing Method |
| It follows concept of cancellable biometrics in the finger print domain. This approach enforces one-way property (non- invert ability) of the biometric sample. |
| C. Key Generation |
| The session keys are generated using Random Triangle Hasing Method [14]. |
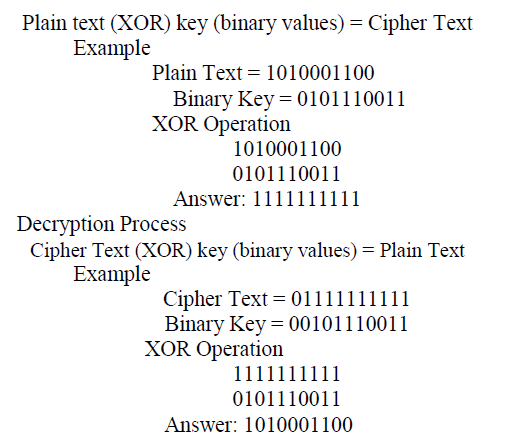
SHUFFLIN PROCESS |
| In shuffling process the binary values of 5 and 9 are 5(0101) and 9(1001). |
| As show in figure 5 random triangle hashing method [15] selects 5, 9 as the chosen co- ordinates. In shuffling process the binary representation of 5(0101) and 9(1001) are selected. |
| Steps |
| • Consider binary value of 5 as one block and 9 as one block. |
| • Parse the 1 st block, if it is 1 append 1 to the 2 nd block else if it is 0 append 0 to the 1 st block itself. |
 |
 |
EXPERIMENTAL RESULTS |
 |
 |
| The above table shows the number of keys needed for various X (Finger-Knuckle-Print) and Y (Finger Print) co-ordinates for a single Finger-Knuckle- Print. |
CONCLUSION |
| In this paper, we proposed a Multi-Modal biometric system for secure transaction. This system provides more attention in terms of security, when compared to single instance biometric systems. The key is extracted from Finger-Knuckle-Print and Finger Print. This approach uses uniqueness of the user and how it can be efficiently used for secure transaction and authentication. In future it will be extended with other biometric samples like Iris, Palm Print, and Retina etc. |
References |
|