ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
V.M.Prabhakaran1, Prof.S.Balamurugan2, S.Charanyaa3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
This paper proposes various sequence flow models efficiently guard Electronic Health Records (EHRs). Privacy-An important factor need to be considered while we publishing the microdata. Usually government agencies and other organization used to publish the microdata. On releasing the microdata, the sensitive information of the individuals are being disclosed. This constitutes a major problem in the government and organizational sector for releasing the microdata. In order to sector or to prevent the sensitive information, we are going to implement certain algorithms and methods. Normally there two types of information disclosures they are: Identity disclosure and Attribute disclosure. Identity disclosure occurs when an individual's linked to a particular record in the released Attribute disclosure occurs when new information about some individuals are revealed. This paper aims to discuss the existing techniques present in literature for preserving, incremental development, sequence flow model of the system proposed.
Keywords |
| Electronic Health Records(EHRs0, Privacy, Microdata, Medical Healthcare System, Database Security. |
INTRODUCTION |
| In the present world people suffer from various health problems. They frequently go to different hospitals to get guidance and get their treatments. However they also hurt from health problems they do not wish to share with anyone about their health problems and treatments. So they are in need of a new system to know about their health conditions. Cloud environment provides one such service. Cloud Computing has been intended as the next generation architecture of IT Enterprise. It moves the application software and databases to the centralized large data centres, where the management of the data and services may not be fully trustworthy. When the information is maintained in cloud it has various advantages patient no need to carry medical records where ever they go they can access from any desired place. It also minimizes the stress of the patient and the time. |
| The remainder of the paper is organized as follows. Section 2 deals about Survey of Literature of Techniques prevailing to protect EHRs. Architectural representation of the proposed system is discussed in Section 3. Section 4 discusses about the existing and proposed techniques for securing PHR. The Sequence Flow Modeling of Key Generation is discussed in Section 5. Section 6 discusses about Sequence Flow Modeling of Data Uploading Process. The Sequence Flow Modeling of Data Retrieval Process is depicted in Section 7. Section 8 discusses the Sequence Flow Modeling of Data Sharing Process. Section 9 concludes the paper and outlines the direction for Future Work. |
II. LITERATURE SURVEY |
| PekkaRuotsalainen (2004) [24] in “A cross-platform model for secure Electronic Health Record communication”. Enhanced cross security platform is proposed which support a platform for communication through the adhoc network to access the distributed electronic health records. Roger J. Quy (2005) [25] in “Method and apparatus for health and disease management combining patient data monitoring with wireless internet connectivity”. The health related data is communicated from the WWD to a server using standard internet protocols. Server calculates the response time and further it reviewed by a physician or health care provider. User and server interaction takes place the server transmits a response to the WWD and the user may answer the response. |
| Avner Amir, Avner Man (2006 a) [26] in “System and method for administration of on-line healthcare”. The end-unit device is guided by the CMIP so that anamnesis, diagnosis treatment is provided, monitored, recorded and clinically investigated. This system is useful for the management of medical records. Paul C.Tang, Joan S. Ash, David W. Bates, J. Marc overhage and Daniel Z.Sands (2006 b) presented “Personal Health Records: Definitions, Benefits, and Strategies for Overcoming Barriers to Adoption” they explore the Personal Health record (PHR) systems for patients. They carry patient data, they combine data, knowledge and software tools which help the patient to handle their medical data they handle through a standalone computer. |
| Christopher Alban, KhiangSeow (2007) [28] defines a “Clinical documentation system for use by multiple caregivers” they explain that A computer based system for recording, storing, accessing and retrieving clinical documentation where the care setting is provided. In a single electronic database it stores clinical patient notes, provides multiple points of read/write access through user interface operating on single or more client computers that are in real time communication with the repository. |
| Brian A. Rosenfeld, Michael Breslow (2008) [29] in “System and method for accounting and billing patients in a hospital environment”. Patient identifier is associated with the billing service provided by the hospitalized unit. If the billable service is provided by a specialist, a specialist identifier is also associated with the billable service. The hospitalized patient is counted and a current procedural terminology (CPT) manager assigns CPT codes to the billable service. A bill generator receives all the details of the patient data, insurance information and CPT codes which generate a bill for the billable services provided to the hospitalized patient. |
| Jacquelyn Suzanne Hunt, Joseph Siemienczuk (2009) [30] in “Process and system for enhancing medical patient care” explored that a system that abstracts selected information. A data warehouse receives the extracted information and reformats that information. Information’s are analyzed by a health care provider having that medical condition. It further collects the data of the selected patients for multiple health care providers and enables comparisons of health care provider’s success for such patients to promote advance of the treatment by less successful providers. |
| Richard J. Schuman (2010) [31] defines “Health care computer system” which define the A hospital bed, patient and nurse call system. A hospital network is provided. Communication is provided over a packet based communication network. Kanagaraj, G.Sumathi, A.C. (2011) [32] in “Proposal of an open-source Cloud computing system for exchanging medical images of a Hospital Information System” proposed clinical information system through the cloud can provide the essential details to the health care and the patient can seek the treatment in different hospital, reduce computational resource maintenance in the hospital also existing medical equipment’s can be reconstructed to be more efficient and low-cost. J. Vidhyalakshmi, J. Prassanna (2012) [35] proposed “Providing a trustable healthcare cloud using an enhanced accountability framework” explored that Security and accountability of patient’s personal health record maintenance it handle the Privacy protection problem. They define Distributed accountability framework to control and monitor user data in cloud. It also handle the object centric which automatically trigger an object to create a log record and access over distributed data. Log file corruptions are handled, log manager maintenance and verify corrupted log records. With the introduction of cloud computing in medical data capital expenditure is converted to operational expenditure. |
| Carmelo Pino and Roberto Di Salvo (2013) [36] in “A Survey of Cloud Computing Architecture and Applications in Health” explained that cloud computing act as an important alternative to ensure high performance data processing and manage the tool in easy manner. Cloud computing provide resource management and computation capabilities, hybrid cloud can increase the development of the health sector. K.S. Aswathy, G. Venifa Mini (2014 a) [37] in “Secure Alternate Viable Technique of Securely Sharing the Personal Health Records in Cloud” proposed a cloud environment for resource sharing it involves in exchange of personal health record between multiple caregivers. Encryption schemes are used to secure the data and provide a patient centric framework for sharing the personal health data. Abhishek Kumar Gupta, Kulvinder Singh Mann (2014 b) defined “Sharing of Medical Information on Cloud Platform” explored that basically hospitals store the patient details in paper format now in the migration to next level medical information are stored in cloud computing which provide a secure way to share. It results in the setting the platform for the exchange and collaboration of medical information. |
III. ARCHITECTURAL REPRESENTATION OF PROPOSED SYSTEM |
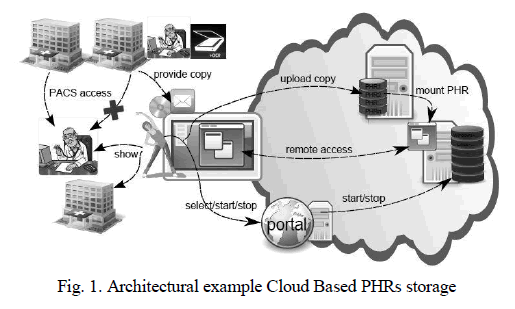
| The architectural representation of cloud based PHR storage is represented in Fig 1. The portal plays an important role in uploading copy of data, remote access maintenance, start/stop operation. PCAS access is used to provide and show copies. The cloud takes the responsibility of mounting the PHRs. |
 |
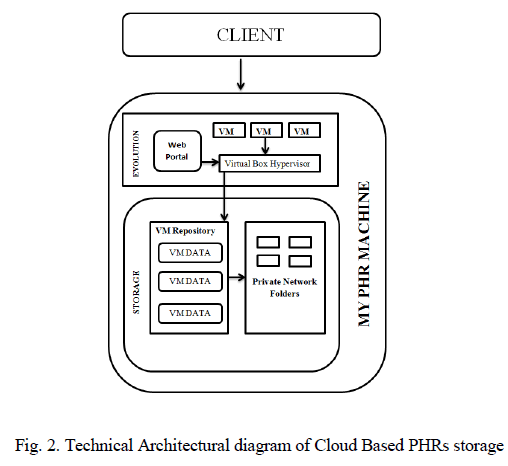
| Architectural representation of MyPHR Machine consists of two components evolution and storage with which client directly interacts with MyPHR Machine. The first component of MyPHR Machine consists of web portal which in turn interacts with Virtual Box Hypervisor. Virtual Machines are connected together with Virtual Box Hypervisor. The second component of MyPHR Machine, storage consists of VM Repository which houses VM Data and Private Network folders as indicated in Figure 2. |
 |
IV. EXISTING AND PROPOSED TECHNIQUES FOR SECURING PHR |
| Existing techniques for securing PHR are Paper based PHRs, Electronic device based PHRs and Web based PHRs[1]. PHR systems typically offer functionality to view the PHR data. PHR platforms provide no technical measures for preventing data abuse by the plug-ins that are contributed by third party software vendors. In this system access control mechanism and security issues occurred. PHRs should also be portable so as to enable easy updation and retrieval. PHR systems typically offer functionality to share, visualize and analyze PHR data. Secure lifelong management of patient medical records since data are stored in the cloud and do not have to be carried around by patients. |
V. SEQUENCE FLOW MODELING OF KEY GENERATION |
| Interaction diagrams model the behavior of use cases by describing the way groups of objects interact to complete the task. The two kinds of interaction diagrams are sequence and collaboration diagrams. Interaction diagrams are used when you want to model the behavior of several objects in a use case. They demonstrate how the objects collaborate for the behavior. Interaction diagrams do not give a in depth representation of the behavior. Sequence diagrams, collaboration diagrams, or both diagrams can be used to demonstrate the interaction of objects in a use case. Sequence diagrams generally show the sequence of events that occur. Collaboration diagrams demonstrate how objects are statically connected. |
| The sequence diagram is used primarily to show the interactions between objects in the sequential order that those interactions occur. Much like the class diagram, developers typically think sequence diagrams were meant exclusively for them. However, an organization's business staff can find sequence diagrams useful to communicate how the business currently works by showing how various business objects interact. Besides documenting an organization's current affairs, a business-level sequence diagram can be used as a requirements document to communicate requirements for a future system implementation. During the requirements phase of a project, analysts can take use cases to the next level by providing a more formal level of refinement. When that occurs, use cases are often refined into one or more sequence diagrams. An organization's technical staff can find sequence diagrams useful in documenting how a future system should behave. During the design phase, architects and developers can use the diagram to force out the system's object interactions, thus fleshing out overall system design. One of the primary uses of sequence diagrams is in the transition from requirements expressed as use cases to the next and more formal level of refinement. Use cases are often refined into one or more sequence diagrams. In addition to their use in designing new systems, sequence diagrams can be used to document how objects in an existing (call it "legacy") system currently interact. This documentation is very useful when transitioning a system to another person or organization. |
| Diagram Elements: |
| ïÃâ÷ Object. Each of the objects that participate in the processing represented in the sequence diagram is drawn across the top. Note that objects are used in this diagram while classes are used in use cases, class diagrams, and state-transition diagrams. |
| ïÃâ÷ Lifeline. A dotted line is dropped from each object in the sequence diagram. Arrows terminating on the lifeline indicate messages (commands) sent to the object. Arrows originating on the lifeline indicate messages sent from this object to another object. Time flows from top to bottom on a sequence diagram. |
| ïÃâ÷ Active. To indicate that an object is executing, i.e., it has control of the CPU, the lifeline is drawn as a thin rectangle. |
| ïÃâ÷ Message. A horizontal arrow represents a message (command) sent from one object to another. Note that parameters can be passed as part of the message and can (optionally) be noted on the diagram. |
| ïÃâ÷ Return. When one object commands another, a value is often returned. This may be a value computed by the object as a result of the command or a return code indicating whether the object completed processing the command successfully. These returned values are generally not indicated on a sequence diagram; they are simply assumed. In some instances the object may not be able to return this information immediately. In this case, the return of this information is noted on the diagram later using a dotted arrow. This indicates the flow of information was based on a previous request. |
| ïÃâ÷ Conditional. Square brackets are used to indicate a conditional, i.e., a Boolean expression that evaluates to TRUE or FALSE. The message is sent only if the expression is TRUE. |
| ïÃâ÷ Iteration. Square brackets preceded by an asterisk (*) indicate iteration. The message is sent multiple times. The expression within the brackets describes the iteration rule. |
| ïÃâ÷ Deletion. An X is used to indicate the termination (deletion) of an object. |
 |
| PHR mainly designed to focus towards achieving the availability of Health data for long term and accessing medical information anywhere and anytime and the invisibility of computing. MY PHR Machine has multiple PHR Data owners and multiple PHR users. The Data owners refer to institution or doctor who has full control over their own PHR data. They can create, manage and delete it. The users include readers and writers that may come from various aspects. MYPHR machine has a cloud server where the data store and access functionality undergoes. Users access the PHR documents through the server in order to read or write to PHR. The PHR files can be organized by their categories in a hierarchical way. Several objectivities for the User process are. |
| Fine-grained access control: It should be imposed. Different users can be authorized to initiate sets of files and access. |
| User level processing: At any time if it is required a user’s access privileges should be processed from future access in an efficient way. |
| Data access should be flexible: No need any conversion tool to process the user functionality it’s more flexible to access the data. |
| Efficiency: To support a large and volatile number of users, the system should be highly scalable and efficient. They mainly focus on the key management, user management, and computation and storage. |
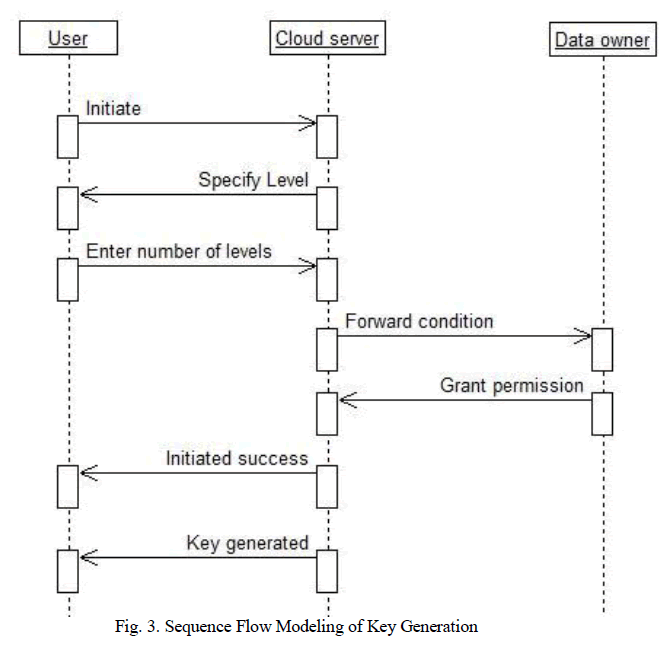
| Data owner is the one who can deliver the permission to the cloud server to provide the access function to the user if the user level is legal and authorized one. Transaction gets cancel without initiating if the user is an Illegal user. Once the initiation gets success the keys are generated by the Advanced encryption standard which has an important skill of generating the key in fast manner. Users attain attribute-based keys from their AA (Attribute Authority). They submit their legality information and obtain keys that connect them to claimed attributes. |
VI. SEQUENCE FLOW MODELING OF UPLOADING PROCESS |
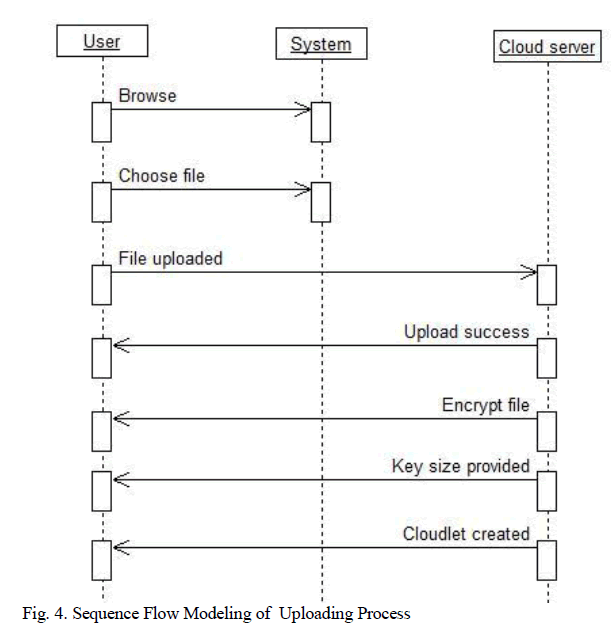
| The general process of upload function is, user through network system will login or specify the user level. The user level will be checked against login cloud data owner. System will verify that to which domain user and grant permission. Doctor who involved in monitoring and maintaining the patient details will collect all the treatment reports and prescriptions details and upload in the cloud server where the user with the assigned key or level has a permission to access the data anytime or anywhere without going to the institution. |
| Patient gets all the relevant prescriptions and guidance about the treatment. Key distribution will be again managed by Cloud server .To avoid key assignment problem will be using the concept of attribute authority (AA). File size will be specified and the cloudlet gets and stored. |
 |
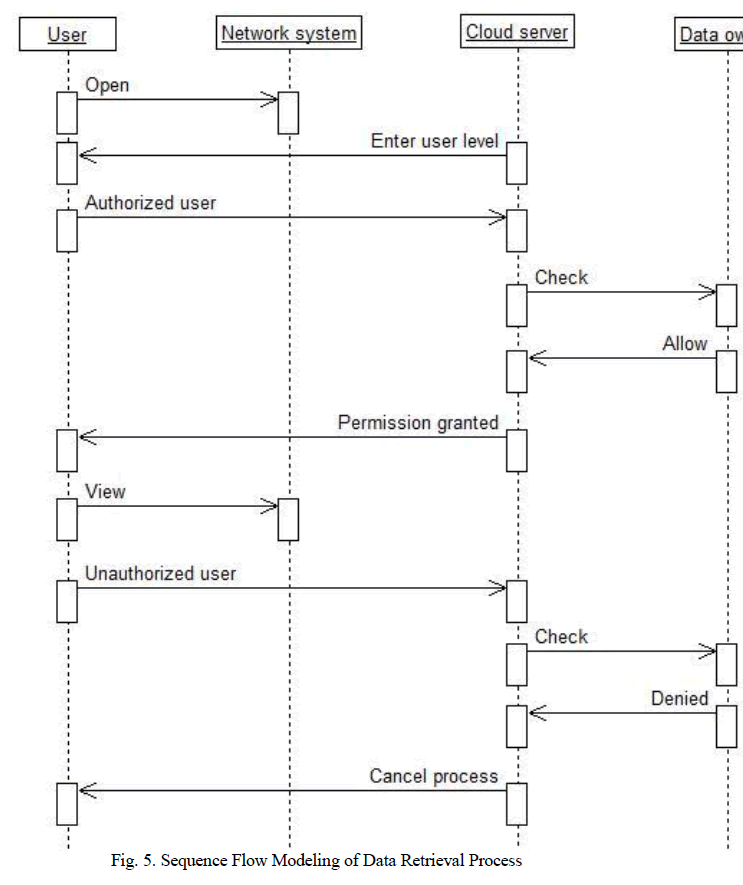
VII. SEQUENCE FLOW MODELING OF DATA RETRIEVING PROCESS |
| In retrieval process the system can be analyzed on various parameters like Security, scalability and efficiency and perform the operation. Read access and write access are been provided according to privilege provided to the user. |
| User level should be entered in correct manner to access the file where the person who is not organized will never get access to such retrieval data. Data may be monitored by the doctor who is the source person in maintaining the tight bond relationship. MYPHR system will be providing the new architecture solution for all the medical data retrieval process. |
 |
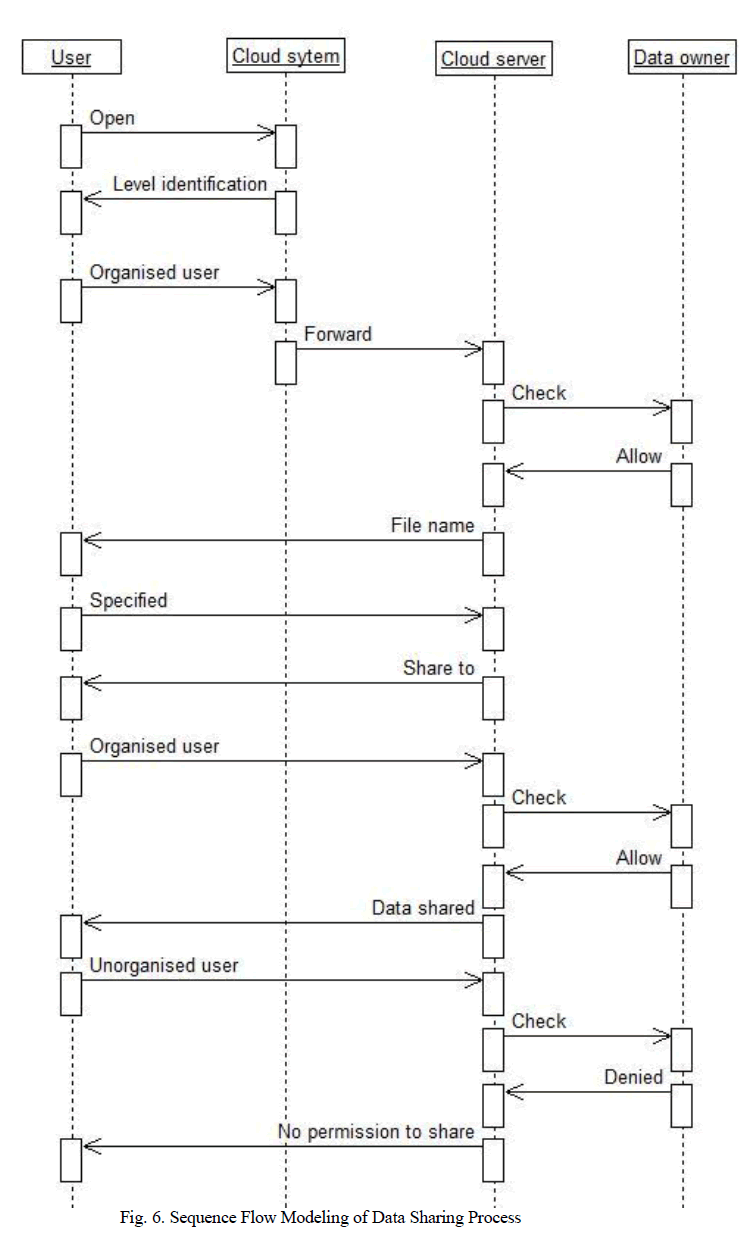
VIII. SEQUENCE FLOW MODELING OF DATA SHARING PROCESS |
| PHR data can be shared to the care provider or the institution to whom the user level permission has been granted. Share Functionality also performs level identification process. Only the initiated level use can perform the share process, if any illegal user try to access the data cloud server will not grant permission to use the data. Cloud server will check with the data owner to provide the access permission. |
 |
IX. CONCLUSION AND FUTURE WORK |
| In this paper, the issue of outsourcing of data in cloud is addressed by the method of key generation for cloud user. Cloud computing, besides providing a maximized effectiveness of shared resources, also provides an easy way of storing and retrieving data. Personal Health Records (PHRs) are designed to maintain lifelong details of patients. Automated Patient Identifier and Patient Care System is designed to count hospitalized patients based on the concept of Current Procedure Terminology (CPT) manager. Cloud storage service is accessed through the cloud computer service, web service application programming interface or by a cloud storage gateway. The cloud based workspace is centralized providing easy functionality to share. The cloud environment can provide improvements in system efficiency & density. As a part of future work, we have planned design the UML diagrams to look into the problem and to increase the clarity and to implement the uploading of encrypted medical data in cloud and in the process of creating individual cloudlets for preventing unauthorized user. |
References |
|