In opportunistic network as one type of challenged networks where networks contact are intermittent or where link performance is highly variable or extreme. This technique to alter user to speak end-toend methods are unstable. when node are selfish, they may not have incentives to participate in probabilistic routing and also the system performance are degrade, enable to participate that selfish node, This approach will considerably decrease the quantity of retransmissions therefore on scale back the routing overhead and improve the routing performance. so finding the neighborhood node, we tend to use channel awareness mechanism for knowledge transmission and to enhance the standard.
Keywords |
| Bargaining game, NCPR (Neighbor
coverage based probabilistic rebroadcast) protocol,
Opportunistic network. |
INTRODUCTION |
| An opportunistic network may be a mobile ad
hoc network and delay tolerant networks, as well as
mobile social networking application. Mobile Ad-Hoc
Networks (MANETs) and Delay-Tolerant Networks
(DTNs), likewise as mobile social networking
applications. Opportunistic networking techniques
modify users to communicate in an atmosphere
wherever contemporaneous end-to-end methods
square measure unavailable or unstable. In such an
atmosphere, as a result of transitivity of links,
messages square measure sometimes passed from one
user to a different in a very store and forward fashion.
Forwarding opportunities arise whenever mobile
devices users inherit the communication vary of every
alternative. In distinction to traditional networking
techniques, during which messages square measure
delivered on pre-existing end-to-end methods,
opportunistic networking permits a message to be transferred from its supply to its destination even once
such a path from the supply to the destination never
exists. |
| In probabilistic routing protocols, once a node
carrying a message meet another node, it estimates the
probability of the latter node having the ability to
bring the message to the destination another node, it
estimates the chance of the latter node having the
ability to bring the message to the
destination[1].Several ideas behind opportunist
networks return from the studies on Delay Tolerant
Networks(DTNs) that are conducted among the net
analysis Task Force and have crystal rectifier to the
specification of the consists of a network of
independent internets every defined by Internet-like
property in among, however having occasiona
Performance Analysis of Cooperation Scheme
for Probabilistic Routing In Opportunistic
Network Using NCPR Protocol
R.Arasa kumar #1 , K.Renuka Devi*2
#1Department of ECE, Velammal College of Engineering and Technology, Madurai, Tamilnadu, India.
*2Department of ECE, Velammal College of Engineering and Technology, Madurai, Tamilnadu, India.
opportunities among them, generally scheduled over
time, some others fully random. During extreme
mobility, watchdog and pathrater can increase network
throughput , while increasing the overhead
transmissions from the standard routing protocols[2].
Ad hoc networks are an increasingly promising area of
re- search with practical applications, but they are
vulnerable in many settings to nodes that misbehave
when routing packets. For robust performance in an
untrusted environment, it is necessary to resist such
routing misbehavior[3]. We show that two techniques
increase throughput by 17% in a net- work with
moderate mobility, while increasing the ratio of
overhead transmissions to data transmissions from the
standard routing protocol's 9% to 17%. Protocol. |
| The message reached its destination and our approach is
intended by the observation that we tend to extend our
model to think about the case during which there is
message exchange in probabilistic routing is analogous to
exchange in markets, in probabilistic routing, a message is
transferred from a node with a lower delivery probability
of the message to a node with the higher delivery
probability, even as during a market, a decent is listed
from an individual with a lower valuation of the nice to an
individual with the higher valuation[4]. we tend to
model the method of probabilistic routing as a series of
bargaining games, to create a broad category of
probabilistic routing protocols incentive compatible[5].
So, being cooperative is often to the simplest interests of
the selfish nodes.a risk of breakdown within the
bargaining method, and gift a sensible solution. |
| Probabilistic routing protocols are supported the
observation that, in observe, nodes dont seem to be
probably to move around indiscriminately, but rather
move during a sure fashion supported quality patterns. If a
two types of nodes has met many times before, its
probably that they will meet once more within the future.
Such quality patterns will be exploited to boost
performance of routing protocol in opportunistic
networks. To use the quality patterns, a probabilistic
metric called delivery probability was introduced.Let, Pa,
b∈ [0,1] be the delivery probability from node a to a
destination node b, this metric indicates however probably
that a node are going to be able to deliver a message to the
destination. every node stores a matrix of delivery
possibilities. When two nodes meet, they exchange their
delivery chance matrices. This matrix is accustomed
update the inner delivery probability matrix. Then the
delivery probability matrix is employed to choose that
message to forward from one node to a different node.
Formally, a basic probabilistic routing protocol works as
follows. |
NEIGHBOR COVERAGE BASED REBROADCAST
PROBABILISTIC TRANSMIT PROTOCOL |
| To calculate the transmit delay and transmit
probability of the projected protocol. Victimisation the
upstream coverage ratio relation of associate in RREQ
packet received from the previous node to calculate the
transmit delay and use the extra coverage ratio relation of
the RREQ packet and therefore the property issue to
calculate the transmit probability in our protocol, that
requires that every node desires its 1-hop neighborhood
information.The node receives the RREQ packet from its
earlier node s, the neighbour list within the RREQ packet
to estimate what percentage its neighbours are not lined
by the RREQ packet from s. The node nickel has a lot of
neighbours not lined by the RREQ packet from supply,
and therefore the RREQ packet will reach a lot of extra
neighbour nodes once node nickel rebroadcasts the RREQ
packet. |
NCPR PROTOCOL DESIGN UNCOVERED NEIGHBORS
CALCULATION |
| We outline the UnCovered Neighbors (UCN) set
U(ni) of node nickel as follows: |
| U(ni) = N(ni) − [N(ni) ∩ N(s)] − {s}, (1) |
| Where, N(s) and N(ni) square measure the neighbors
sets of node s and nickel, severally. s is that the node that
sends Associate in Nursing RREQ packet to node nickel.
determination of broadcast delay td(ni) of the node ni: The
node that features a larger broadcast delay could hear
RREQ packets from the nodes that have lowered one,
delay as a result of the broadcast delay is employed to
work out the order of distributive neighbor coverage
information. |
| Td (ni) = MaxDelay × Tp(ni), (2) |
| Where, Tp(ni) is that the delay quantitative relation of
node nickel, and MaxDelay could be a little constant
delay. If the num neighbor is zero, the node will nothing.
attributable to the 2 cases and this system will cut back
the overhead of neighbor list listed within the RREQ
packet. Wireless networks with 10, 20, 30, and 40 mobile
nodes at random distributed during a piece of ground
space of 10km by 10 metric linear unit. Every node has 3
locations within the physical piece of ground, and at
random travel among these locations at a speed uniformly
chosen between 10 m/s and 30 m/s. when reaching its
destination, the node stays there for five minutes.Three
nodes use IEEE 802.11 (at 11Mbps) because the MAC
layer protocol. The radios transmission vary is about to
250 meters. Nodes broadcast hello message each one
second. The length of your time unit employed in
probabilistic routing protocols is about to one minute.
Nodes generate messages with uniform quantity of ten
minutes. The destination of the message is at random
select from the opposite nodes. A message is born if it
cannot be forwarded to a different node in one hour. Each
node has associate in initial credit of 5000, and pays one
hundred credit for every delivered message. |
RESULT AND DISCUSSION |
PACKET DELIVERY RATIO |
| Delivery ratio reflects the impacts of our schemes on the
performance of a opportunistic network with selfish
nodes. Our second set of evaluations are to demonstrate
that our schemes improve the delivery ratio of
probabilistic routing in face of selfish nodes. Behaving
cooperatively when nodes are selfish. |
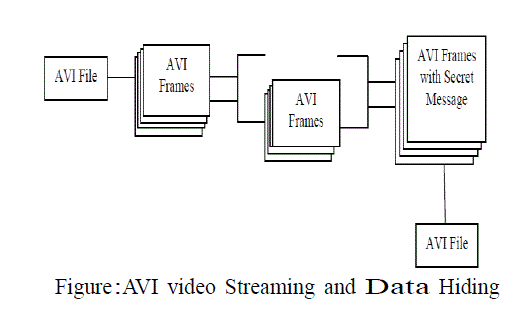 |
| Fig1 shows the packet delivery ratio ,as we have
mentioned selfish behavior of nodes can lower the
network performance. In contrast our schemes improve
the delivery ratio of probabilistic routing in face of selfish
nodes and can boost the network performance in terms of
delivery ratio in face of selfish nodes. |
CUMULATIVE UTILITY |
| The total utility obtained by a node over a period of
time. Cumulative utility reflects the impacts of a node’s
behavior on its own. All nodes prefer higher utilities.
Furthermore, since a beneficial trade brings a forwarding
node a positive utility, the nodes always prefer increasing
cumulative utilities. |
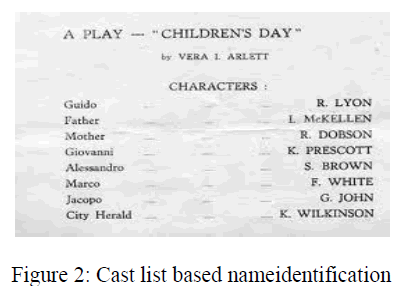 |
| The figures show the results when all nodes are
cooperative and when some of them are selfish. we
consider two situations, in which 30% and 70% of the
nodes are selfish. We observe that the cumulative utilities
achieved by collectively being cooperative are higher than
those of partially being selfish. |
ENERGY CONSUMPTION |
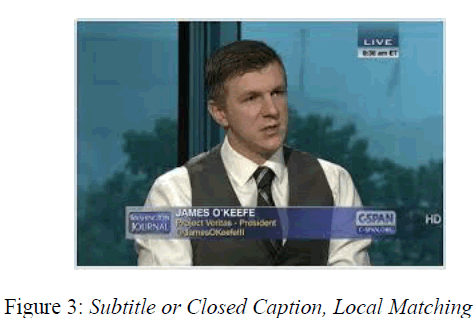 |
| The average delivery ratio as a function of the
number of nodes in the network when all nodes behave
cooperatively and when some of the nodes behave
selfishly, our schemes can boost the network performance
in terms of delivery ratio in face of selfish nodes.to obtain
a more accurate additional coverage ratio. In order to
keep the network connectivity and to reduce the
retransmissions and connectivity factor to determine
how many neighbors should receive the packet in the
cooperative incentive scheme. |
COMPARISION OF PARAMETERS |
PACKET DELIVERY RATIO |
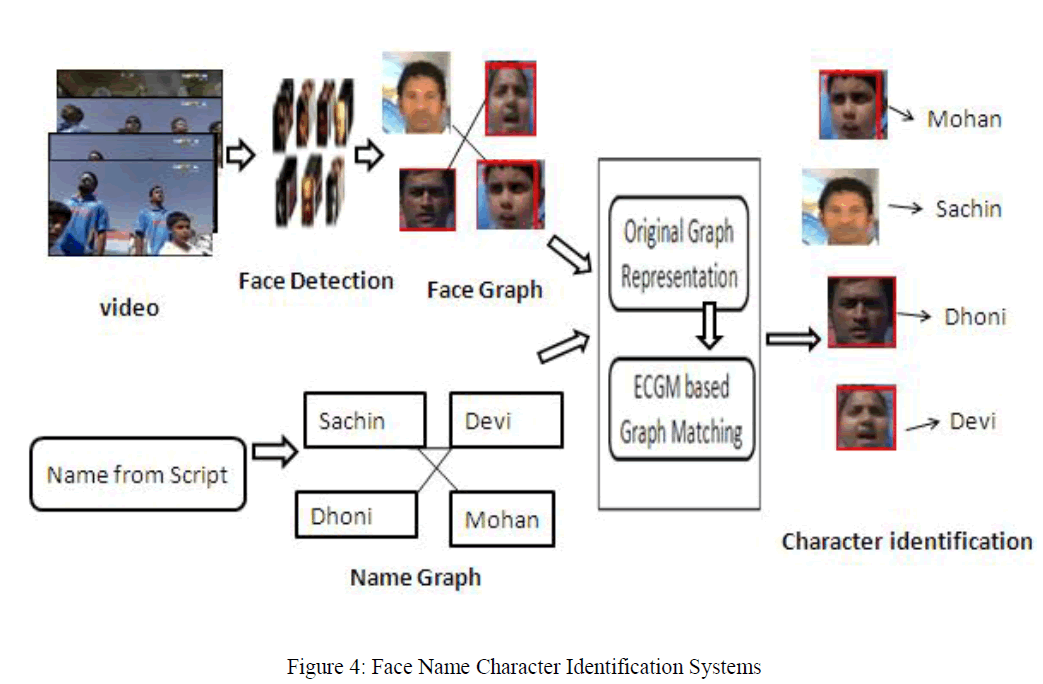 |
| Thus, the good network performance in terms of
delivery ratio in face of selfish nodes. |
CUMULATIVE UTILITY |
 |
PERFORMANCE ANALYSIS |
 |
CONCLUSION |
| This phenomenon will be more severe with an
increase in the number of nodes. It is very important to
reduce the redundant rebroadcast and packet drops caused
by collisions to improve the routing performance.
Compared with the NCPR protocol reduces the collision
rate by about 98.1% on the average. Under the same
network conditions, the collision rate is reduced. when the
NCPR protocol is compared with the other protocol. This
is the main reason that the NCPR protocol could improve
the routing performance |
References |
- U. Shevade, H. H.Song, L. Qiu, and Y. Zhang, “Incentiveaware routing in DTNs,” in Proc.2008 InternationalConf. Netw.Protocols.
- L. Anderegg and S. Eidenbenz, “Ad hoc-VCG: a truthful andcostefficient routing protocol for mobile ad hoc networks with selfishagents,” in Proc. 2003 International Conf. Mobile Comput. Netw.
- M. E. Mahmoud and X. S. Shen, “Stimulating cooperation inmultihop wirelessnetworks uses cheating detection system,” in Proc.2010 IEEE Conf. Comput. Commun
- N. Ben Salem, L. Buttyan, J.-P. Hubaux, and M. Jakobsson, “A charging and rewarding scheme for packet forwarding in multi-hopcellular networks,” in Proc. 2003 ACM Symp. Mobile Ad Hoc Netw.Comput.
- S. Lee, G. Pan, J. Park, M. Gerla, and S. Lu, “Secure incentives for commercial ad dissemination in vehicular networks,” in Proc. 2007ACM Symp. Mobile Ad Hoc Netw. Comput.
- A. Lindgren, A. Doria, andO.Schelen,“Probabilistic routing in intermittently connected networks,” in Proc. 2003 ACM Symp. MobileAd Hoc Netw. Comput.
- S. Marti, T. Giuli,K. Lai, and M. Baker, “Mitigating routingmisbehaviorin mobile ad hoc networks,” in Proc.2000 InternationalConf.MobileComput. Netw.
- V. Srinivasan, P. Nuggehalli, C.-F. Chiasserini, and R. Rao, “Cooperation in wireless ad hoc networks,” in Proc. 2003 Annual IEEEConf. Comput.Commun.
- B. Burns, O. Brock, and B. N. Levine, “MV routing and capacity building in disruption tolerant networks,” in Proc. 2005 IEEEConf.Comput. Commun
- Security and Cooperation in Wireless Networks.CambridgeUniversity Press, 2007.
- B. B. Chen and M. C. Chan, “Mobicent: a credit-based incentive system for disruption tolerant network,” in Proc. 2010 IEEE Conf.Comput.Commun.
- T. Chen and S. Zhong, “Inpac: an enforceable incentive scheme for wireless networks using network coding,” in Proc. 2010 IEEEConf. Comput. Commun.
|