Keywords
|
| Partial Reconfiguration, Embedded system, Reconfigurable computing, cryptography, FPGA |
INTRODUCTION
|
| Today, security becomes perplexing and grave issue especially for real time applications. Considering for cryptography algorithms full software implementation is very hefty and slows down the speed of the information exchange. From another side, full hardware implementation is very expensive in terms of area, power and can also worsen speed of information transitions. But the effective implementation of cryptographic algorithm can be done by using Dynamic Partial Reconfiguration (DPR), called as Dynamically PR implementation of a Cryptosystem. |
| Partial Reconfiguration (PR) is the process of changing a portion of reconfigurable hardware circuitry while the other part is still operating [1]. Field programmable gate arrays are frequently used as a provision to PR. Partial reconfiguration allows for critical parts of the design to continue operating while a controller will load a partial design into a reconfigurable module. Xilinx has supported partial reconfiguration for many generations of devices like high end FPGAs, Xilinx Virtex series, Spartan-II.Static Partial reconfiguration and Dynamic Partial reconfiguration are different approaches for reconfiguration. Dynamic partial reconfiguration, also known as active partial reconfiguration, allows changing a part of the device while the rest of an FPGA is still running. Partial Reconfiguration uses three different design flows like Module based, difference based, JBits. |
| This work uses Partial Reconfiguration (PR) by which FPGA can dynamically reconfigure itself under the control of embedded microprocessor like Microblaze. PR facility could help to reduce area requirements and increase systems versatility, and it could also present an optimal implementation of the AES (Advanced Encryption Standard) cryptography algorithm. The reconfigurable aspect adapts the key length which will be given like AES128, AES192, AES256 and the size of the provided information i.e. the fixed data of 128 bits, and makes all the AES blocs reconfigurable. |
| This work is organized as follows: Related work is tried to cover in section II. Section III describes the AES algorithm which is followed by the Algorithm specification in section IV which will elaborate CIPHER. Dynamic PR of AES and AES implementation is presented in section V and VI. Section VII gives results. The last section finally concludes this paper. |
RELATED WORK
|
| Wang Lie et al. has introduced in 2009 about a simple reconfigurable system and focused on the advantages of the newest dynamic partial reconfiguration design flow [2] Different researcher has mentioned about three design flows. A short paper on Module Based Implementation of Partial Reconfiguration Using VHDL on Xilinx FPGA is presented by Solomon Raju Kota et al [3, 4]. Guccione and Delon Levi explains about JBitsie. a Java-Based Interface to FPGA Hardware. How Difference-based partial reconfiguration is useful for making small on-the-fly changes to design parameters such as logic equations, filter parameters, and I/O standards and again how increases in speed and functionality of FPGA based system is presented in IJAET [5]. |
| An innovative implementation for real time audio and video processing using run time internal partial reconfiguration. System is implemented on Virtex-4 FPGA. Internal reconfiguration is handled using internal configuration access port (ICAP) driven by soft processor core. The considerable savings in device resources, bit stream size and configuration time is observed.[6] |
| Taking an optimal implementation of the AES (Advanced Encryption Standard) cryptography algorithm, many researchers have been devoted the efforts to implement cryptographic algorithm. In the implementation of the AES crypto-processor with partial reconfiguration, it modify the size of the key without stopping the normal operation of the system and hence increases the security of AES algorithm. |
| The widespread adoption of IEEE 802.11 wireless networks has brought its security paradigm under active research. One of the important research areas in this field is the realization of fast and secure implementations of cryptographic algorithms. Under this work, such an implementation has been done for Advanced Encryption Standard (AES) onfast, efficient and low power Field Programmable Gate Arrays (FPGAs) whereby computationalintensive cryptographic processes are offloaded from the main processor thus results in achieving high speed secure wireless connectivity. The dedicated resources of Spartan-3 FPGAs have been effectively utilized to develop wider logic function which minimizes the critical paths by confining logic to single Configurable Logic Block (CLB), thus improving the performance, density and power consumption of the design. The resultant design consumes only 4 Block RAMs and 487 Slices to fit both AES cores and its key scheduling.[7] |
| This work, present an experience in implementing two different cryptographic algorithms in anFPGA: IDEA and AES. Both implementations have been done by means of mixing Handel-Cand VHDLand using partial and dynamic reconfiguration in order to reach a very high performance. In both cases,obtained very satisfactory results, achieving27.948Gb/s in the IDE Algorithm and 24.922Gb/sin the AES algorithm.[8] |
AES ALGORITHM
|
| Advanced Encryption Standard called as AES is a United States encryption standard defined in Federal Information Processing Standard (FIPS) 192, published in November 2001. It was consented in May 2002 as a federal standard. It is the most recent of the four current algorithms approved for federal in the United States called as symmetric encryption algorithm processing data in block of 128 bits. Under the effect of a key, a 128-bit block is encrypted by altering it in a unique way into a new block of the same size. As same key is used for encryption and the reverse transformation, decryption AES is symmetric algorithm. The only secret needed to keep for security is the key. AES may designed to use different key-lengths, AES-128, AES-192 and AES-256. Each bonus bit in the key effectively doubles the strength of the algorithm. |
ALGORITHM SPECIFICATION
|
| For the AES algorithm, 128 bits represents the length of the input block, the state and the output block which is denoted as Nb = 4, reflects the number of 32-bit words i.e. number of columns in the State. The key length is represented by Nk = 4, 6, or 8, for 128,192 & 256 bit key which reflects the number of 32-bit words i.e. number of columns in the Cipher Key. The number of rounds which is represented as Nr to be performed during the execution of the algorithm is dependent on the key size i.e. Nr = 10 when Nk = 4, Nr = 12 when Nk = 6, and Nr = 14 when Nk = 8. This algorithm uses a round function for both its Cipher and Inverse Cipher that is composed of four different byte-oriented transformations: 1) byte substitution using a substitution table (S-box), 2) shifting rows transformation, 3) mixing the data within each column of the State array, and last one adding a Round Key to the State. |
| A. CIPHER |
| At the start of the Cipher, the input is copied to the State array and after an addition of initial Round Key, the State array is transformed by implementing a round function 10, 12, or 14 times (depending on the key length), with the last i.e. final round contrary from the first Nr -1 rounds. The final State is then copied to the output. Key schedule that consists of a one-dimensional array of four-byte words derived using the Key Expansion routine, parameterized the round function. The encryption and decryption process runs as follows in fig 1. |
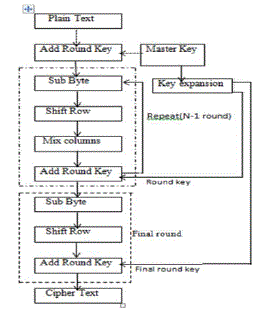
Fig. 1 AES Algorithm (Encryption) |
| Sub_Bytes_Transformation |
| The Sub_Bytes_transformation is a non-linear byte substitution that operates independently on each byte of the State using a substitution table (S-box). The S-box used in the Sub_Bytes_transformation is presented in hexadecimal form in Fig. 3. For example, if s(1,1)={53}, then the substitution value would be determined by the intersection of the row with index ‘5’ and the column with index ‘3’ in Fig. 3[9]. This would result in s’(1,1) having a value of {ed}. |
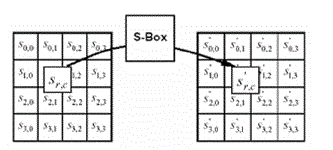
Fig. 2SubBytes() applies the S-box to each byte of the State. |
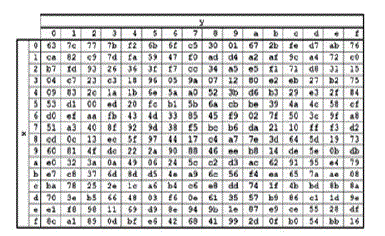
Fig. 3 Intersection of row and column |
| Shift_Rows_Transformation |
| In the Shift_Rows_transformation, last three rows bytes of the State are cyclically shifted over different numbers of bytes (offsets). The first row, r = 0, is not shifted. Specifically, the Shift_Rows_transformation proceeds as follows: This has the effect of moving bytes to “lower” positions in the row (i.e., lower values of c in a given row), while the “lowest” bytes wrap around into the “top” of the row (i.e., higher values of c in a given row).Figure below illustrates the Shift_Rows_transformation.[9] |
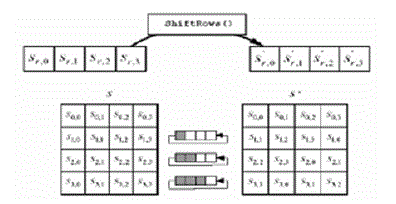
Fig. 4Shift_Rows cyclically shifts the last three rows in the State. |
| Mix_Columns_Transformation |
| The Mix_Columns_transformation works on the State column-by-column, considering each column as a four-term polynomial. The columns are reflected as polynomials overGF(28) and multiplied modulo x 4+ 1 with a fixed polynomial a(x) which is given by a(x) = {03}x 3 + {01}x 2 + {01}x + {02}.This can be written as a matrix multiplication. Let s’(x) = a(x) s(x): |
 |
| Figure below illustrates the Mix_Columns_transformation.[9] |

Fig. 5Mix_Columns operates on the State column-by-column |
| Add_RoundKey_Transformation |
| In the Add_RoundKey_transformation, by a simple bitwise XOR operation a Round Key is added to the State. Each Round Key contains Nb words from the key schedule.The action of this transformation is illustrated in Fig. below, where l = round * Nb.[9] |
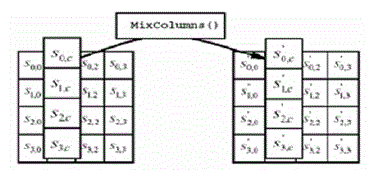
Fig. 6Add_RoundKey XORs each column of the State with a word from the key schedule. |
DYNAMIC PARTIAL RECONFIGURATION OF AES
|
| Partial Reconfiguration (PR) is the process of changing a portion of reconfigurable hardware circuitry while the other part is still operating [10]. Static Partial reconfiguration and Dynamic Partial reconfiguration are different approaches for reconfiguration. Dynamic partial reconfiguration, also known as active partial reconfiguration, allows changing a part of the device while the rest of an FPGA is still running. FPGA can reconfigure itself under the control of embedded microprocessor. This embedded processor provides intelligent control of device reconfiguration run-time. And this reconfiguration can be done with the help of internal configuration access port, control logic, a small configuration cache and an embedded processor. The embedded processor can be Xilinx Microblaze, which is a 32-bit RISC soft processor core [11].Another embedded processor named as hard-core Power PC on virtexII pro can also be used. Internal configuration access port application program interface (ICAP API) and Xilinx partial reconfiguration toolkit (XPART) provide methods for reading and modifying selected FPGA resources and support for relocatable partial bitstreams. With all these FPGA capacities AES Algorithm can be implemented as shown in block diagram given below. |
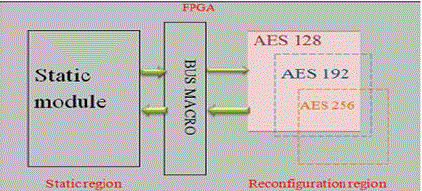
Fig. 7Block Diagram of AES Algorithm with PR |
PR IMPLEMENTATION OF AES
|
| `To increase the performance of the implemented circuit, especially cost, power and inaccessibility, all of the AES blocs may be reconfigurable [12].Following figure shows the global architecture for AES implementation. Microblaze processor computes the reconfiguration parameters using the available input and the key size as well as computes the best parameters under input constraints, and writes these parameters in the configuration register for managing the reconfiguration process. Internal configuration access port application program interface provide methods for reading and modifying selected FPGA resources. Again it supports to reconfigurable AES core. |
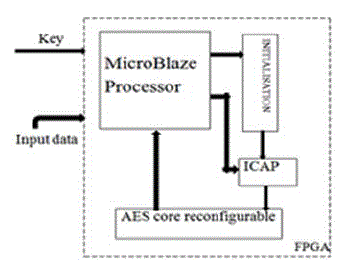
Fig. 8Global architecture for implementation the AES
|
RESULT`
|
| AES algorithm is implemented with Virtex II (XC2V500) [13] & theresults are summarized as follows: |
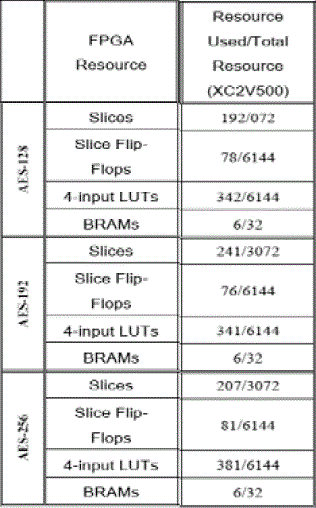 |
| TABLE II PERFORMANCE PARAMETERS |
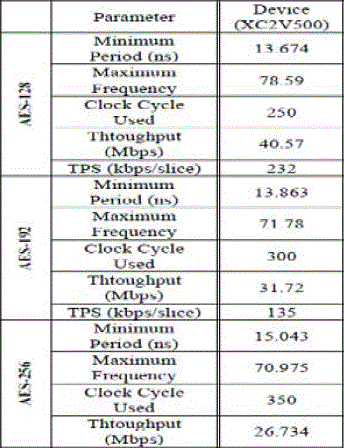 |
TABLE III DEVICE UTILIZATION SUMMARY FOR MicroBlaze system and AES
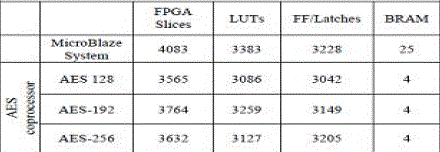 |
| With this, paper results are tried to optimize with VirtexV(XC5VLX110T).AES Encryption & Decryption work is reported in the paper. Simulated results of AES encryption and decryption are as follows: |
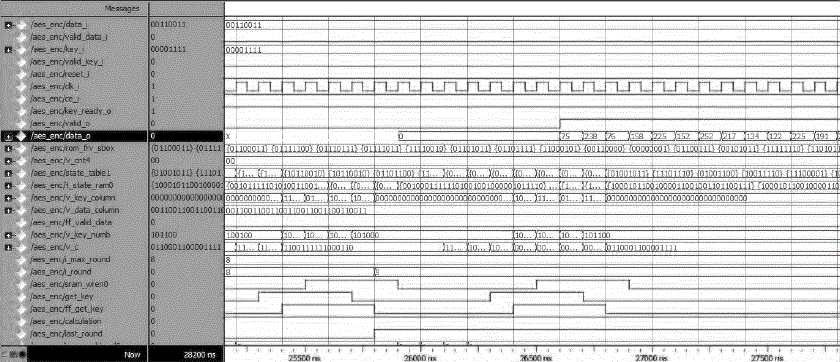
Fig. 9 Simulated result of the AES Encryption |
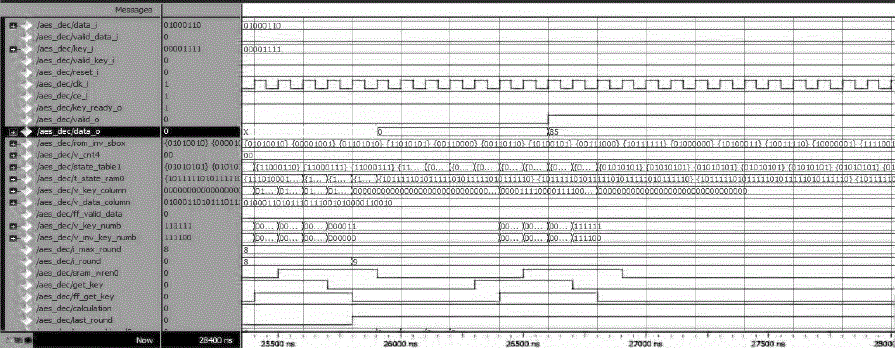
Fig. 10 Simulated result of the AES Decryption |
CONCLUSION
|
| Through this paper concept of partial reconfiguration is tried to cover. It has been observed that the idea of dynamic reconfiguration can be adapted to reduce the resources. It also reflects that PR is beneficial for reducing device count, reducing power consumption, provide more secure aspect in case of encryption methodology etc.As a part of encryption methodology AES can indeed be implemented with reasonable efficiency on an FPGA. The main advantage of this work is the facility to modify the size of the key without stopping the normal operation of the system and hence increases the security of AES algorithm. Implementation of the AES crypto-processor with this new configuration illustrates the ability of this architecture to optimize the processor occupation and the reconfiguration time. This implementation is a good solution to preserve confidentiality and accessibility to the information in the numeric communication. |
References
|
- M. Huebner, C. Schuck, M. Kuhnle, J. Becker, “New 2-Dimensional Partial Dynamic Reconfiguration Techniques for Real-time AdaptiveMicroelectronic Circuits,” Proc. Of Emerging VLSI Technologies and Architectures, Karlsruhe,Germany, Mars 2006.
- Matthew G.Parris. Optimizing Dynamic Logic Realizations For Partial Reconfiguration Of Field Programmable Gate Arrays. B.S.Universityof Louisville. 2008.
- K. Bondalapati and V. Prasanna. “Reconfigurable Computing systems,” in Proc. IEEE, vol. 90, no7, pp.1201-1217,July 2002.
- Katherine Compton and Scott Hauck, “Reconfigurable Computing: A Survey of Systems and Software,” ACM Computing Surveys, vol. 34,no. 2, pp.171-210, June 2002..
- Eric Lechner and Steven A. Guccione, "The Java Environment for Reconfigurable Computing", in Proceedings of the 7th InternationalWorkshop on Field-Programmable Logic and Applications, FPL 1997. Lecture Notes in Computer Science 1304", Wayne Luk and Peter Y. K.Cheung, eds., Springer-Verlag, Berlin, September 1997, pp. 284-293.
- Sheetal U. Bhandari, ShailaSubbaraman, ShashankPujari and RashmiMahajan“Internal dynamic partial reconfiguration for real time signalprocessing on FPGA” in Indian Journal of Science and Technology Vol. 3 No. 4 (Apr. 2010).
- “FPGA Implementation Aes For Ccm Mode Encryption Using Xilinx Spartan-Ii”, Ece-679 (2003) by K Vu, D Zier.
- Jose´ M. Granado, Miguel A. Vega-RodrÃâñ´guez, Juan M.Sa´nchez-Pe´ rez, JuanA. Go´ mez-Pulido, “IDEA and AES, two cryptographicalgorithms implemented using partial and dynamic reconfiguration” in Microelectronics Journal 40 (2009) .
- J. Daemen, V. Rijmen,“AES Proposal : Rijndael, The Rijndael Block Cipher”, AES Proposal, 1999.
- Matthew G.Parris, “Optimizing Dynamic Logic Realizations For Partial Reconfiguration Of Field Programmable Gate Arrays.” B.S.Universityof Louisville .2008.
- Xilinx, Inc., "The Programmable Logic Data Book", 1996.
- Z. A. Alaoui, A. Moussa, A. Elmourabit& K. Amechnoue “Flexible Hardware Architecture for AES Cryptography Algorithm” IEEEConference on Multimedia Computing and Systems, ouarzazate, morocco, April 2009.
- Zine El Abidine ALAOUI ISMAILI and Ahmed MOUSSA, “Self-Partial and Dynamic Reconfiguration Implementation for AES usingFPGA” , Innovative Technologies Laboratory, National School of Applied Sciences, Tangier,Morocco in IJCSI International Journal ofComputer Science Issues, Vol. 2, 2009
- A Jelbirt, I Nyip, B Chetwynd, C Paar. “An FPGA Implementation & Performance Evaluation Of The Aes Block Cipher Candidate Algorithm Finalists”
- K Vu, D Zier. “FPGA Implementation Aes For Ccm Mode Encryption Using Xilinx Spartan-Ii”, Ece-679 (2003)
- J.DaemenandV.RijmenRijndael“Rijndael:AlgorithmSpecification,http://csrc.nist.gov/encryption/aes/rijndael,(2001)
- Jose´ M. Granado, Miguel A. Vega-RodrÃâñ´guez, Juan M.Sa´nchez-Pe´ rez, JuanA. Go´ mez-Pulido, “IDEA and AES, two cryptographicalgorithms implemented using partial and dynamic reconfiguration”in Microelectronics Journal 40 (2009) .
- Jose M. Granado-Criado, Miguel A. Vega-RodrÃâñguez, Juan M. S anchez-Perez, Juan A. Gomez-Pulido, “A new methodology to implement theAES algorithm using partial and dynamic reconfiguration” in INTEGRATION, the VLSI journal43(2010)
- Samir El Adib and NaoufalRaissouni, “AES Encryption Algorithm Hardware Implementation Architecture: Resource and Execution TimeOptimization” in International Journal of Information & Network Security (IJINS) Vol.1, No.2, June 2012, National School for AppliedSciences of Tetuan, University AbdelmalekEssaadi Innovation & Telecoms Engineering Research Group. Remote Sensing & Mobile GISUnit. Mhannech II, B.P 2121 Tetuan, Morocco.
- B. Schneier , “Applied Cryptography”, John Wiley & Sons Inc., New York, USA,1996.
- M. Kandemir, W. Zhang, & M. Karakoy, “Runtime code parallelization for onchip multiprocessors”, In Proceedings of the 6th DesignAutomation and Test in Europe Conference, Munich, Germany, March, 2003.
- J. Daemen, V. Rijmen, “AES Proposal: Rijndael , The Rijndael Block Cipher”,AES Proposal, 1999.
- M. Huebner, C. Schuck, M. Kuhnle, and J. Becker, “New 2-Dimensional Partial Dynamic Reconfiguration Techniques for Real-time AdaptiveMicroelectronic Circuits,” Proc. Of Emerging VLSI Technologies and Architectures, Karlsruhe, Germany ,Mars 2006.
|