ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
| MAYANK SINGH UG Student , Dept. of ECE, Dronacharya Engineering College, Gurgaon, Haryana, India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Radio frequency identification network is becoming so popular nowadays because of its reliability and security that it provides in wireless communication betweeen RFID tag and system . RFIDs came into exisstance during II World War which which was devoloped by British and was named IFF( Identification freind and foe ) since then many modifications has been made in this technology and today this techonology has wide range of application in suplly chains , cash cards , airoplanes , animal tagging etc . RFID is one of the most commen used techonology in todays world reson being less interfarence of human being which enhaces the rate of Data computaion and decends the chances of error . As this techonogly came into existanece about 50 years ago only due to which it privides us with numerouse resarch oppurtunities as well as risk .Objective of this paper is to preset an introduction about RFID techinque and its application .
Keywords |
| Radio Frequency Identification |
INTRODUCTION |
| The RFID(fig1) is an automatic identification system were RFID stands for radio frequency identification in which a unique ID is being provided to a tag and with help of this ID detailed information about an object is retrived from database .The process of communication between tag and syatem is via radio wave due to which the process is known as radio frequecy identification . RFID was devoloped to replace bar codes as bar codes has a limitation of LINE OF SIGHT which means that the bar code is need to be placed under scanner for reading were as in case of RFID tag you need not place in some particular direction once the tag comes in the range of RFID scanner it could be scanned eassily this is the reson why it became so popular in supply chains and pharma medicos companies . RFID tag(fig 1) consists of a simple antenna , a transponder and memory chip which consists of ID information . when this transducer is exposed to elecrtomagnetic waves than it enable a special rfid reader to retrive information once RFID is verified this object profile could be retrived from Database magnagment . |
 |
WORKING OF RFID |
| A RFID operates with radio waves . Magnetic or electromagnetic fields are used for data exchange between radio frequency transponder and reader . the components of RFID are : |
| • Tag - Transponder |
| • Reader- transreciver |
| • Backed Database |
| Tag or Transponder : |
| Transponders may be either active or passive. Active transponders have an on-tag power supply (such as a battery) and actively send an RF signal for communication were as passive transponders obtain all of their power from the RF signal of the transceiver and either reflect or load modulate the transceiver’s signal for communication.It consist of an microchip for computation and storage . this chip carries a unique ID these chips are typically programed during there contact testing phase at time of fabrication and an antenna which is desinged for either magnetic feild or electromagnetc feild depending upon its application . when these Tags are exposed to feild than it provides reciever with ID with help of which data is retrieved from Database. |
| Reader or Transreciver : |
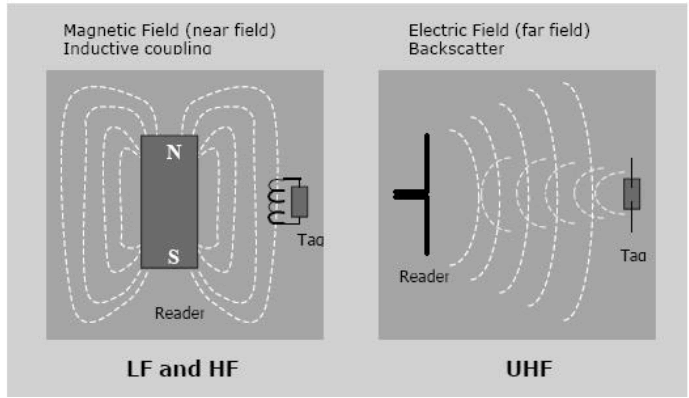
| reader consist of a RF receiver , control unit and antenna .Reader is used to provid command to Tag . Readers are basically of two types depending upon the type of frequency they uses one is Inductive Coupling and other is Backscatter Coupling |
 |
| Backed Database : |
| once the reader traces the transponder ID than connectivity is being established via ethernet which further connects the RFID to the central server which consist of predefined database .in this database the detailed information of product is stored . |
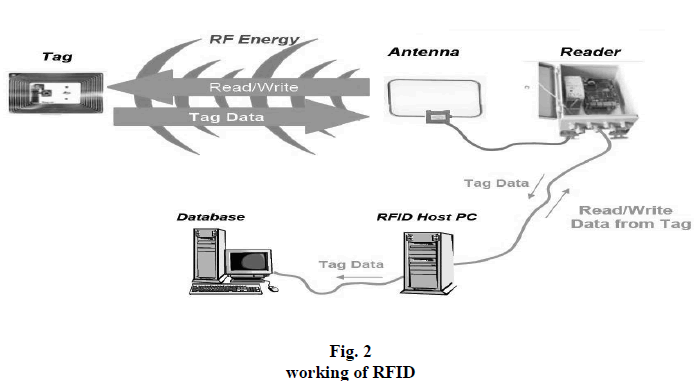
| The fuctioning of RFID could be explained as follows with help of follwing block chart . |
 |
VARIOUS FREQUENCY RFID TAGS |
| RFID tags are broadly divided into three respective frequency bands: |
| • Low frequency (30-500KHz) |
| • High frequency (10-15MHz) |
| • Ultra High Frequency (850-950MHz,2.4-2.5GHz) |
| The low frequency tags are less expensive as that of other two and these tags have least effect of fluid presence or metal but The disadvantage of these tags is therev range the have very short range in which they can respond this problem could be overcome by using High frequency range tags which are expensive as that of low frequency tags but can respond from far distance with higher transmission rate . The ultra high frequency bands have highest range of all tags . It’s range vary from 3-6 meters for passive tag and 30+meters for active tags. |
STANDARDS |
| As RFID tags being used for wide apllications so different tags are required with different specificattion for vaerious applications for this pupose we have provided various standards to these tags some of the standards are listed as follows ISO 11736, ISO 11785,ISO 14223,ISO 10536, ISO 14443, ISO 15693, ISO 18000. |
SECURITY |
| Security is one of the most crucial aspect of related to wireless communication . RFID provides many security benifits that is why is has wide application in Airlines passenger and baggage tracking and comes in range of transreciver than Keyless entry system . RFID tags contains quit essential information ,so thses tags must not compromise with privacy of holders information and this information must not be leaked to unathorised user for this purpose only we use following techniques : |
| • TAG KILLING : |
| In tag killing the privacy of consumer is protected by deactivating the tag , this process of deactivating tag is known as to "KILL" the tag . killing of atg is done before handing over the product to consumer . A killed tag is truely dead and can never be reactivated . |
| • ACTIVE JAMMING : |
| Active jaming is physical means of sheilding tag from view .The consumer could carry a device that blocks radio signals inorder to prevent the connectivity between tag and any near by RF reader source . |
| • TAG SHEILDING : |
| Here, tag is being placed in container made of metal mesh or foil ,this container do not allow RF wave to penetrate it and it blocks the connectivity between reader and tag . This cage is known as Faraday cage . |
| • HASH LOCKING : |
| In hash lock technique , tag is being locked by user by first selecting key at random , then computing hash value of key .The hashed output is designated as "MetaID" and this MetaID is stored on tag which toggles the tag into locked state . |
| The key and MetaID is stored in database. To unlock a tag, the owner first quries the MetaID from tag and uses this value to lookup into data base . The owner transmit key value to tag which hashes the received value and compair it with stored MetaID if it matches than tag unlock itself and information is made available to user. |
APPLICATION |
| RFID has wide range of application in various feilds and these applications are stated as follows |
| • IN AUTOMOTIVES : |
| Automation companies use RFID for taking there cars in order to provide them security from thiefs .A RFID tag is being palced in car and this RFID tag when it could be traced . |
| • IN SUPPLY CHAINS : |
| Some big supply chains like wallmart the uses RFID for keeping up record of there product in market and also mthesse RFID tags are being used for storing details of the product which include the product description about it's shape, size,colour ,model number , date of manufacturing etc. |
| • IN TRACKING ANIMALS : |
| RFID tags are becoming more popular in animal tracking in which a collar is placed around the neck of animal and it consistently emit a radio frequency whivh could be eassily taced via reciver . these collars consist of all information about vacine, weight, details of blood sample etc |
| • ASSET TRACKING : |
| Assets such as jwellary, watchs ,currency etc could also be tracked via RFID system in which tag is being placed in assets , and via reader we could trace the path of these assets . |
FUTURE PROSPECTIVE |
| As , RFID is new technolgy so there is vast source of resarch and development in this feild some of the projects that could be acheived in future are stated as below : |
| • “Smart” products Clothing, appliances, CDs, etc. tagged for store returns these tags contain ed detailed discription of products . |
| • Smart appliances |
| o Refrigerators that automatically create shopping lists |
| o Closets that tell you what clothes you have available, and search the Web for advice on current styles, etc. |
| • •RFID-enabled mobile phones (e.g., Nokia): |
| Scan movie poster to learn show times Scan consumer product to get price quotes |
| • Recycling : |
| this system would aotumatically seprate plastic from the waste . |
LIMITATION |
| • Till today there are no certain standerdized protocols that are being introduced related to the RFID transfer due which different countries uses different frequencies for communication between device and tag . |
| • A thief could create a duplicate tag with the same EPC number and return a forged item for an unauthorized refund. |
| • privacy is another issue as if some how the counsumer would be able to get active rfid tag then valuable information of owner could be loosed. |
CONCLUSION |
| As many reforms have been made in RFID technology but still it is feild which has many resarch and devolopments need to be made .so by this paper I just want make large popullation aware of this technology . |
References |
|