ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Madhavi Prathapaneni1 and Gunasekhar Reddy N2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
The rapid proliferation of multimedia over internet demands sophisticated technique for secure and efficient access to information. There is growing need to discourage unauthorized duplication and use of digital data. To provide copyright protection for colour images, an effective, robust and imperceptible watermarking scheme is proposed. Because of its growing popularity, the Discrete Wavelet Transform (DWT) is commonly used in recent watermarking schemes. In a DWT-based scheme, the DWT coefficients are modified with the data that represents the watermark. In this paper, we present a hybrid non-blind scheme based on DWT and Singular Value Decomposition (SVD). After decomposing the cover image into four bands (LL, HL, LH, and HH), we apply the SVD to each band, and modify the singular values of the cover image with the singular values of the visual watermark. Modification in all frequencies allows the development of a watermarking scheme that is robust to a wide range of attacks. We compare our hybrid algorithm with a pure SVD-based scheme, and show that it is considerably more robust and reliable.
Keywords |
| Copyright protection, Discrete Wavelet Transform, Singular Value Decomposition. |
INTRODUCTION |
| Due to rapid growth of multimedia applications over Internet, we have seen an explosion of data in the Internet and the extensive use of digital media. Consequently, digital data owners can transfer multimedia documents across the Internet easily. Therefore, there is an increase in the concern over copyright protection of digital content [1, 2]. In the early days, encryption and control access techniques were employed to protect the ownership of media. However, to protect against unauthorized copying after the media have been successfully transmitted and decrypted, recently the watermarking techniques are utilized [3], because watermarking algorithms embed the watermark into digital data and using these watermark we can prevent the unauthorized copying. A digital watermark is a pattern of bits inserted into an image, audio or video file. The name comes from the barely visible text or graphics imprinted on stationary that identifies the manufacturer of the stationery. There are several applications of watermarking such as, Broadcast monitoring, Owner identification, Proof of ownership, Transaction tracking, Content authentication, Copy control, and Device control [4]. |
| Based on the domain of processing, the watermarking schemes are classified into two categories: spatialdomain and frequency-domain schemes [5]. Spatial domain schemes embed the watermark by directly modifying the pixel values of the cover image and these schemes are less complex in computation. Many techniques have been proposed in the spatial domain, such as the LSB (least significant bit) insertion method [6], the patchwork method and the texture block coding method. These techniques process the location and luminance of the image pixel directly. The LSB method has a major disadvantage that the least significant bits may be easily destroyed such as randomly flipping the lower bits or lossy compression. On the other hand, transform domain schemes [7] embed the watermark by modulating the frequency coefficients in a transformed domain such as, Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT) and Discrete Wavelet transformation (DWT) [8]. Transformed domain schemes are more robust when compared to spatial domain schemes [7]. |
RELATED WORK |
| This is the digital information revolution era. It has heralded connectivity, i.e. connectivity over the Internet and connectivity through the wireless network. Innovative devices such as digital camera and camcorder, high quality scanners and printers, digital voice recorder, MP3 player and PDA, have reached consumers worldwide to create, manipulate, and enjoy the multimedia data. The development of high speed computer networks and that of internet, in particular, has explored means of new business, scientific, entertainment, and social opportunities in the form of electronic publishing and advertising, real-time information delivery, product ordering, transaction processing, digital repositories and libraries, web newspapers and magazines, network video and audio, personal communication etc. The cost effectiveness of selling software, high quality art work in the form of digital images and video sequences by transmission over World Wide Web (www) is greatly enhanced as a consequence of technological improvement. The commercial exploitation of www is steadily being more appreciated. |
| The boom in the information age is not without its adverse effects though. Copying is simple with no loss of fidelity. A copy of a digital media is identical to the original. This has in many instances, led to the use of digital content with malicious intent. One way to protect multimedia data against illegal recording and retransmission is to embed a signal, called Digital signature or copyright label or watermark that authenticates the owner of the data. With the ease of editing and perfect reproduction in digital domain, the protection of ownership and the prevention of unauthorized tampering of multimedia data (audio, image, video, and document) have become important concerns. Data hiding, schemes to embed secondary data in digital media, have made considerable progress in recent years and attracted attention from both academia and industry. Techniques have been proposed for a variety of applications, including ownership protection, authentication and access control. Imperceptibility, robustness against moderate processing such as compression, and the ability to hide many bits are the basic but rather conflicting requirements for many data hiding applications. |
DISCRETE WAVELET TRANSFORM |
| The Discrete Wavelet Transform of an image divides the image into bands of approximately equal bandwidth on a logarithmic scale. This is similar to the retina of the human eye that splits the image into several components of each having a bandwidth of approximately equal to one octave. It is believed that the use of DWT for watermarking produces an imperceptible watermark. The basic idea of the DWT for a two-dimensional image is described as follows. An image is first decomposed into four parts of high, middle, and low frequency subcomponents (i.e., LL1, HL1, LH1, HH1) by critically sub-sampling horizontal and vertical channels using subcomponent filters. The subcomponents labelled HL1, LH1, and HH1 represent the finest scale wavelet coefficients. To obtain the next coarser scaled wavelet components, the subcomponent LL1 is further decomposed and critically sub sampled. This process is repeated several times, which is determined by the application at hand. |
| In two dimension Wavelet transformation, the wavelet representation can be computed with a pyramidal algorithm. The pyramid algorithm operates on a finite set of N input data, where N is a power of two; this value will be referred to as the input block size. These data are passed through two convolution functions, each of which creates an output stream that is half the length of the original input. These convolution functions are filters; one half of the output is produced by the low-pass" filter function, and the other half is produced by the high-pass" filter function. |
 |
| Figure 1: Layout of individual bands at different levels of DWT decomposition |
| The two-dimensional wavelet transform that we describe can be seen as an one-dimensional wavelet transform along the x and y axes. Mathematically the wavelet transform is convolution operation, which is equivalent to pass the pixel values of an image through a low pass and high pass filters [9]. A separable filter bank to the image is represented as follows: |
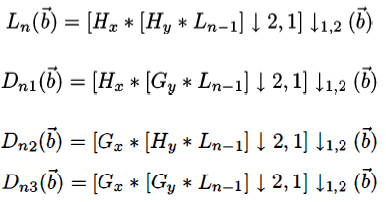 (1) (1) |
| where * represents the convolution operator, ↓2, 1(↓ 1,2 ) represents sub-sampling along the rows (columns) and L0 = I(x) is the original image. H and G are the low pass and band pass filters respectively. Ln is obtained by low pass filtering and is therefore referred to as low resolution image at scale n. The Dn1 are obtained by band pass filtering in a special direction and thus contains the directional detail information at scale n, they are referred to as the detail images. The original image I is thus represented by set of sub images at several scales;{{Ld, Dnl }|l = 1,2,3,n = 1,2,3, ... ,d}, which is multi-scale representation with depth d of the image I. The image is represented by two dimensional signal function, wavelet transform decomposes the image into four frequency bands, namely, the LL1, HL1, LH1 and HH1 bands. H and L denote the high pass and low pass filters respectively. The approximated image LL is obtained by low pass filtering in both row and column directions. The detailed images LH, HL and HH contain the high frequency components. To obtain the next coarse level of wavelet coefficients, the sub band LL1 alone is further decomposed and critically sampled. Similarly LL2 will be used to obtain further decomposition. By decomposing the approximated image at each level into four sub images forms the pyramidal image tree. |
DISCRETE WAVELET TRANSFORM |
| Singular Value Decomposition (SVD) is a numerical technique for diagonalizing matrices in which the transformed domain consists of basis states that is optimal in some sense. The Singular Value Decomposition of image I of size m x n (m ≥ n) is obtained by the operation |
| where U is column-orthogonal matrix of size m x n, S is the diagonal matrix with positive or zero elements of size n x n and transpose of n x n orthogonal matrix V .The diagonal entries of matrix S are known as the singular values of I. The columns of U matrix are known as left singular vector and the columns of the matrix V are known as the right singular vector of I. Thus, each singular value represents the luminance of image layer and the corresponding pair of singular vector represents the geometry of the image layer. |
| In SVD based image watermarking, several approaches are possible. A common method is to apply SVD to the entire cover image and modify all the singular values to embed the watermark. The important property of SVD based watermarking is that the large of the modified singular values of image will change by very small values for different types of attacks. The theoretical analysis of the effects of geometrical distortion is provided in [10]. |
WATERMARK EMBEDDING ALGORITHM |
| The proposed scheme uses the colour image I of size m x n as the cover image and the monochrome image W of size m/2 x n/2 as the watermark. The colour image is transformed into R, G and B channels of size m x n. Human eyes are less sensitive to change in the intensity of the B channel. On the B channel the one-level DWT is applied to generate sub band coefficients LL, LH, HL, HH of size m/2 x n/2. The SVD decomposition is applied on all sub band coefficients and watermark. The singular values of watermark (λw) are added to the singular values (λl for l €{LL, LH, H L, HH}) of the DWT transformed B channel using watermark scaling factor α. |
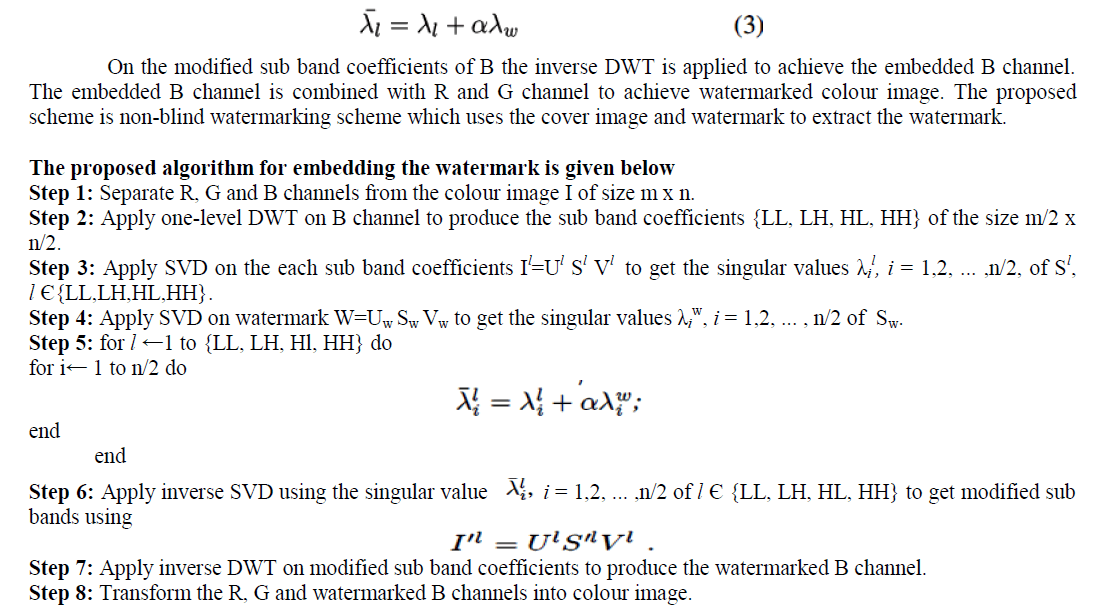 |
WATERMARK EXTRACTION ALGORITHM |
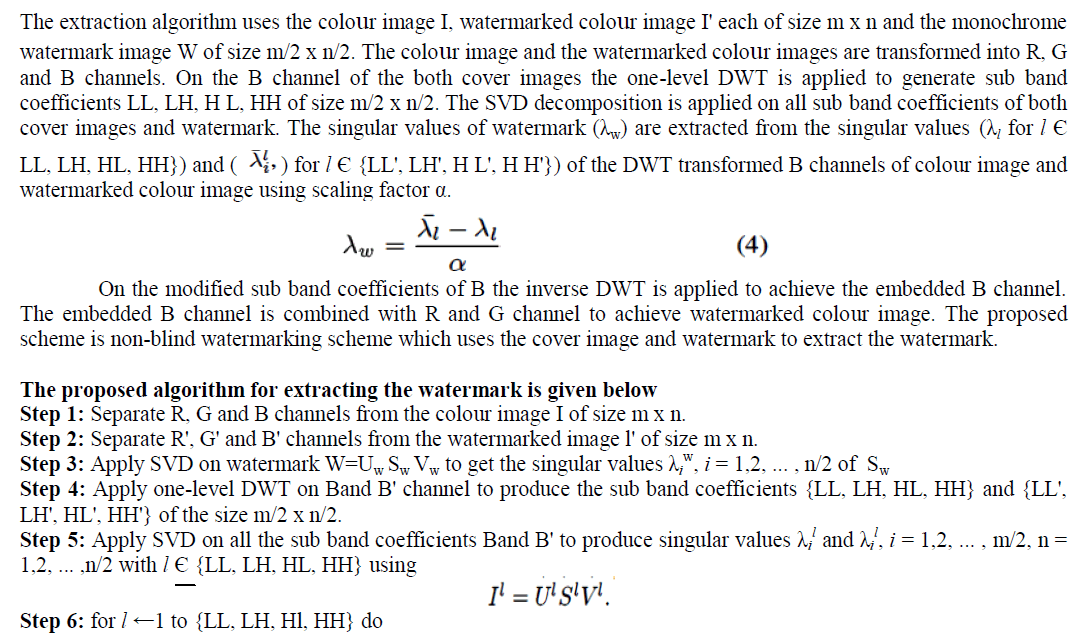 |
 |
EXPERIMENTAL RESULTS |
| The series of experiments are conducted to analyse the effect of embedding and extraction algorithm on the colour image. In these experiments the colour image of size 256 x 256 and monochrome watermark of size 128 x 128 are considered. Figure 2 and Figure 3 shows sequence of outputs of embedding and extraction algorithms, where Mountain image is used as the test image and a logo is used as watermark. |
 |
| Figure 3: Watermark Extraction |
| Figure 4 shows the watermarked Lena cover images with different image processing attacks on it. The effect of different image processing attacks on colour image is analysed considering the watermarked Lena colour image as shown in Figure 4 (a). The contrast of a colour image is usually adjusted to enhance the quality of image. Figure 4 (b) shows the result of applying contrast enhancement on Lena image by increasing 10 % the brightness of image. Image retouching operation is used to improve the quality of image using sequence of operations like erasing, zooming, etc. |
 |
| Figure 4: Effect of image processing operations on Watermarked Lena Image |
| Figure 4 (c) show the result of watermarked Lena image on which retouching operations are applied. Figure 4 (d) show the effect of sharpening on Lena image, where a special type of 2D un-sharp contrast enhancement filter is applied on the watermarked Lena image. The un-sharp contrast enhancement filter enhances edges, and other high frequency components of an image, by subtracting a smoothed ("un-sharp") version of an image from the original image. Image sepia toning is used in image prints which are exposed to sepia in order to replace the metallic silver in the photo emulsion with a silver compound. By doing so the developer could change the colour, but also increase the tonal range of the image. sepia toning is applied on image by adjusting gradient map, filter adjustment and black and white adjustment. |
| Figure 4(e) show the sepia toned Lena cover image. Figure 4(f) and 4(g) shows the Lena cover images with operations like modifying blurring and image warmify. The colour images have three important perceptual attributes, which are hue, saturation and brightness [11].The most obvious is hue, which denotes whether the colour appears red, orange, yellow, green, blue or purple. The saturation denotes the extent to which the hue is apparent. The saturation is zero for gray, black and white. Brightness represents the lightness of a colour, low for black, medium for greys and browns, and high for yellow and white. These three attributes are orthogonal to each other, thus saturation and brightness can be changed without affecting the hue of a colour. Figure 4(h) show the effect of increasing the saturation on Lena colour image. |
CONCLUSION |
| In this paper, we have presented a non- blind watermarking scheme in which the watermark image is hidden into the colour image using the combination of DWT and SVD. The wavelet transform decomposes the image into standard sub band sets which are not necessarily the optimal representation for images. The Singular Value Decomposition (SVD) is numerical technique for diagonalizing the image matrices in which transform domain consist of basis state that is optimal. To achieve high robustness against attacks like Gaussian noise, compression and cropping the combination of SVD and DWT are used. To embed the watermark into cover image the scaling factor is chosen from a wide range of values for all sub bands. The same watermark is embedded into four sub bands which is very difficult to remove or destroy. Watermark embedding in the LL sub band is resistant to attacks including Gaussian blur, Gaussian noise, pixilation, JPEG compression, JPEG2000 compression, and rescaling. Watermark embedding in the HH sub band is resistant to attacks including sharpening, cropping, contrast adjustment, histogram equalization, and gamma correction. Watermark embedding in the LH sub band is resistant to the rotation attack. The rigidity of the proposed scheme is analysed by considering various types of image processing attacks. The scheme was found robust to various types of image processing attacks. |
References |
|