ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
| Isha Padiya1, VinodManure2, Ashok Vidhate2 Assistant Professor, Dept. of E&TC, SMSMPITR, Akluj, Maharashtra, India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Visual Cryptography is an encryption technique where a secret image is cryptographically encoded into n meaningless share images. A basic model for visual cryptography for natural images was proposed by Naor and Shamir. Security has gained a lot of importance as information technology is widely used. Cryptography refers to the study of mathematical techniques and related aspects of Information Security like data confidentiality, data Integrity, and of data authentication. Visual cryptography is a process where a secret image is encrypted into shares which refuse to divulge information about the original secret image. Its strength is a fact that the decryption of the secret image is through human visual system without computation. This paper provides a formulation of encryption for multiple secret images, which is a generalization of the existing ones, and also a general method of constructing visual secret sharing schemes encrypting multiple secret images.
Keywords |
| Visual Secret Sharing (VSS), Visual Cryptography (VC), Information-theoretic security, multiple secret images, image processing. |
INTRODUCTION |
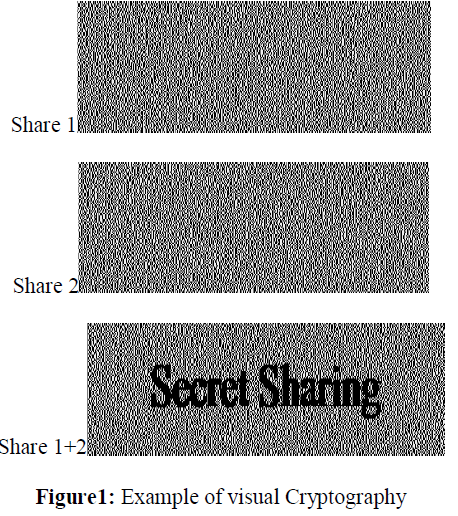
| VISUAL cryptography (VC), which was proposed by Naor and Shamir, allows the encryption of secret information in the image form [1]. With the network is more and more popular, the hackers utilize leak of the Internet to steal information that they want. Therefore, secure data transmitting becomes very important. In the recent years, generally using the traditional cryptology to avoid the data to be altered, but it needs complex computation to decode. In order to reduce the computation and furthermore secure the data, Naor and Shamir [1] proposed a new cryptology called visual cryptography in 1994. Without huge calculation, it can restore encrypted messages by stacking two shares via human visual system to identify. The first visual cryptography scheme is used for the black-and-white image in disorder to embed the confidential message. These disordered images are called “shares” that one of them may regard as the cipher text and the other treats as the key. Hackers cannot decrypt the secret message from one share. As shown in fig.1.Later on this theory, visual cryptography can extend as (k, n) – threshold visual secret sharing scheme that divides n transparencies into secretinformation. When be decoded, the owner must have k ormore shares to stack. In 1998, Chen and Wu proposed a new visual cryptography scheme. It improves the drawback of the conventional visual cryptography that two share images only can embed. |
| In a k-out-of-n scheme of VC, a secret binary image is cryptographically encoded into n shares of random binary patterns. The n shares are Xeroxed onto n transparencies, respectively, and distributed among n participants, one for each participant. No participant knows the share given to another participant. Any k or more participants can visually reveal the secret image by superimposing any k transparencies together. The secret cannot be decoded by any k-1 or fewer participants [4].There are many algorithms to encrypt the image in another image, but a few of them have been in visual cryptography for colour image. |
| In this paper, the different approach have been produced for the visual cryptography for colour image, the proposed algorithm splits a secret image into two shares based on three primitive colour components. |
 |
VISUAL CRYPTOGRYPHY MODEL |
| A printed page of cipher text and a printed transparency (which serve as a secret key). The original clear text is revealed by placing the transparency with the key over the page with the cipher, even though each one of them is indistinguishable from random noise. The model for visual secret sharing is as follows in fig.2. There is a secret picture to be shared among n participants. The picture is divided into n transparencies (shares) such that if any m transparencies are placed together, the picture becomes visible. If fewer than m transparencies are placed together, nothing can be seen. Such a scheme is constructed by viewing the secret picture as a set of black and white pixels and handling each pixel separately [5]. |
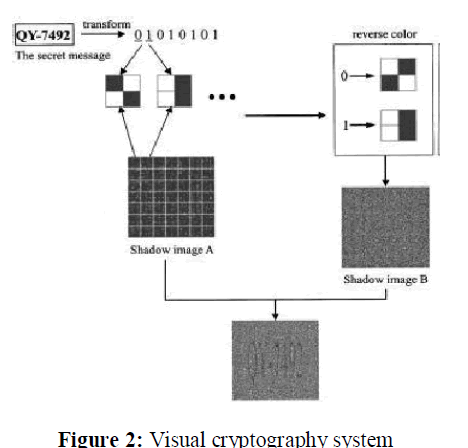 |
| In visual cryptography system the pixels of the image to be encrypted can be applied to the image in different manner. There is a set of n participants (image), and the secret image is divided and encoded into n shadow images called shares. Each participant is encrypted by one share, k out of n participants are needed to combine shares and see secret image, sometime k-1 of shares can not reveal information about secret image. The technology makes use of the human vision system to perform the OR logical operation on the superimposed pixels of the shares. When the pixels are small enough and packed in high density, the human vision system will average out the colors of surrounding pixels and produce a smoothed mental image in a human’s mind [6]. |
LITEARTURE SURVEY |
A. Black And White Visual Cryptography Scheme: |
| The visual cryptography scheme is used for encrypting the information. Visual cryptography is a one of the technique of encryption which is used to hide the information in an image; decryption can be done by human visual system. By using only this type of cryptography, no one is able reuse the data. The image which we can recover after decryption will not be same as original image so it cannot be reused. There are number of visual cryptography schemes in existence. Some of them are described below. |
| 1) Sharing Single Secret Image: In this type of visual cryptography scheme, the secret image is divided into exactly two shares. This is the simplest kind of visual cryptography. The major application of this scheme is found with remote voting system that uses 2 out of 2 secret sharing schemes for authentication purpose. To reveal the original image, these two shares are required to be stacked together. Naor and Shamir’s proposed encoding scheme to share a binary image into two shares i.e. Share1 and Share2. If pixel is white one of the above two rows of table from fig 2 is chosen to generate Share1 and Share2, likewise If pixel is black one of the below two rows table of fig 2 is chosen to generate Share1 and Share2. Here each share of pixel p is encoded into two white and two black pixels. Each share alone gives no hint about the pixel p. That is share is not provide any information whether it is white or black. Secret image is shown only when both shares of images are overlaid or superimposed. Wen-Pinn Fang suggested non pixel expansion scheme in which the pixel expansion was minimal. These all schemes have their own disadvantages |
| 2) Sharing Multiple Secret Images:Wu and Chen [10] were first researchers to present the visual cryptography schemes to share two secret images in two shares. He hidden two secret binary images into two random shares, that is A and B, such that the first secret can be seen by stacking the two shares, denoted by A⊗ B, and the second secret can be obtained by first rotating A Ãâè anti-clockwise. They designed the rotation angle Ãâè to be 90âÃâæ. However, it is easy to obtain that Ãâè can be 180âÃâæ or 270âÃâæ. To overcome the angle restriction of Wu and Chen’s scheme [10].Wu and Chang also refined the idea of Wu and Chen [10] by encoding shares to be circles so that the restrictions to the rotating angles (Ãâè = 90âÃâæ, 180âÃâæ or 270âÃâæ) can be removed. |
| S J Shyuwere first researchers to advise the multiple secrets sharing in visual cryptography. This scheme encodes a set of n≥2 secrets into two circle shares. In this the n secret image can be obtained one by one by loading the first share and the rotated second shares with n different rotation angles. For encoding purpose unlimited shapes of image and to remove the limitation of transparencies to be circular, Fang [4] offered reversible visual cryptography scheme. In this scheme two secret images which are encoded into two shares; one secret image appears with just stacking two shares and the other secret image appears with stack two shares after reversing one of them. Jen-Bang Feng [8] developed a visual secret sharing scheme for hiding multiple secret images into two shares. This scheme analyses the secret pixels and the corresponding share blocks to construct a stacking relationship graph. In this the vertices denote the share blocks and the edges denote two blocks stacked together at the desired decryption angle. By using this graph and the pre-defined visual pattern set, two shares are generated. To provide more randomness for generating the shares Mustafa Ulutas advised secret sharing scheme based on the rotation of shares. In this scheme shares are of rectangular shape and they are created in a fully random manner. |
B. Colour Visual Cryptography Schemes |
| Until the year 1997 visual cryptography schemes were applied to only black and white images. First colour visual cryptography scheme was developed by Verheul and Van Tilborg. Colour secret images can be shared with the concept of arcs to construct a colour VCS. In colour VCS one pixel is converted into m sub pixels, and each sub pixel is further divided into c colour regions. In each sub pixel, there is exactly one colour region is colour, and other colour regions are black. The colour of one pixel depends on the interrelations between the stacked sub pixels. For a coloured visual cryptography scheme with c colures, the pixel expansion m is c× 3. Yang and Laih improved the pixel expansion to c × 2 of Verheul and Van Tilborg. But in both of these schemes share generated were random. To share true-colour images Lukac and Plataniotis developed bit-level based scheme by operating directly on S-bit planes of a secret image. |
| 1) To hide a colour secret image into multiple colour images it is desired that the generated camouflage images contain less noise. For this purpose R. Youmaran et al invented an improved visual cryptography scheme for hiding a colour image into multiple colour cover images. This scheme provides improvement in the signal to noise ratio of the camouflage images by producing images with similar quality to the originals. By considering colour image transmission over bandwidth constraint channels a cost effective visual cryptography scheme was invented by Mohsen Heidarinejad et al. This scheme offers a perfect reconstruction while producing shares with size smaller than the size of input image using maximum separable distance. This scheme provides pixel expansion less than one. Haibo Zhang et al presented a multi-pixel encoding which can encode a variable number of pixels for each run to improve the speed of encoding. F. Liu [6] developed a colour visual cryptography scheme under the visual cryptography model of Naor and Shamir with no pixel expansion. In this scheme the pixel expansion is not increasing the number of colours of a recovered secret image is increased. |
| 2) Visual Cryptography technique is used to protect image-based secret information. In this scheme we have proposed a technique called random sequence to divide an image into n number of shares. The shares are sent through different communication channels from sender to receiver so that the probability of getting sufficient shares by the intruder minimizes but the distorted shares may arise suspicion to the hacker’s mind that some secret information is passed. The original image can be encrypted using a key to provide more security to this scheme. The key may be a text or a small image. Steganography can be used by enveloping the secret shares within apparently innocent covers of digital picture. This technique is more effective in providing security from illicit attacks. |
| 3) In this proposed idea comes from the fact that VSS schemes need no computation in decryption and the generic idea behind the proposed system is to introduce security to a weakly secure visual secret sharing scheme. That is, it is possible to assume in VSS schemes that we do not have (or it is a bother to use) computers in decryption. In such a scenario, it may be difficult to analyse every share exhaustively without computers, for instance, we would not investigate combinations and/or statistical data of pixels in shares. Based on this observation, we can relax the unconditional security notion of (k ,n) -threshold VSS schemes to a weaker notion in such a way that it is secure if the image obtained by stacking k-1 or fewer shares seems to be a random dot image. We say that such VSS schemes are weakly secure VSS schemes, or simply WS-VSS schemes hereafter. On the other hand, we abbreviate the unconditionally secure VSS scheme as US-VSS schemes in this paper. We note here that, in several previous studies on VSS schemes for black–white binary secret images, the weak security notion discussed above was implicitly used without sufficient security mechanisms in their constructions of US-VSS schemes. |
 |
PROPOSED ALGORITHM |
| Step1: Secret color image. |
 |
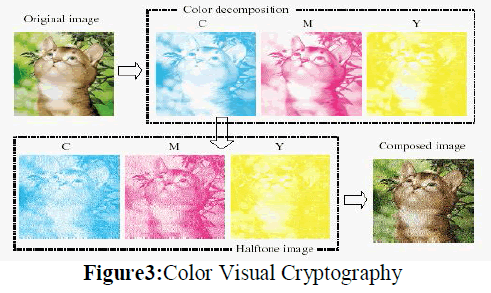
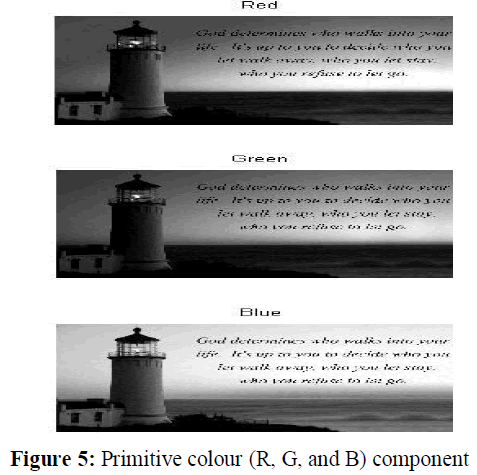
| Step2: The secret colour image as shown in Fig.3 is decomposed into three planes namely, red, green, blue, RGB. Fig.4 shows the three primitive colour components of secret colour image, where each image has 256 levels of the corresponding primitive colour, and each pixel represented by 24 bits. |
 |
| Step3: Encrypt the colour space |
 |
| Step5: Two shares will be generated by the following method. |
| Method: |
| 1. Read the pixel value with respect to ii (number of rows of secret image) and jj (number of columns of secret image). sij = I(ii,jj); |
| 2. Pixel reversal. |
| sij1 = 255-sij; |
| 3. Read each pixel and convert to shares. |
| 4. Reduce sij. |
| 5. Pixel reversal. |
| 6. Take difference of two random generator with original pixel. |
| 7. Pixel reversal. |
 |
| Step 6: After mixing share1 and share 2 with three planes of RGB we obtain decrypted image. |
 |
| Step7: Size of the decrypted image is same as secret image. |
CONCLUSION |
| Visual cryptography exploits human eyes to decrypt secret image with no computation required. As we are divide the input into multiple visual encrypted parts. The given input image can be divided into secret sharing parts which can be used in future for Encryption. We would be using genetic algorithm for implementation of this Encryption technique. Paper suggests VSS, but we would be developing as it is a better and more robust algorithm for image encryption. This paper exploits the techniques of Halftone technology. The proposed scheme revealed good security due its randomness. |
References |
|