ISSN: 2229-371X
ISSN: 2229-371X
Asst.Prof. Mohammed Najm. Abdallah1*, Ahmed Mosa Dinar 2*;
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at Journal of Global Research in Computer Sciences
When comparing terrestrial wireless sensor networks with underwater wireless sensor networks in terms of challenges, we find that the fundamental difference is the communication medium. Studies in this area indicated that acoustic communication is the typical physical layer technology for underwater networks compared with electromagnetic waves and optical waves. Energy constraint, long delay and limitation in bandwidth are greater challenges in underwater monitoring and other applications. In this paper, we will assess the performance of five UWSN MAC layer protocols of the aquatic environment in terms of energy consumption and received throughput and then nominate three of them based on previous assessment and compare them in terms of total drop packets and average end to end delay. Assessment is carried out by using Aqua-Sim simulators for underwater sensor networks and NS2 based simulator installed in Linux environment
Keywords |
| MAC protocols, Broadcast MAC, Aloha, R-MAC, FAMA, UWAN_MAC, Aqua-Sim |
INTRODUCTION |
| Water quality monitoring is essential to control physical, chemical andbiological characteristics of water. For example, drinking water should not contain any chemical materials that could be harmful to health; water for agricultural irrigation should have low sodium content; water for industrial uses should be low in certain inorganic chemicals. Water quality monitoring can help with water pollution detection and discharge of toxic chemicals and contamination in water [1]. There are several parameters can monitored such as Potential of hydrogen (pH), Dissolved oxygen (DO), Temperature, Conductivity/TDS and Turbidity. |
| Underwater wireless sensor network contain a number of sensors each one of them to monitor specific pollutants these sensors are connected together by acoustic signals. |
| Electromagnetic waves communication and optical waves are not the best candidate for underwater communication. The propagation characteristics of water dictate that electromagnetic waves propagate at long distances through conductive sea water only at extra low frequencies (30–300 Hz). This requirement requires large antennae and high transmission power, which are not suitable for the deployment of sensor networks. In contrast to electromagnetic waves, optical waves do not suffer from such high attenuation. However, optical wave communication under water suffers from significant scattering. Therefore, optical waves are only used for short-range communication in the underwater environment. Thus, links in underwater networks are based on acoustic wireless communications [2]. |
| In UAWSN, MAC constitutes one of the major challenges in sensor networks [2]. Such as available bandwidth is severely limited, Propagation delay in underwater is five orders of magnitude higher than in Radio Frequency (RF) terrestrial channels and Battery power is limited and usually batteries cannot be recharged as solar energy cannot be exploited [3]. |
| The main task of MAC protocols is to provide efficient and reliable access to the shared physical medium in terms of throughput, delay, error rates and energy consumption. However, due to the different nature of the underwater environment, there are several drawbacks with respect to the suitability of the existing terrestrial MAC solutions for the underwater environment. In fact, channel access control in UWSNs poses additional challenges due to the aforementioned peculiarities of underwater channels. |
| However, Frequency Division Multiple Access (FDMA) is not suitable for UWSNs due to the narrow bandwidth available in underwater acoustic channels, and the Vulnerability of limited band systems to fading and multipath effects. Moreover, Time Division Multiple Access (TDMA) shows limited bandwidth efficiency because of the long time guards required in the underwater acoustic channel. Furthermore, the variable delay makes it very challenging to achieve a precise synchronization through a common timing reference [4]. |
| There are two categories suitable for UAWSN: Carrier Sense Multiple Access (CSMA) or Code Division Multiple Access (CDMA). |
| In general, CSMA-based protocols are vulnerable to both hidden and exposed terminal problems. In order to reduce the effects of hidden terminals, MAC proposals should include techniques similar to the ones used in terrestrial networks like MACA [6], that uses RTS/CTS/DATA packets to reduce the hidden terminal problem, and MACAW [7], which adds to the previous one an ACK packet at the link-layer, which can be helpful in an unreliable underwater channel. FAMA [8] extends the duration of RTS and CTS packets in order to avoid data packet collisions, and so contention is managed at both sender and receiver sides before sending data packets. The efficiency of these protocols is heavily impacted by propagation delays due to their multiple handshakes. CDMA-based protocols aren’t useful for acoustic networks because these protocols have some problems such as synchronization and near far problem [9]. |
| Underwater MAC layer protocols should also consider node mobility, low bandwidth, energy efficiency and long propagation delay. Due to the long propagation delay, node mobility and other underwater environment constraints, distributed topologies are used more than centralized topologies. Hence contention based protocols such Broadcast MAC, Aloha, R-MAC, FAMA, and UWAN_MAC are useful for such topologies. |
| In this paper, we will assess these protocols by compared them in terms of energy consume and received throughput, after this we will elect three of them based on previous assessment and then compared between these three protocols in term of total drop packets and average end to end delay. |
| The paper is organized as following: |
| Attributes of five MAC layer protocols in the section (2), performance assessment and simulation in section (3) and finally, conclusion in section (4) |
ATTRIBUTES OF MAC LAYER PROTOCOLS |
| Fama: FAMA is proposed by [8], the objective of a FAMA protocol is to allow a station to acquire control of the channel (the floor) dynamically, and in such a way that no data packets ever collide with any other packet. This can be viewed as a form of dynamic reservations; however, in contrast to prior approaches to dynamic reservations, which are also called collision avoidance schemes the FAMA protocols presented do not require separate control sub-channels or preambles to reserve the channel. Instead, a FAMA protocol requires a station who wishes to send one or more packets to acquire the floor before transmitting the packet train. The floor is acquired using control packets that are multiplexed together with the data packets in the same channel in such a way that, although control packets may collide with others, data packets are always sent free of collisions. There are many different schemes with which stations can acquire the floor, and any single-channel MAC protocol that does not require a station to sense the channel while it is transmitting can be adapted to support floor acquisition for our purposes. |
| A floor acquisition strategy based on an RTS-CTS exchange is particularly attractive in the control of packet- radio networks because it provides a building block to solve the hidden-terminal problem that arises in CSMA. Within the context of using an RTS-CTS exchange for floor acquisition, there are many ways in which such control packets can be transmitted. We address only two variants in this paper. |
| a. RTS-CTS exchange with no carrier sensing. |
| b. RTS-CTS exchange with non-persistent carrier sensing. The first variant corresponds to using the ALOHA protocol for the transmission of RTS packets; the second consists of using the non-persistent CSMA protocol to transmit RTS packets. We choose to consider non-persistent carrier sensing over persistent carrier sensing, because the throughput of non-persistent CSMA is much higher under high load and only slightly lower under low load than the throughput of p-persistent CSMA. Although the original motivation for MACA was to solve the hidden-terminal problem of CSMA, the basic RTS-CTS dialogue of MACA and even a four way handshake (RTS, CTS, data, acknowledgment) does not solve all hidden- terminal problems. For example, as Figure 1 shows, given three stations S, R and H, if H is “hidden” from S (i.e., S and H cannot hear each other's transmissions) it could happen that S sends an RTS to R in the clear and R sends a CTS to S; the problem occurs when H transmits an RTS to R, or another station that can hear R and H, at the same time that R transmits its CTS to S. If that is the case, S will send data packets to R, and H may transmit an RTS that R can hear and that collides with S’s data packets. Clearly, an ad-hoc solution would be to make H wait a very long time before attempting to retransmit, but that would degrade the network throughput. The four-way handshake advocated in the IEEE 802.11 only helps to detect hidden-terminal interference after it occurs, it does not prevent it. |
| The RTS-CTS dialogue can be used as the building block to eliminate the hidden-terminal problem; however, this paper focuses only on using such a dialogue to establish a floor acquisition discipline, and focuses on single-hop networks in which no hidden terminals exist. The design of FAMA protocols for multi-hop packet-radio networks is addressed elsewhere; the basis for such protocols is the use of additional feedback from the receiver, in the form of CTSs and partial acknowledgments to packet trains. |
| Drawbacks of FAMA are the following [10]:- |
| a. It's difficult to configure FAMA protocol when a new node com in or moves out of network system. |
| b. It is difficult to implement FAMA protocol in a distributed mode. |
R-Mac: |
| The major design goals of R-MAC are energy efficiency and fairness. R-MAC schedules the transmissions of control packets and data packets to avoid data packet collision completely. The scheduling algorithms not only save energy but also solve the exposed terminal problem inherited in RTS/CTS-based protocols |
| Furthermore, the scheduling algorithms allow nodes in the network to select their own schedules, thus loosening the synchronization requirement the protocol. Additionally-MAC supports fairness. R-MAC is divided into three phases. In the initial phase (Latency Detection), nodes measure the distances to neighbors by sending some small control packets. |
| Based on the measurements, every node will randomly choose a period for its data transmission and inform others in Phase 2(Period Announcement). |
| In Phase 3(Periodic Operation), nodes cooperate with each other to schedule data transmissions to avoid collisions [9]. R-MAC is a fair MAC layer protocol. Because an intended receiver can provides equal opportunities for making reservation for all its neighbors using REV and ACK-REV packets. This protocol is good when no new node joins the network and all the nodes are static |
| The main drawback of R-MAC is that there is no technique proposed for the node which wants to change its transmission schedule, or when a node fails or a new node joins the network [11]. |
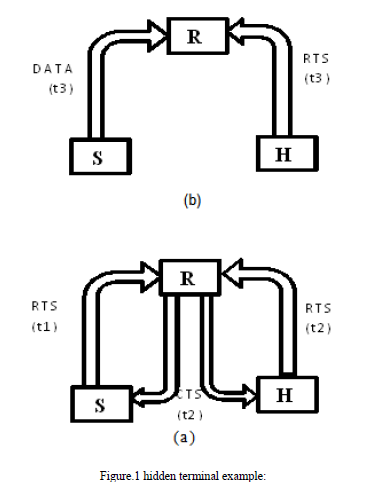 |
| The transmission from R and H collide at t2, leading to collision of S's data with H's RTS. |
Uw-Mac: |
| UWAN-MAC [32] also deploys CSMA-based MAC and has been primarily developed for high density UWSNs. Rather than bandwidth optimization, UWAN-MAC is focused on energy efficiency by introducing sleep schedules similar to its terrestrial counterparts. Each node has a sleep schedule such that each node wakes up periodically in the network to transmit its data. At the beginning of each cycle, a node broadcasts a SYNC packet indicating its period of the sleep schedule. As a result, the neighbor nodes that receive this packet wake up at the next scheduled time to listen to the node. Consequently, every node wakes up for each of its neighbors to receive data in addition to its scheduled wakeup time to transmit data. Note that since relative time information is exchanged by the SYNC packets, UWAN- MAC does not require the propagation delay to be known by each node. |
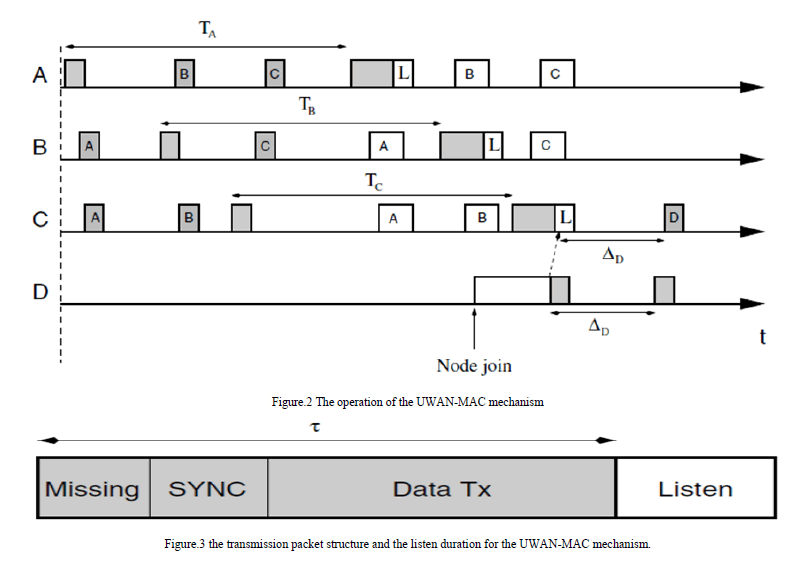
| As long as the propagation time stays constant, the information about the sleep duration of a node helps keep each node synchronized. The operation of the UWAN-MAC synchronization mechanism is shown in Fig.2 When node A broadcasts a SYNC packet, it indicates its sleep period as TA. Accordingly, when node A’s neighbors receive this SYNC packet, they schedule to wake up TA seconds after receipt of the SYNC packet. Similarly, node A also receives SYNC packets from its neighbors and schedules wakeup times for them. The data transmission packet structure of each node is shown in Fig.3, which consists of Missing, SYNC, Data Tx, and Listen periods. The SYNC period is used to broadcast SYNC packets as explained before, while Data Tx is used to transmit the DATA packets. Since each of the neighbors of node A is listening to the transmission period of the node, it can transmit its DATA without any collisions. The Missing and Listen periods are used to handle node failures/removals and node joins. At each sleep period, a node collects the list of its neighbors that it has received SYNC messages from. In case there is a change in this list (a SYNC message from a particular node is not received), the node creates a missing node list and broadcasts this information during the Missing period shown in Fig.3. This list serves as notification to the nodes in the missing list that a communication error may have occurred earlier. If a node does not hear from its neighbors in the missing list for a couple of consecutive cycles, it deletes this node from its neighbor list. On the other hand, the node that is in the missing list replies back to the sender of the SYNC message as if it is a newcomer node. The procedure for newcomer nodes is explained next. |
| The Listen period in the transmission period shown in Fig.3 is used to include newcomers to the network. This situation is illustrated in Fig.2 where node D joins the network while node C is transmitting a SYNC packet. When node D joins the network, it listens to the channel for the SYNC packets from its neighbors. When it receives a SYNC packet from node C, it replies to this packet with a HELLO packet to indicate its existence. The Listen period at the end of each transmission period ensures that node C receives this HELLO packet. Then, node C includes the newcomer node D in its list of neighbors. In the HELLO packet, node F also indicates the time left for its next wakeup time, i.e. Node C can then wake up for the scheduled wakeup time of node D and receive its SYNC packet as shown in Fig.2 Node D indicates its schedule to other nodes similarly. |
| The operation of UWAN-MAC so far assumes that the propagation delay between two nodes does not change. This enables the relative wakeup announcements by the SYNC packets to synchronize nodes. However, the underwater acoustic channel suffers from high variable propagation delays and channel fluctuations due to many reasons such as drifts of nodes, scattering objects in the water and multi-path effects. As a result, the propagation delay fluctuates randomly. In order to account for this fluctuation, UWAN-MAC introduces guard times before and after each listen duration of its neighbors. This ensures that a packet is correctly and fully received even if it arrives earlier or later than expected. A potential problem with this extension is that a node’s transmission schedule and its listen period may overlap because of the guard times. In this case, the node changes its transmission schedule and broadcasts this via a SYNC packet. |
| UWAN-MAC achieves significant energy consumption through the sleep schedules. Since it is developed for delay- tolerant applications, the sleep schedules may induce very high medium access delays for communication. Moreover, the throughput of the protocol is decreased due to the overhead in maintaining schedules and the sleep schedule operation [12]. |
 |
Aloha: |
| This protocol is based on the Aloha idea while tailored to underwater network environments: when a node has packets to send, it will send it directly without sensing the channel. The sender then will start a timer and wait for the response from the receiver. If the receiver receives the packet correctly, it will send an ACK back to the sender. If the sender receives an ACK before it times out, the sender knows that this packet has been successfully transmitted and starts to send the next packet. Otherwise, the sender will back off for some time and resend the same packet again. |
Broadcast MAC: |
| When a node has packets to send, it first senses the channel. If the channel is free, it broadcasts the packets. Otherwise, it backs off. Packets will be dropped if the number of back-off times exceeds the limit. When the receiver receives a packet, it does not need to send an ACK back to the sender. This protocol is simple yet efficient in low traffic networks. In addition, this protocol can take full advantages of the broadcast nature of the underwater acoustic channel and are suitable for geo-routing protocols such as VBF [14]. |
PERFORMANCE ASSESSMENT AND SIMULATION |
| In this section, we evaluate the performance of Broadcast MAC, Aloha, R-MAC, FAMA, and UWAN_MAC protocols. All simulations are performed using the Network Simulator (ns2) [15] with an underwater sensor network simulation package (called Aqua-Sim) extension [16]. We use the Table 1 parameters in the all simulation scenarios. In our simulations, we consider the scenario in fig.4; in this scenario at first we consider throughput and energy consumption for the five protocols. In the simulation, number of nodes are 7, which 6 nodes are sender and one nodes (sink) are receiver. Positions of each node are chosen as fig.4. Traffic is generated according to a Poisson process. Each sender node sends packets per 10 second, which can help to effectively avoid the interference between two continuous data packets. |
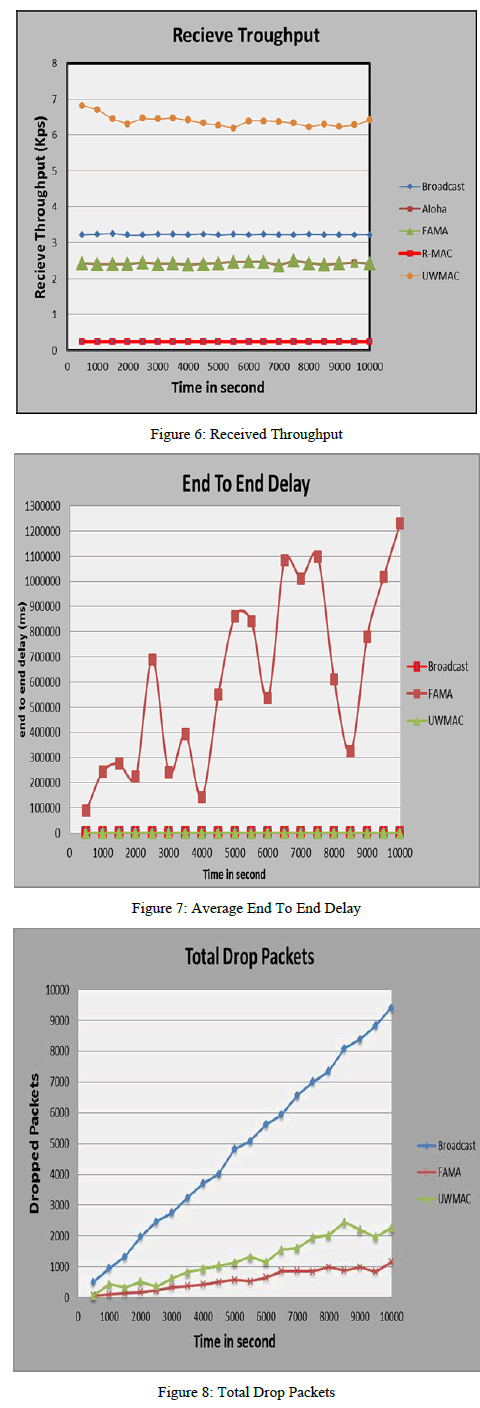
| Through Fig. 5 ,we found that the FAMA protocol is higher than the rest protocols in energy consumption because it does not consider sleep mode and rest they take into consideration, either on Fig. 6 the part of received throughput we found that the higher three protocols are UW-MAC,Broadcast and FAMA protocols. To clarify the issue more about the most appropriate protocols in terms of energy efficiency as well as the rest of the performance specifications we compared between the top three protocols in Figure 6 and compare them in terms of average end to end delay (represents the average time taken by a packet to travel from the source node to any of the sinks) and total drop packets For different times and the same scenario as shown in Fig.7 and Fig.8 respectively. |
| We found that the delay in the FAMA irregular and higher than UW_MAC and Broadcast, either in terms of total drop packets found that Broadcast protocol higher than U_MAC and FAMA protocol |
 |
 |
CONCLUSION |
| In this paper, we present a Performance assessment of five MAC protocols for underwater acoustic wireless sensor networks. We have carried assessment by using Aqua-Sim simulators and found it achieves most of the protocols parameters. We consider throughput, energy consumption, average end-to-end delay and total drop packets as our performance evaluation parameters. We found that the FAMA protocol is not suitable for UAWSN in terms of energy efficient. And the rest of the four protocols, R-MAC protocol is more energy efficient, either in terms of throughput , it better protocols are primarily UW_MAC and then Broadcast and Aloha. From these results, it has been found that the UW_MAC protocol gave 30% improvement compared with other protocols, in term of energy, throughput, total drop packets and end to end delay. We suggest that the optimum protocol to the scenario presented above is UW_MAC in term of throughput and energy efficient. And I suggest using UW-MAC protocol in our monitoring system. |
References |
|