ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Ms T.SREELEKHA1, Dr M. DHAMODHAR REDDY2, Dr T. RAMASHRI3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
This paper proposes robust hybrid watermarking scheme for grey scale images using block processing method. The proposed watermarking technique developed using combination of various transforms such as Discrete Cosine Transform (DCT), Singular Value Decomposition (SVD), Discrete Sine Transform (DST),Fast Fourier Transform(FFT) and edge detection technique. Pixel values of the blocks are modified based on the threshold value determined from edge detection. Later on from the modified block, the singular values using SVD are chosen. Using singular values watermark is embedded. Reverse process is used to extract watermark image from the watermarked image Evaluation metrics used to analyze the experimental results are Correlation (CORR) &Peak Signal to Noise Ratio (PSNR).Proposed work will be suitable to applications such as copyright protection and Copy control.
Keywords |
| Watermarking Algorithm, DCT, SVD, DST, FFT, watermark, copy right protection, CORR and PSNR. |
INTRODUCTION |
| Digital watermarking is a branch of information hiding which is used to multimedia, copyright protection However, today; there is no evidence that watermarking techniques can achieve the ultimate goal to extract the right information from the received data. There are many solutions that have been proposed like Cryptography, Steganography and Watermarking [1, 2]. The embedded watermark should not degrade the quality of the image and should be perceptually invisible to maintain its protective secrecy [3]. The watermark is embedded in magnitudes of the Fourier transform. A peak signal-to-noise ratio is used to evaluate quality degradation. applications [4]. In the frequency domain schemes, the watermark is embedded with the transformed coefficients of original image. It is more robust than spatial domain, less control of perceptual quality and mainly suits for copyright application [5,6]. The robustness and perceptual quality of the watermarking schemes mainly depends on how much percentage of the watermark is embedded into host image i.e., scaling factor [3]. |
| The main impediments of DFT&DST, SVD based watermarking schemes are as follows: 1.They are generated strong signals to rotation, scaling, translating.2.False positive Problem: when a specific watermark is detected from substance in which a different watermark was embedded, causing an hazy situation, [7, 8]. 3. Diagonal Line Problem: If we modify the singular values of the cover image directly with the watermark image then there will be a diagonal line in the reconstructed watermark from the attacked watermarked images [9]. The discrete cosine transform (DCT) represents an image as a sum of sinusoids of varying magnitudes and frequencies. The DCT has special property of energy compaction. In this paper embedding the watermark into the host image using DCT domain of DST and FFT coefficients. Hence we can achieve better performance when compared to using DCT alone [11]. Proposed work will be suitable to applications such as copyright protection and Copy control [12]. |
PROPOSED SYSTEM |
| The proposed algorithm is modified method of T.Ramashri et al method [3] method. The proposed Watermarking scheme is implemented in two phases first watermarking and then extraction. By adding DST and FFT the proposed method is more robust over [3] method. In the proposed method initially the DCT is applied to the original or host image to which watermark is going to be embedded. |
| To the host image edge detection technique is applied and divided into blocks, and then DST is applied to the blocks from which sub bands of the FFT edge image are obtained. Pixel values of the blocks are modified based on the threshold value determined from edge detection. Later on from the modified block, the singular values are selected using SVD. Then the watermarking step is performed by embedding the watermark to get the watermarked image.Figure.1 shows the block diagram of watermark embedding procedure. From the block diagram watermark size is taken 64x64 size. The watermark logo is divided into same block size of that host image block size. Blocks are selected based on the threshold value using DST, FFT of edge detection technique. Combine the HF co-efficient of DCT of host image on selected blocks. Singular values are selected on that blocks. |
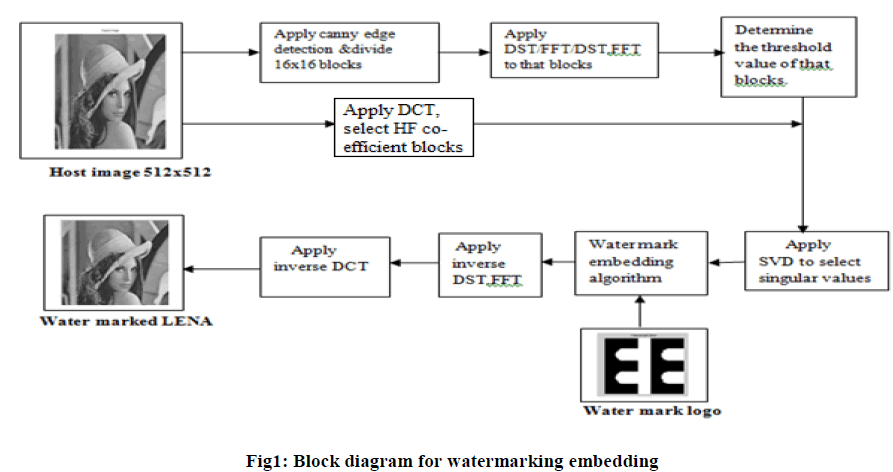 |
| The robustness of the algorithm is tested using various attacks.. Then the watermark is extracted using revere procedure. Figure.2 shows the block diagram of watermark extraction procedure from watermarked image. |
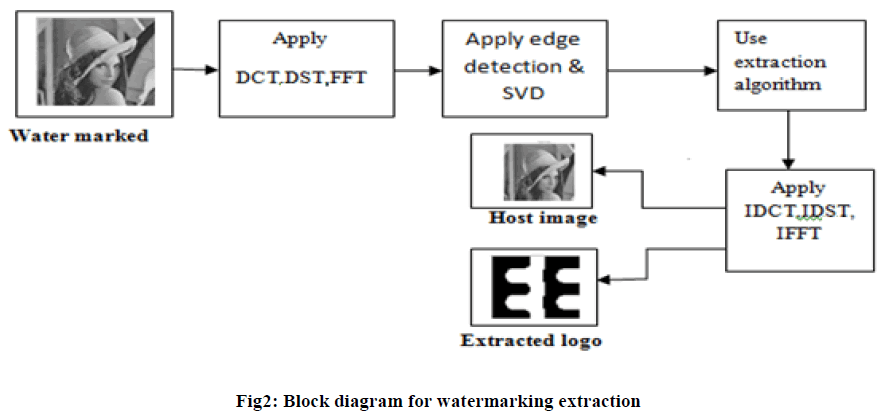 |
| From the block diagram 2 apply DCT, DST and FFT to the watermarked image. Apply edge detection to select the singular values, and extraction algorithm is used extract the water mark image from the watermarked image. Finally PSNR values are determined between original image and watermarked image. CORR values are determined between the watermark and extracted watermark. And also watermark extracted from the various attacks, PSNR and CORR values are determined those images. |
ALGORITHAMS FOR PROPOSED METHOD |
A. Watermark Embedding: |
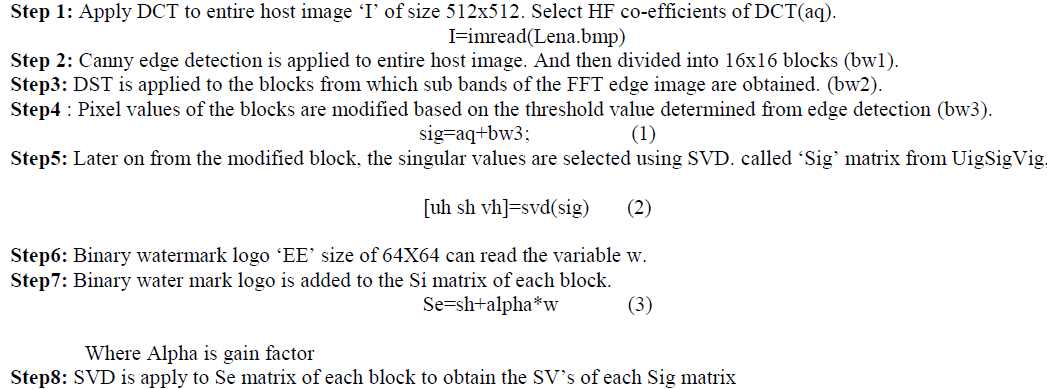 |
 |
B. Watermark Extraction: |
 |
EXPERIMENTAL RESULTS |
| In this proposed watermarking algorithm host image Lena of the size 512x512 is used as shown in figure3. For testing purpose gray scaled (BMP format) image is used. The watermark logo is „EEâÃâ¬ÃŸ of size 64X64 shown in fig.4. |
 |
| DCT is applied to entire host image. Using DST, FFT of canny edge detection the blocks are found which have more number of high frequency components. SVD is applied to the modified blocks. Singular values of the selected blocks modified using binary watermark logo and gain factor „alphaâÃâ¬ÃŸ. Fig.5 and 6shows the water marked image and extracted water mark logo respectively. The proposed watermarking algorithm is simulated using MATLAB 7.01. |
 |
| Proposed watermarking algorithm is tested for various host and watermarked images. here results are given Lena image only. |
| To evaluate the performance of the proposed method, evaluation metrics used are PSNR (peak signal to noise ratio) and CORR (correlation coefficient). PSNR is widely used to measure visual quality between the original image and watermarked image. PSNR is defined by the equation 7. Similarly the original watermark and extracted watermark from the attacked image is evaluated by using correlation coefficient given by the equation 9. |
| For robustness inspection of the scheme the watermarked image was tested against several types of attacks namely Histogram equalization, salt and pepper noise, Gaussian noise, Rotate-45, Best contrast, gauss ion blurring , image resizing, cropping compression. The quality of the watermarked image can be I estimated using peak-signal-to-noise ratio (PSNR) and is calculated |
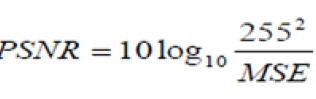 |
| Where MSE represents the mean square error and is given by |
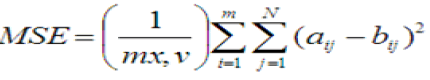 |
| Where „aâÃâ¬ÃŸ and „bâÃâ¬ÃŸ are original and watermarked images. The similarities between the original image, W and extracted watermarks, eW can be determined by using the normalized correlation coefficient (NC) and it is defined as follows: |
 |
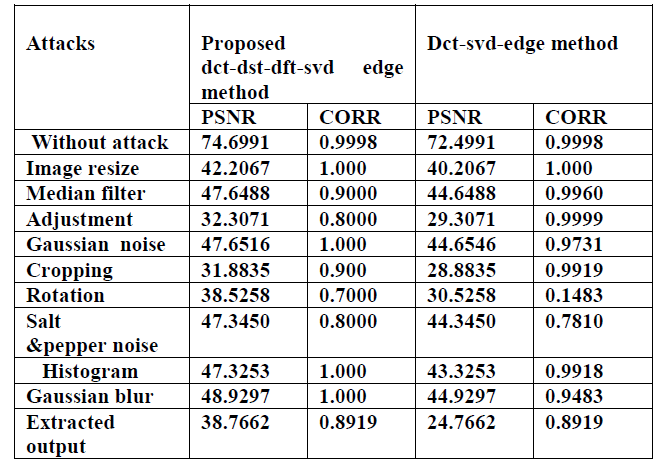
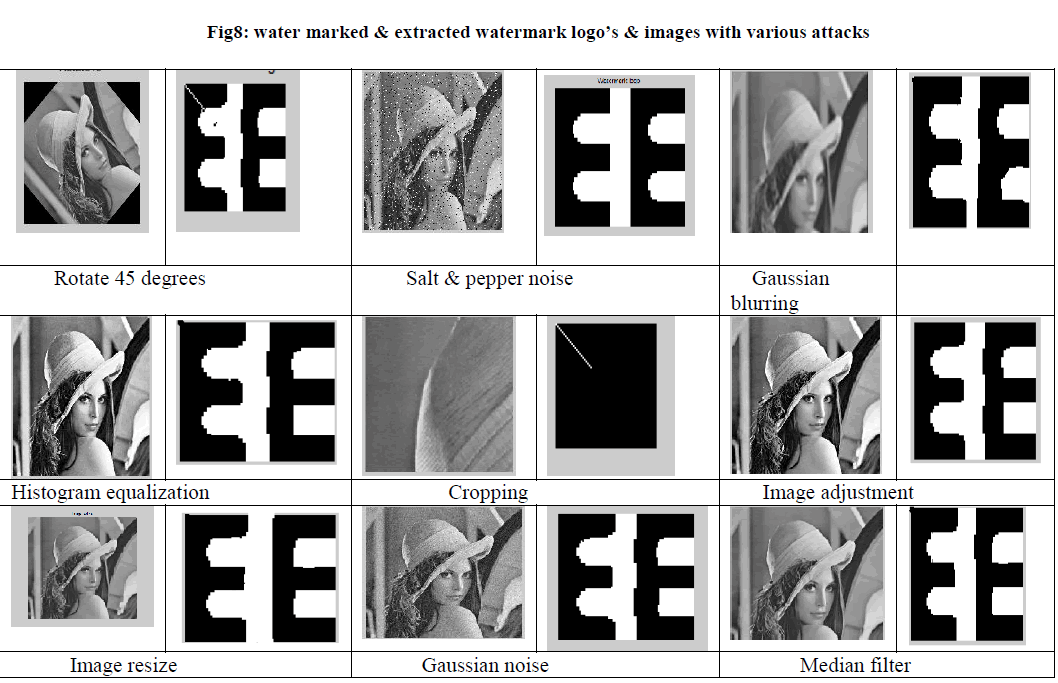
| The following figures (fig.8) represent the attacks of the watermarked images and its extracted watermark logoâÃâ¬ÃŸs of that watermarked images for proposed scheme. The different values of PSNR & CORR values of various attacks of the watermarked images are listed in Table 1. |
| Table .1: Performance results for different combinations of transform in terms of PSNR and CORR values |
 |
 |
| Table 1 is observed that the proposed watermarking algorithm is more robust then the existing method. The evaluated PSNR value limited up to 20-30dB along with diagonal line problems or false positive problems. By embedding the principle components of the watermark into the DCT of host image and Sub bands of FFT of edge detection technique& SVD blocks of the image provides better imperceptibility as well as reliability in the quality and recovery of image. By implementing, can avoid the false positive problem and hence provides the copyright protection. From the extracted watermark Have been proved there improved correlation values for Rotating, translating, Scaling and less false detection problems .And also achieved the suitable scaling factor for any watermark which is image dependent. Hence the robustness and transparency of the scheme for any watermarking can be processed. |
| The performance of the proposed method is tested by applying DCT and DST, FFT sub band technique. And image processing attacks like Histogram equalization, Gaussian noise, Rotate-45, Best contrast, Salt & Pepper noise, Adjustment, cropping, Gaussian blurring, Median filter and resize etc. and has got the values of CORR are all above 0.7 which are acceptable. Thus proposed method is robust as well as reliable watermarking technique. The scheme has been tested with success on various test images on a MATLAB simulation platform. |
CONCLUSION |
| The proposed watermarking algorithm is a non-blind robust watermarking algorithm. The proposed watermarking algorithm using DCT, DST sub bands of FFT, SVD and Edge detection is more robust in comparison with many watermarking algorithms developed using DCT and SVD methods. The watermark is inserted in few of selected blocks of original image, so that perceptual quality of the watermarked image is good. Watermark is inserted into the blocks number of times so retrieval of watermark is good. From the experimental results it is observed that the proposed watermarking algorithm is robust against too many signal processing and geometrical attacks compared to existing DCT and SVD, EDGE method. The visual quality of extracted watermark image is good. Proposed algorithm can be further improved using different transforms like Walsh transform, Hartley transform Kekre transform various edge detection techniques and further can be extended to color images and video processing. |
References |
|