ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
G Vinay Kumar 1, R.Raju2, Santhosh Kumar 3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
An automated teller machine or automatic teller machine (ATM) is a computerized telecommunications device that provides a financial institution's customers a secure method of performing financial transactions in a public space with RFID reader and GSM. Using an ATM, customers can access their bank accounts in order to make cash withdrawals (or credit card cash advances) and check their account balances. Many ATMs also allow people to deposit cash or checks, transfer money between their bank accounts, pay bills, or purchase goods and services. The customer then verifies their identity by showing RFID tag to a reader, then a message is being send to registered user of that Account, such that “Please enter pin and amount”, after successful reception of message then the system validates for PIN number and then process the transaction, if fails then it will not process transaction and send a reply message as invalid transaction. After the transaction is complete, motor will rotate to dispatch required amount to the customer. Concerned person will receive a message through SMS via GSM regarding authentication and money transfer transactions. ATM security system using GSM Module is one of the hot topics in embedded systems industry. For providing Security at ATMs GSM Module are controlled by using Microcontroller. Probably the most useful thing to know about the global system for mobile communication is that it is an international standard. If you travel in parts of world, GSM is only type of cellular service available. Instead of analog services, GSM was developed as a digital system using technology.
Keywords |
| ARM7LPC2148, GSM Modem , RFID Reader , MAX232, Embedded c-Language, KEIL Micro vision, Flash magic. |
INTRODUCTION |
| An embedded system is a combination of software and hardware to perform a dedicated task. Some of the main devices used in embedded products are Microprocessors and Microcontrollers. Microprocessors are commonly referred to as general purpose processors as they simply accept the inputs, process it and give the output. In contrast, a microcontroller not only accepts the data as inputs but also manipulates it, interfaces the data with various devices, controls the data and thus finally gives the result. |
| RFID cards have brought a revolution in how industry takes care of large number of products. Either it has products in shopping mall, vehicles in an assembly line of a manufacturing unit or employee attendance etc., RFID card is nothing but a small electronic device either actively or passively functioned. RFID has emerged as a replacement to barcodes which are being used for the object identification so far. Unlike the barcode system, RFID has many different advantages: it can have data memory in addition to identification of data and it can also be recognized out-of-sight even from a relatively long distance. |
| These features can enable various types of application services in addition to simple identification. For example, it can be inventory management, automation of manufacturing process, shipping management, animal tracking, container recognition and ticketing service. |
| RFID is the core technology for ubiquitous computing environment implementation, together with USN (Ubiquitous Sensor Network). Currently, there is a new stream, called mobile RFID. It has a small binary coded circuit in it which on energizing either changes from 0 to 1 or vice versa. Depending on application they can manufacture the card with capacity to hold more data. The reader is device which emits EM waves continuously and these waves when touches the card reflects and carries the data back to the reader. This is present in the ATM center. |
| RFID technology is a bewitch invention which has the ability to deliver embedded information in a tag without any physical contact. On the other hand, that means RFID is vulnerable to security breaches such as cloning and clandestine tracking can even tamper the information in the tag. Problems and solution proposals related to privacy and security of RFID issues are illustrated in the survey paper. |
| To achieve a real RFID credit card holder during trending process, in 2007, proposed mobile phone based RFID architecture for secure electronic payments using RFID credit cards, which are based on the difficulty of factorization (public key cryptography, RSA).now we are using rfid tag as a credit and debit cards. Rfid tags will used as atm cards on a days.it holds the information about the account holder and details will be predefined at the time atm issued to customer and details will be stored by the banks. |
| Whenever rfid tag will place before atm center rfid reader place immediately atm machine will send sms to the user that enter respective details. |
REVIEW ON LITERATURE |
| Most of the previous works assume the communication channel between an RFID reader and its backend server is secure and concentrates only on the security enhancement between the RFID tag and RFID reader. However, once RFID reader modules gets extensively deployed in consumers' handheld devices , the privacy violation problems at reader side will become a matter of great concern for individuals and organizations. If the future |
| Communication environment for RFID systems is in wireless it increases the insecurity among the three roles. We need to achieve message security, anonymity, availability and protection of information from being stolen or tampered with. Under such infrastructure, handheld device, such as mobile phone, embedded RFID reader modules will be situated everywhere and operated with many RFID tags in various RFID application systems. In the meantime, it is more difficult to secure the privacy of a mobile RFID-enabled device with the change in consumption habits, trending practices have changed from the traditional to the entity stores patterns. They have gradually transformed into the network of online shopping Patterns, and most of online shopping is completed by the Transaction through the credit card. |
| However, with the traditional trading protocol, the credit card number and code (three digit code), can be faked by cardholders to carry out all transactions. When the card is lost, the system cannot detect the implementation of the transaction, whether it is by the legitimate credit card |
| Holder or not. Recently the use of mobile devices has become very common in the world. They have the functionality to read RFID tags and they also have higher computing performance. During transactions process they take less time for encryption, decryption and certification. RFID based smart stick prototype has been developed to aid |
| And assist the visually challenged (user) in shopping through GORE (Goal oriented Requirements Engineering Methodology). The device developed is based on Radio Frequency Identification (RFID) which operates in the Low Frequency (LF) band. The envisioned device is a combination of a RFID LF reader module and a microcontroller unit to convey all the information pertaining to the product to the user and thereby enhancing their shopping experience. |
METHODOLOGY |
| The main purpose of rfid and gsm based atm money transfer prototype system is for making of secured atm transactions by not revealing atm password to users. Account holder will send password through mobile to the gsm modem present in the architecture. The theme of this system is we use rfid tag as an atm card, first we show rfid tag to the rfid reader then it identifies the account holder information and sends a message to the predefined mobile number or customer’s mobile number. Gsm modem will send message to account holder that please enter your four digits password numbers. Now he sends his secured password to atm center number through sms.if he enters correct password then he will receive return sms as please enter your amount. If password is wrong we get return sms as please enter your correct password. If we entered more amount than available balance in our account, then we receive sms as you are having insufficient money in your account. If the transaction is Successful we receive money and dc motor will rotate in the project architecture. |
BLOCK DIAGRAM |
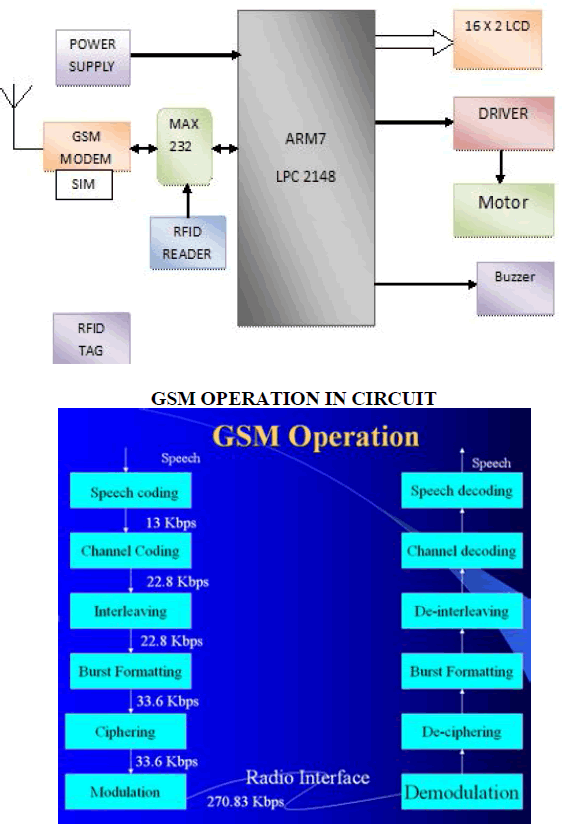 |
| A GSM modem is a specialized type of modem which accepts a SIM card, and operates over a subscription to a mobile operator, just like a mobile phone. From the mobile operator perspective, a GSM modem looks just like a mobile phone. When a GSM modem is connected to a computer, this allows the computer to use the GSM modem to communicate over the mobile network. While these GSM modems are most frequently used to provide mobile internet connectivity, many of them can also be used for sending and receiving SMS and MMS messages. |
COMPONENTS |
| RS232 CABLE: To allow compatibility among data communication equipment, an interfacing standard called RS232 is used. Since the standard was set long before the advent of the TTL logic family, its input and output voltage levels are not TTL compatible. For this reason, to connect any RS232 to a microcontroller system, voltage converters such as MAX232 are used to convert the TTL logic levels to the RS232 voltage levels and vice versa. |
| 1. Transmitter module consisting of a transmitting antenna. |
| 2. Receiver module consisting of a receiver antenna. Distance of separation between the transmitting and receiving module depends upon the type of antenna used. |
| 3. Microcontroller to get the count of the RFID tags used. 4. It has a RS232 interface to communicate with external devices |
| MAX232: Max232 IC is a specialized circuit which makes standard voltages as required by RS232 standards. This IC provides best noise rejection and very reliable against discharges and short circuits. MAX232 IC chips are commonly referred to as line drivers. To ensure data transfer between PC and microcontroller, the baud rate and voltage levels of Microcontroller and PC should be the same. The voltage levels of microcontroller are logic1 and logic 0 i.e., logic 1 is +5V and logic 0 is 0V. But for PC, RS232 voltage levels are considered and they are: logic 1 is taken as -3V to -25V and logic 0 as +3V to +25V. So, in order to equal these voltage levels, MAX232 IC is used. Thus this IC converts. RS232 voltage levels to microcontroller voltage levels and vice versa. |
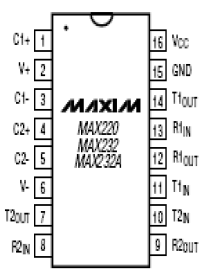 |
| Fig: Pin diagram of MAX 232 IC SCON (serial control) register: The SCON register is an 8-bit register used to program the start bit, stop bit and data bits of data framing. |
RFID: |
| Radio-frequency identification (RFID) is the use of an object (typically referred to as an RFID tag) applied to or incorporated into a product, animal, or person for the purpose of identification and tracking using radio waves. Some tags can be read from several meters away and beyond the line of sight of the reader. |
| Most RFID tags contain at least two parts. One is an integrated circuit for storing and processing information, modulating and demodulating a radio-frequency (RF) signal, and other specialized functions. The second is an antenna for receiving and transmitting the signal. |
| There are generally three types of RFID tags: active RFID tags, which contain a battery and can transmit signals autonomously, passive RFID tags, which have no battery and require an external source to provoke signal transmission, and battery assisted passive (BAP) which require an external source to wake up but have significant higher forward link capability providing great read range. |
| RFID has many applications, for example, it is used in enterprise supply chain management to improve the efficiency of inventory tracking and management In 1945 Léon Theremin invented an espionage tool for the Soviet Union which retransmitted incident radio waves with audio information. Sound waves vibrated a diaphragm which slightly altered the shape of the resonator, which modulated the reflected radio frequency |
CONCLUSION |
| This whole implementation ensures us a secured and authenticated transaction through rfid and gsm technique with lowest cost and minimum maintenance. Mankind will utilize new and secured type of money transactions. The only thing is that initial cost of RFID conversion of the entire system is the required one time investment. Account holder will utilize atm card by entering password through his predefined mobile number for bank. The value added service that this system provides increases the credibility of the financial institutions, the banks improves the convenience to its customer. Hence as the world progresses through the inevitable and an indomitable quest for knowledge, the aspect of security bound systems are bound to concede with the growing innovations and obviously more vulnerabilities. Hence our application might well solve the aspect of transaction security to a precise and great extent. |
ACKNOWLEDGEMENT |
| The authors want to heartily thank Mr. R.Raju Project Coordinator, Assistant Professor, Mr. Santosh kumar Project Guide, and Assistant Professor of ECE. Marri Laxman reddy engineering college, Jawaharlal Nehru technological university of Hyderabad For Their critique discussion and valuable suggestion. |
References |
|